Set Up Automatic Certificate Enrollment (Autoenroll)
Managing certificates usually does not need to much intervention. Issuing and enrolling for certificates, again is a piece-of-cake… in a small environment. But if you are running more than let’s say 50 workstations and servers enrolling for certificates is a week job, if not more.To ease the work; actually to automate this you can use Active Directory since you already have the tool in your hands. This is one of the advantages of an Active Directory domain with an Enterprise CA; you can deploy certificates automatically using a process known as autoenrollment. This greatly reduces the amount of administrative overhead required to deploy certificates to your clients; and all you need for this is a GPO linked to your domain or an OU configured with the autoenroll policy.
Before we start I presume you already have your Active Directory Certificate Service installed and at least some clients joined to the domain to be able to test this. If you don’t have enough hardware at your disposal, VMware Workstation is great way to do test labs.
In the first part of the article I’m going to talk about Computer Certificates Auto-Enrollment and in the second part about User Certificates Auto-Enrollment.
Computer Certificates Auto-Enrollment
Now log in to one of your domain controllers and open the Group Policy Management console.
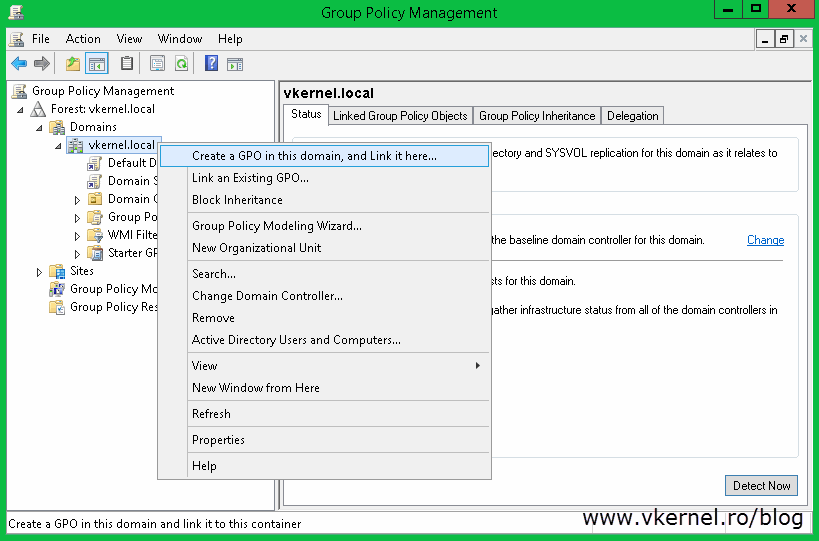
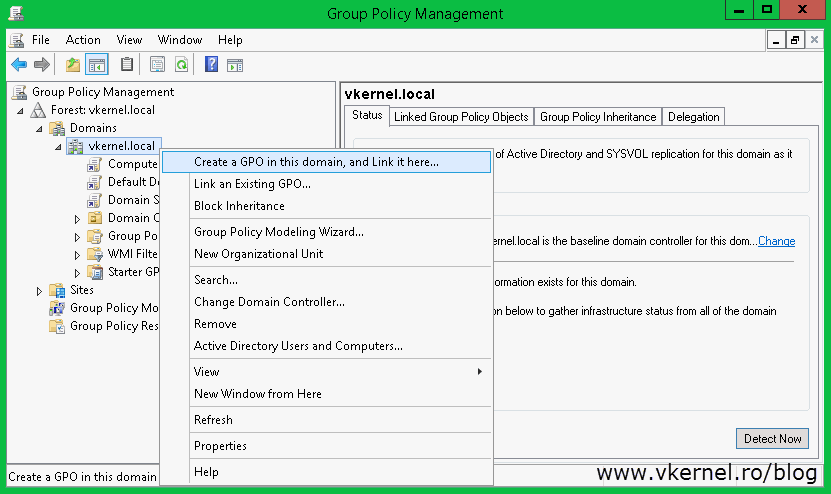
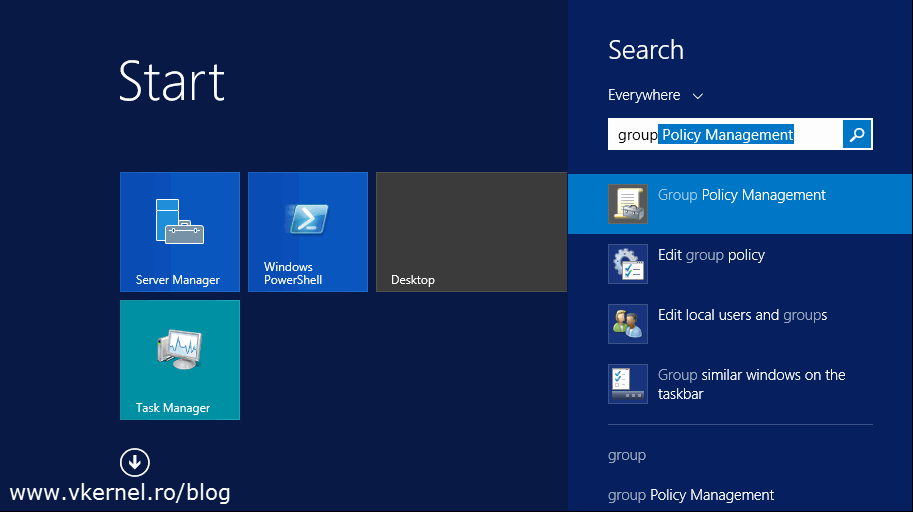 Here you have to decide where the GPO should be linked. If you want only a bunch of clients to be configured for autoenrollment, create and link the GPO to the OU where those clients sit. If however, you want the policy to apply to all clients in your domain, create and link the GPO to the root of the domain. To create the GPO, right-click the root of the domain or the OU and choose Create a GPO in this domain, and Link it here…. Give it a name and click OK.
Here you have to decide where the GPO should be linked. If you want only a bunch of clients to be configured for autoenrollment, create and link the GPO to the OU where those clients sit. If however, you want the policy to apply to all clients in your domain, create and link the GPO to the root of the domain. To create the GPO, right-click the root of the domain or the OU and choose Create a GPO in this domain, and Link it here…. Give it a name and click OK.
