Configuring Cluster-Aware Updating in Server 2012
This is a cool feature in Windows server 2012 and I’ve been dying to write about it. OK, let me tell you what actually happens. Until now, when you wanted to update your cluster nodes, first you needed to migrate cluster roles from the active node to a passive one. Then download the updates, install those updates, reboot the server a couple of times, and migrate the roles back to the preferred node. You then had to repeat this steps for the rest of the nodes in the cluster. This could easily take you the all day to patch a bunch of servers. With this new feature available in Windows server 2012 called Cluster-Aware Updating, all those tasks are automated. All you have to do is start the cluster patching and your done. O yeahh, you don’t even have to start the patching by hand, you can schedule it to run automatically.
You can patch those nodes in the cluster from the Microsoft Update service or from a WSUS server. As you might guess by now, for this lab I’m going to use a WSUS server. Now, I presume you already have a Windows Cluster created, and a WSUS server up and running. Hyper-V is installed on all nodes in the cluster and a VM is running on the Hyper-V Cluster, just to have something to migrate during the patching process.
Before we start some Active Directory stuff need to done, like moving the nodes on a separate OU so its easier with the WSUS policy. This is not a prerequisite, you can leave the servers (cluster nodes) on the OU they are right now and apply GPO filtering, but in this case I will move them in a separate one just to be more organized.
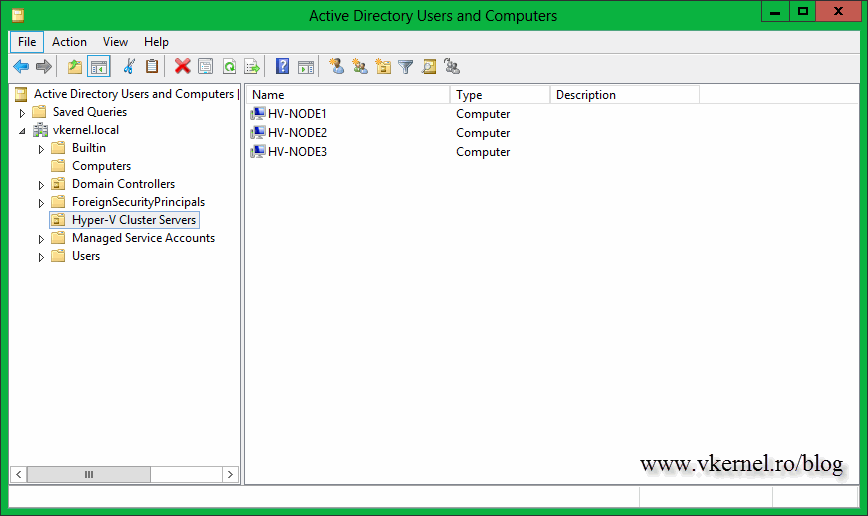
I just want to mention that all the operations are done remotely from the domain controller. You can use your technician workstation if you want to, all you have to do is install the Microsoft Remote Server Administration Tools then follow this article on how to control 2012 servers from a remote workstation/server.
Now open the GPO Editor and create a new policy that links to this OU, then right-click the policy and choose Edit.
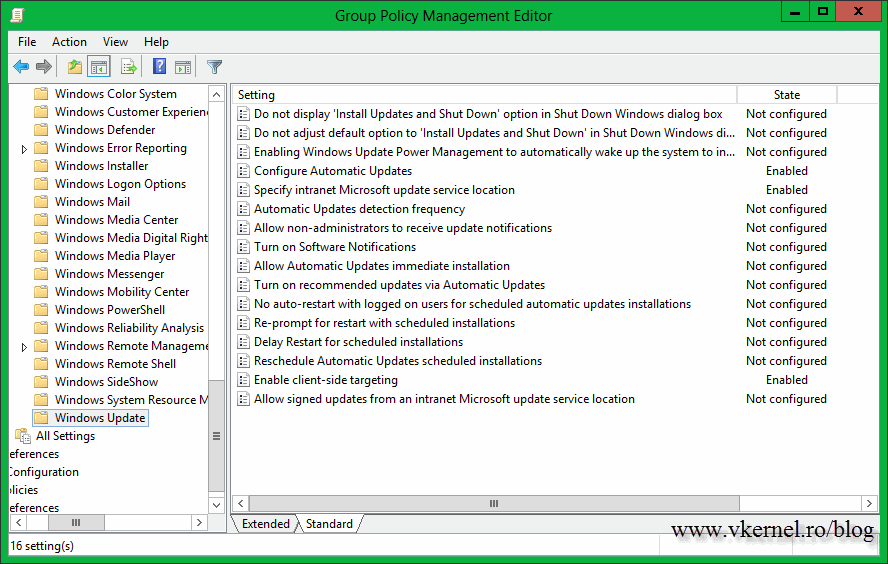
Drill down to Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Update and enable the following policies:
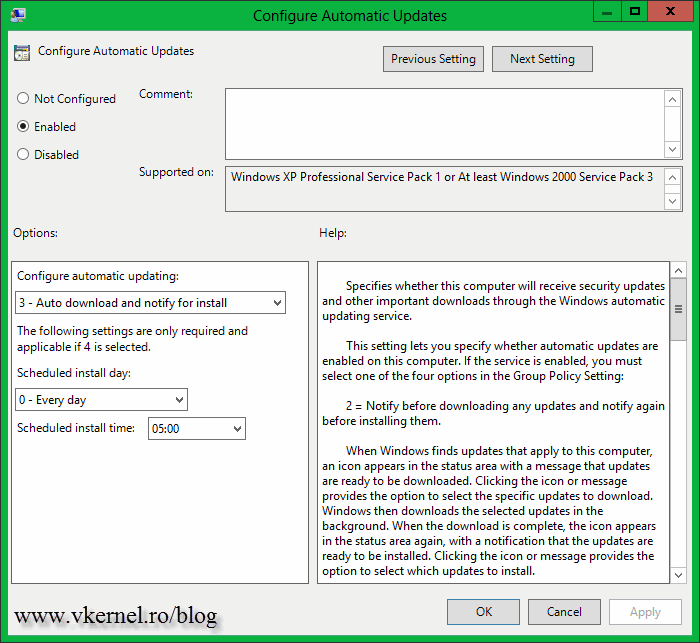
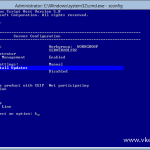
Configure Automatic Updates – make sure you do NOT configure this policy to automatically install the updates. I set mine to just download the updates from source (WSUS server) and notify me when they are ready to install. If you configure to automatically install the updates the Cluster-Aware Updating feature is useless and you are back to the old method. You can also configure the policy to notify you when updates are available, but I like to have the updates already downloaded on the servers when the patching scheduler is triggered.
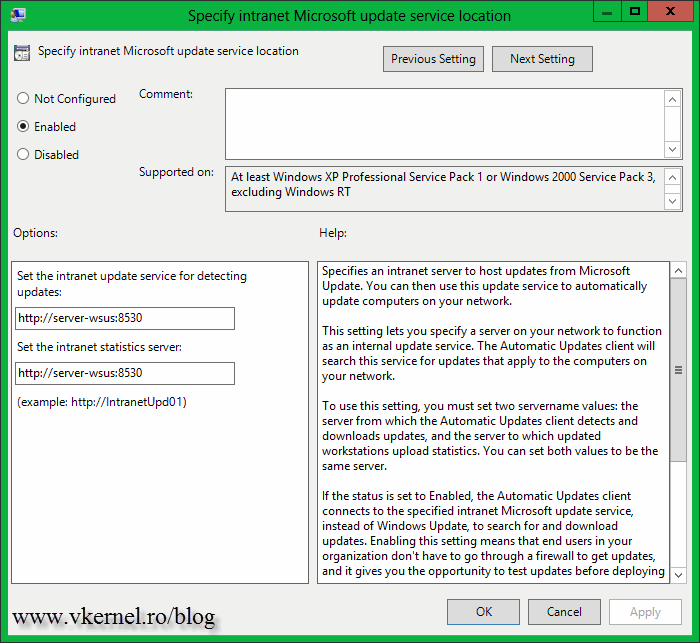
Specify intranet Microsoft update service location – since we are using a WSUS server, this policy needs to be configured too. Type your WSUS server address and hit OK.
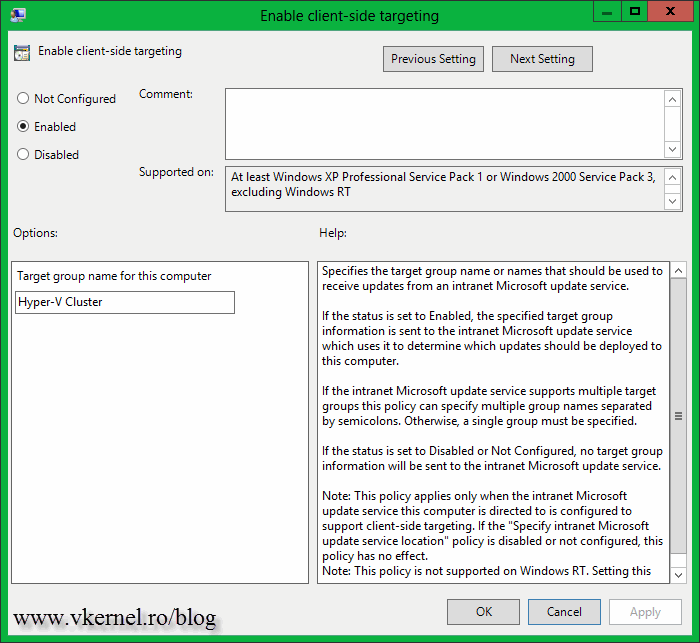
Enable client-side targeting – this is not mandatory, but I like to have some order in my WSUS server, that’s why I configure this policy; to put the servers in a separate WSUS computer group.
If you want more details on how to configure the WSUS server and create policies for clients, read this article. After all this, you will have to wait between 90 and 120 minutes for the policy to apply, but if you are in a hurry you can force a policy update.
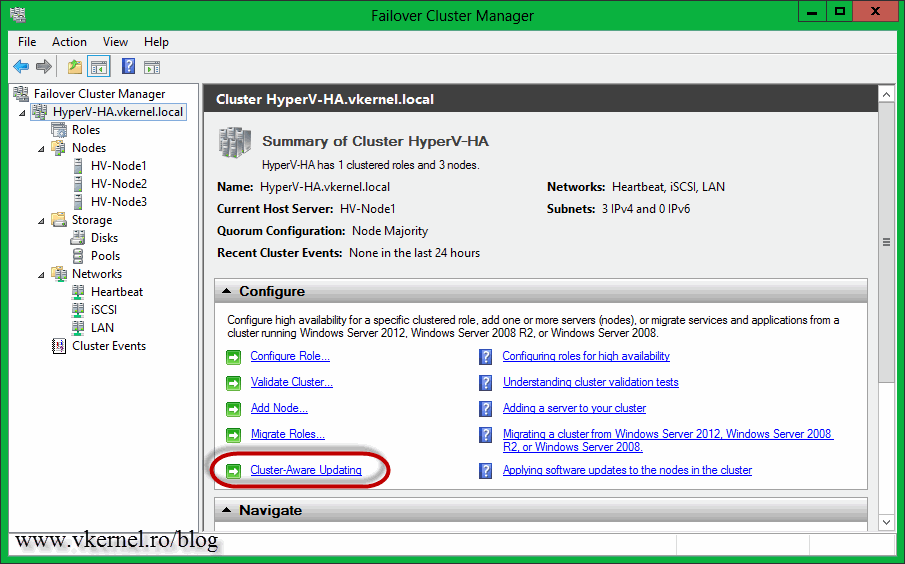
The next step is to open the Cluster-Aware Updating console. This can be done from the Failover Cluster Manager console or directly from the Start screen.
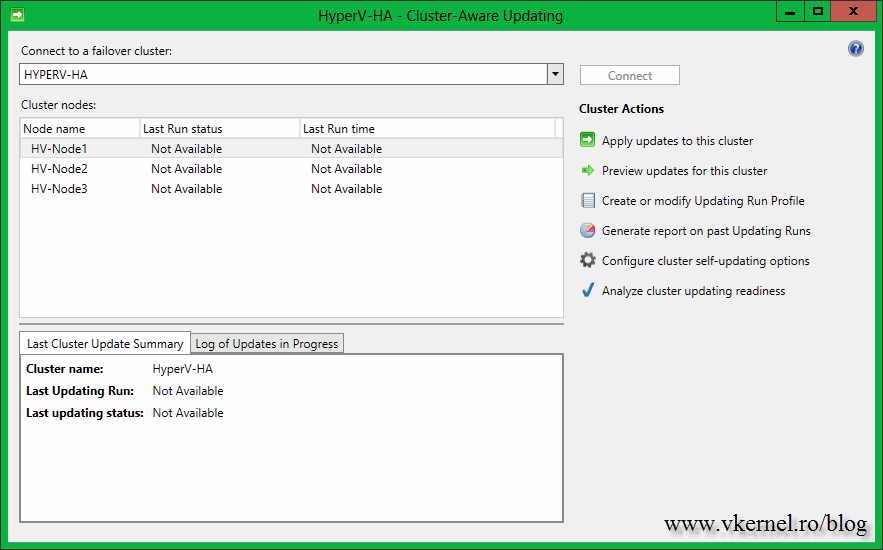
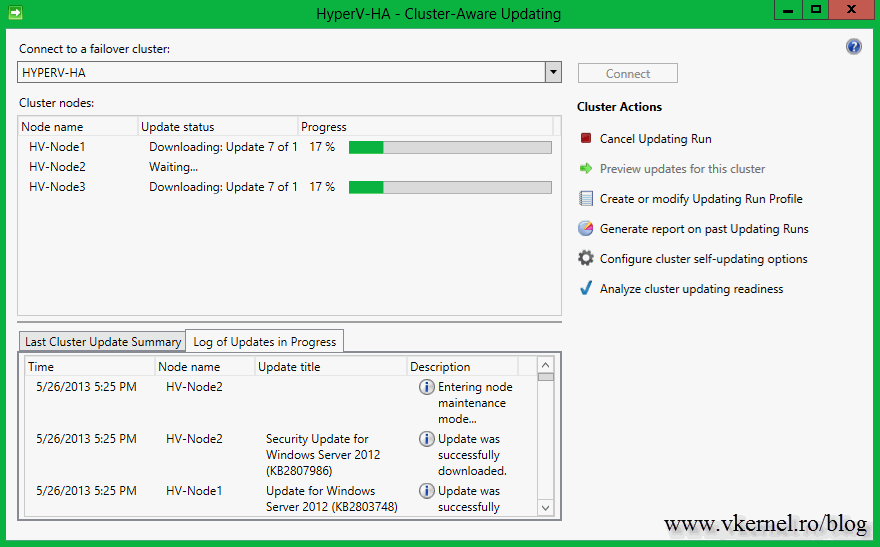
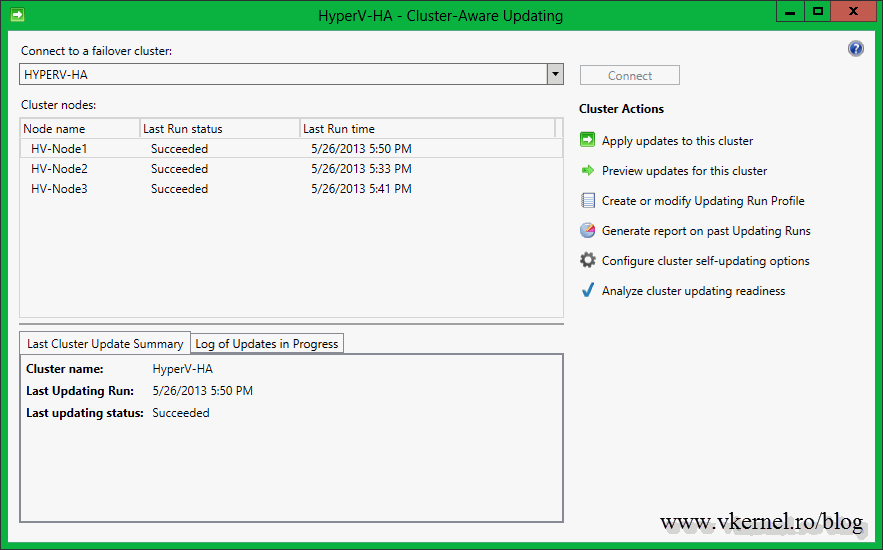
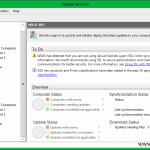
After the console opens, the first thing you need to do is to connect to the cluster. Type the cluster name in the Connect to a failover cluster box, then hit the Connect button. If the connection was successful, all the nodes that are part of that cluster should be listed in the Cluster nodes area. No information is available yet, since this is the first time it’s running.
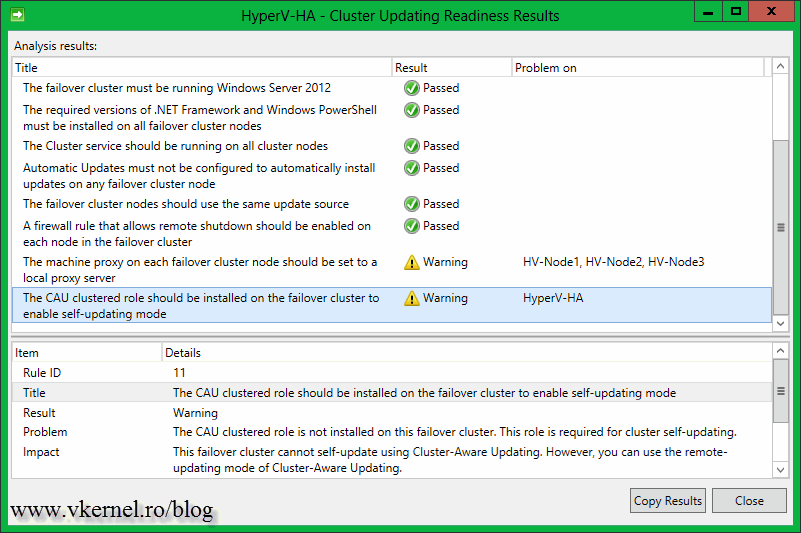
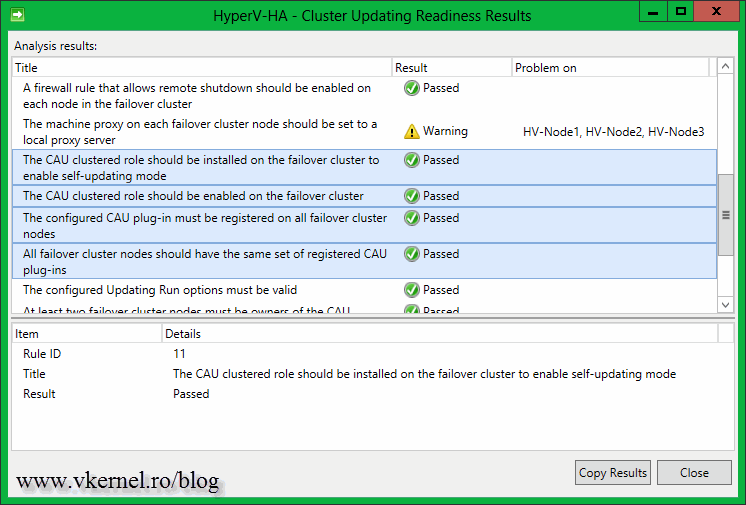
Click the Analyze cluster updating readiness to see if all the cluster services and management commands are responding on all the nodes. You might get the message: The CAU clustered role should be installed on the failover cluster to enable self-updating mode “…” This failover cluster cannot self-update using Cluster-Aware Updating. “…”. This is because the Cluster-Aware Updating self-updating options are not configured for this cluster; we’ll handle this later. Ignore the proxy error, that’s the WinHTTP proxy setting, not the one you configure in IE, but if you are running a proxy server in your environment this needs to be configured. For more information, consult this Microsoft TechNet page.
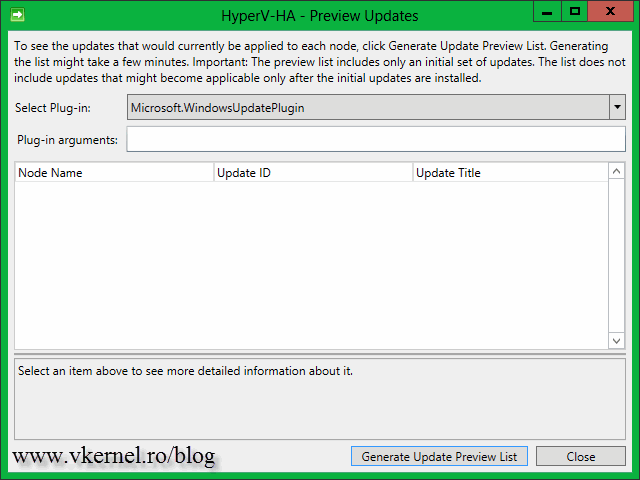
For now just close this window and click the Preview updates for this cluster link then hit the Generate Update Preview List button. After a few seconds a list with all the available updates for the cluster nodes are displayed. This are the updates I approved on the WSUS server.
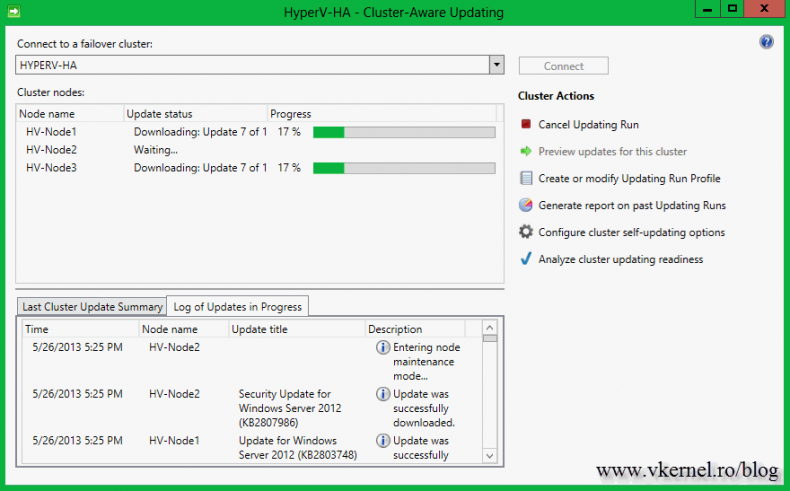
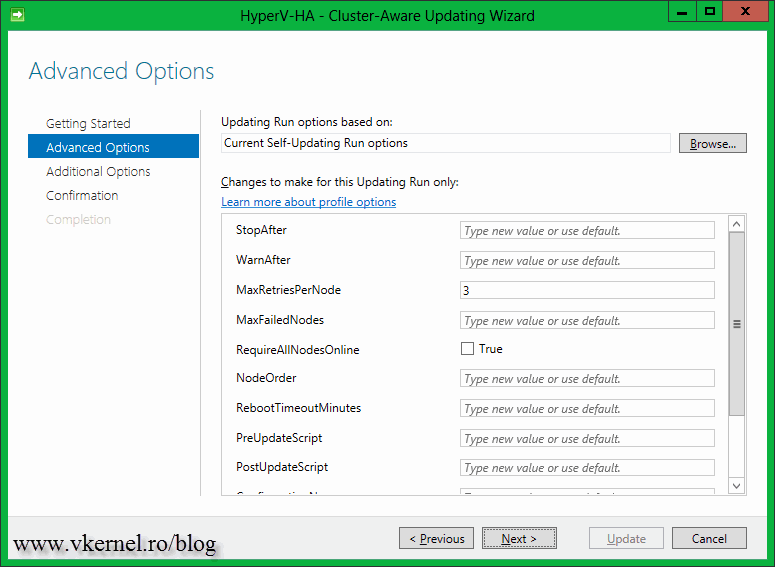
When you are ready to patch the cluster, all you have to do is click the link Apply updates to this cluster. You will see some options during the Cluster-Aware Updating Wizard that you can modify, but for now the default settings are just fine. At the end of the wizard click Update and watch the magic happen.
The wizard will download updates and put one of the nodes in maintenance mode. In my case the updates were already downloaded on the servers, since that’s how I configured the update policy (see above).
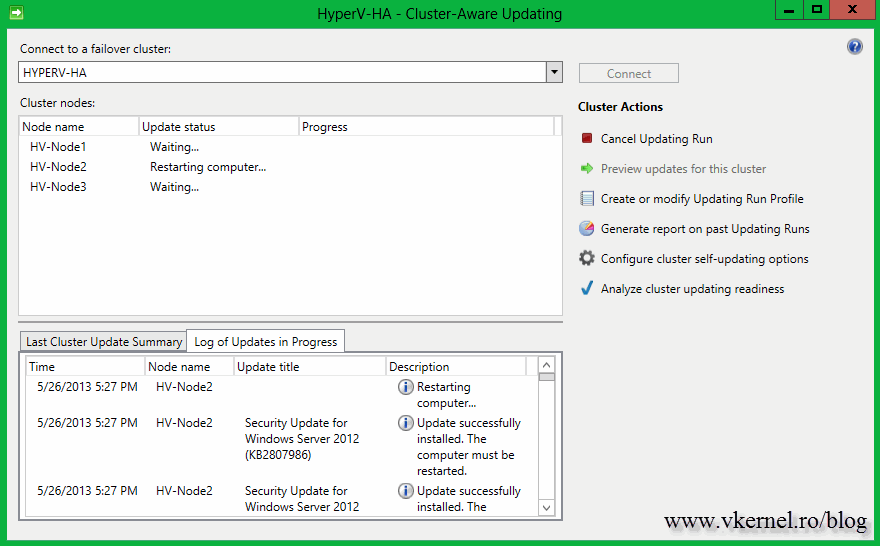
After patches were applied the server will be automatically rebooted,
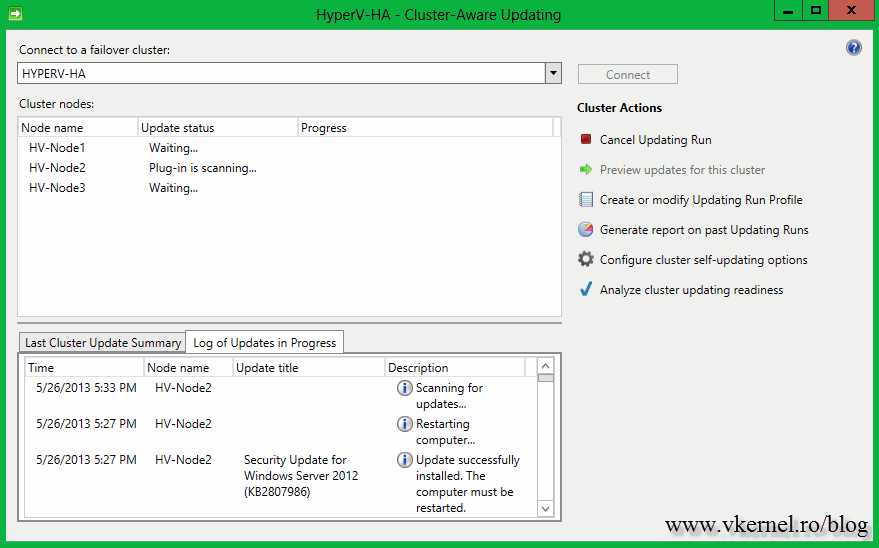
rescanned, and taken out of the maintenance mode.
When the node is up and running in the cluster (online) the patching for another server starts in the same way.
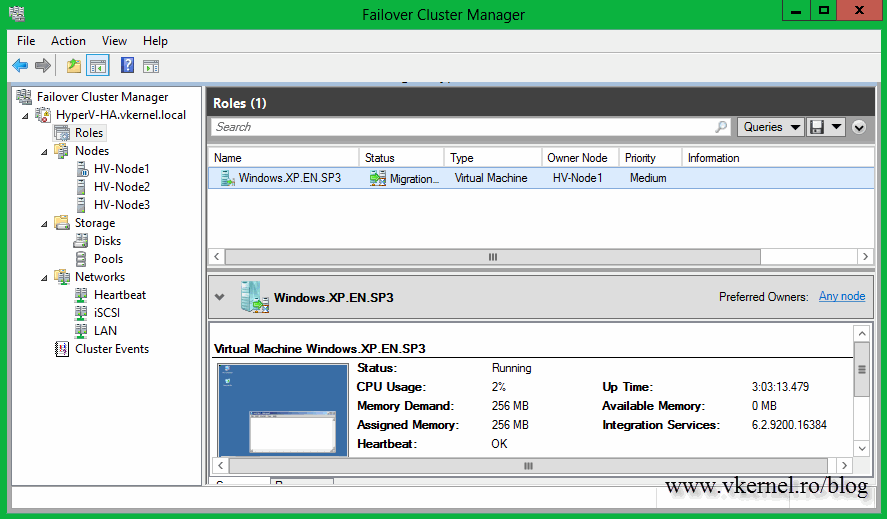
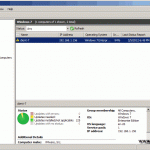
We finally got to the point where the node that is holding the VM is ready for patching. The VM is automatically migrated to another node and the one the was running on is put into maintenance mode.
You might have to refresh the screen in order to see the migration process.
At the end your servers should be patched and online in the cluster, and the cluster roles should automatically migrate on the original node they were running before patching. As you can see my VM was migrated back to HV-Node1; the node that was running on before the patching process started.
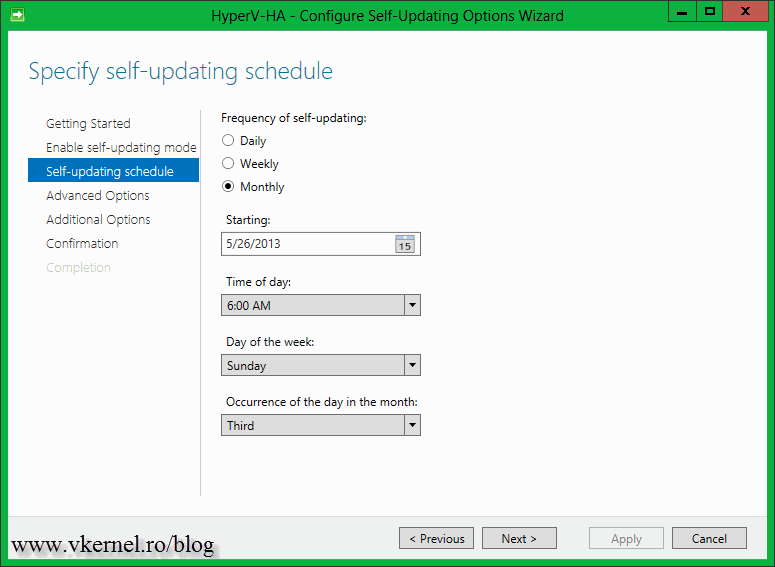
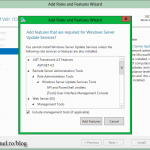
Everything went perfect but there is one more thing to discuss, the self-updating option. By configuring this you can schedule the patching process so you don’t even have to touch the Cluster-Aware Updating console. This schedule can be set by clicking the Configure cluster self-updating options link in the Cluster-Aware Updating console. After the Configure Self-Updating Options Wizard pops-up click Next to skip the Getting Started screen. On the Add Clustered Role page check the box Add the CAU clustered role, with self-updating mode enabled, to this cluster. If you are in a big organization you might require to prestage a computer account for the CAU clustered role because of the security policies. In that case prestage the computer account then check the box I have a prestaged computer object for the CAU clustered role. Since I’m logged in with a domain admin account I have all the right I need, so no prestaging for me. 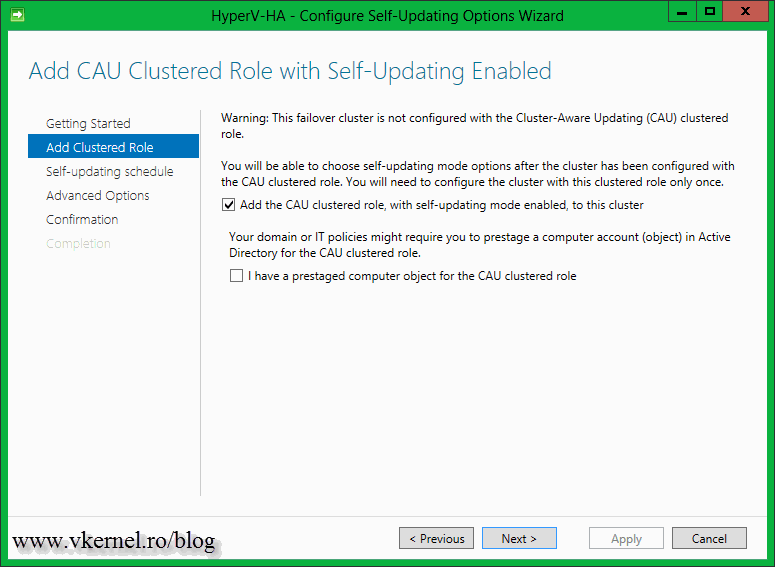
Schedule when the patching should take place then click Next.
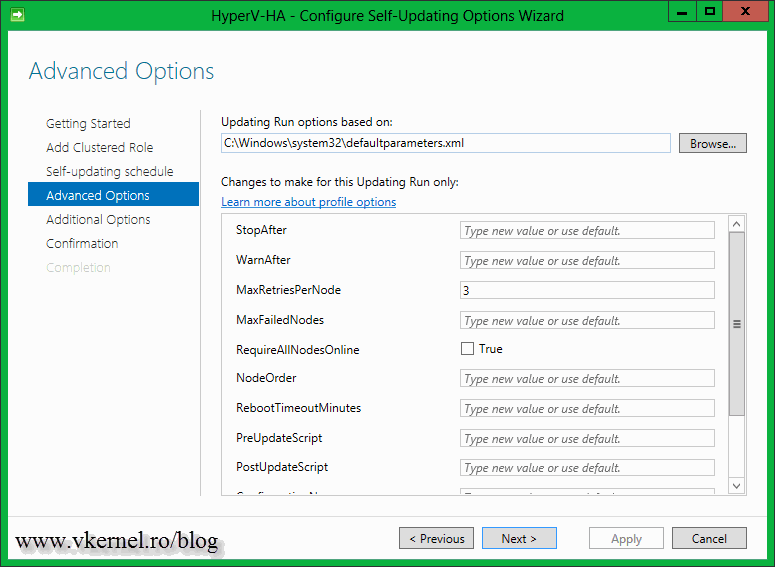
If you want a more advanced configuration on how the patching process should handle the nodes in the cluster, configure this options. Most of the time the default settings are just fine.
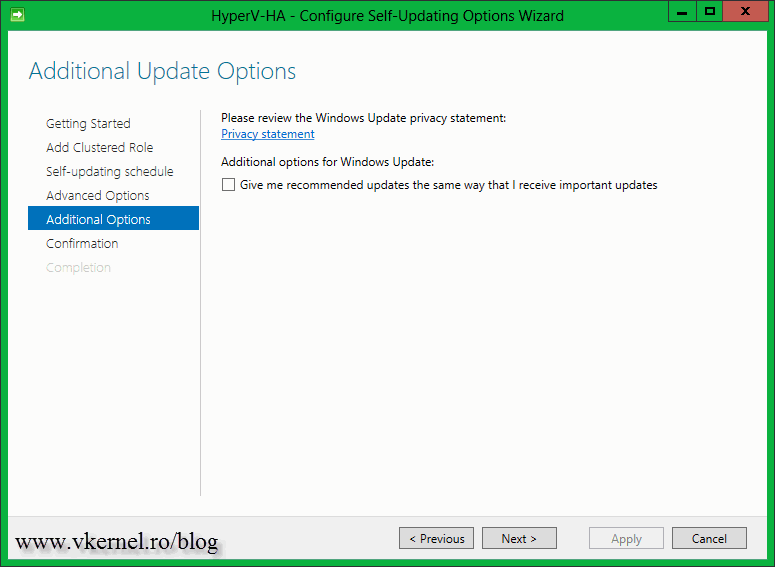
For receiving recommended updates, check the box Give me recommended updates the same way that I receive important updates.
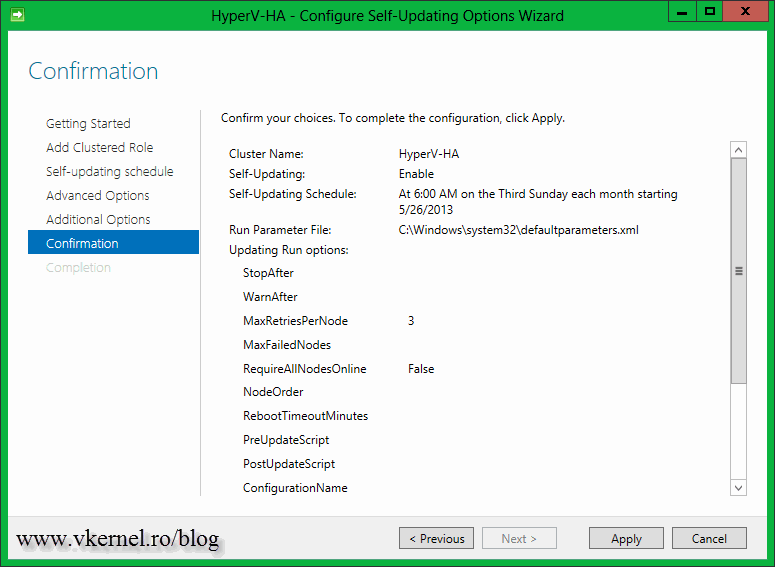
On the Confirmation page click the Apply button to write the configuration changes.
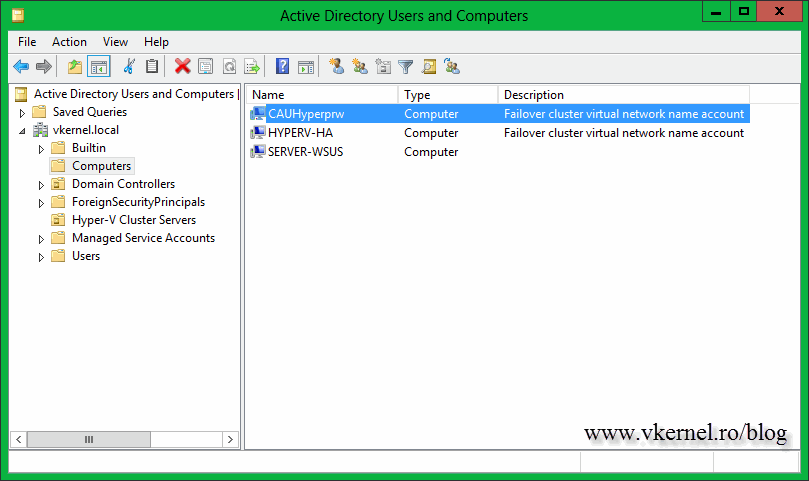
A computer account should be created in AD by the wizard, if you did not prestaged it in advance.
Now if the cluster is analyzed again, the warning about the CAU clustered role should not be displayed anymore.
Nice feature and easy to use. Think about, it if you have more than ten clusters, or even five of them, how much time and work will be reduced by using this. All that extra time is for you to learn something else.
Want content like this delivered right to your
email inbox?

Hi Adrian.
It should be installed in DC or in the servers belongs to Failover Cluster?.
Thanks,
Mario.
Hi Mario,
Nothing gets installed on DCs, it’s rule of thumb. You need separate servers that are part of the domain and on this ones you install the service.
I have installed as you said. How it works really?. I mean, Do I have to setup something in WSUS to auto download the patches in this Cluster?.
BR
Yes, you have to configure WSUS and the servers to download updates from the WSUS server. Here is an article on how to do it.
It got resolved , I just deleted the computer account obj and created the account with the cluster full permission and also added it as the pre_staged computer OBJ..Thanks for looking in to the issue..
Glad you solved it. I appreciate your comment; it helps others.
I configured the same settings and when I run the Apply updates to this cluster , it is not updating the patches and it shows the WARNING ” The updating Run has been Triggered , but it has not yet started and might take long time or fail.
Hi Ganeh,
I create a lab trying to reproduce the error but is not showing up for me. Did you set up the GPO to download updates but don’t automatically install ? Maybe is trying to download updates and fails or can’t connect to the update source. I can’t say for sure because I’ve never seen this error.
What the logs on the hosts are saying ?
Also, verify the update log in the Windows folder see if you have any errors.
Let me know what you find.
Is there a quick way to find out which computer account is associated with which cluster? We’ve got a few and the auto-generated account names don’t make it easy to tell which is associated with which cluster.
Hi,
Sorry for the late response. For some reason your message got into the spam folder :-).
You can’t be connected to multiple clusters at once with Cluster-Aware Updating, so you don’t have to make the difference. All you have to do is to look at which cluster you are connected to. Hope this answer your question.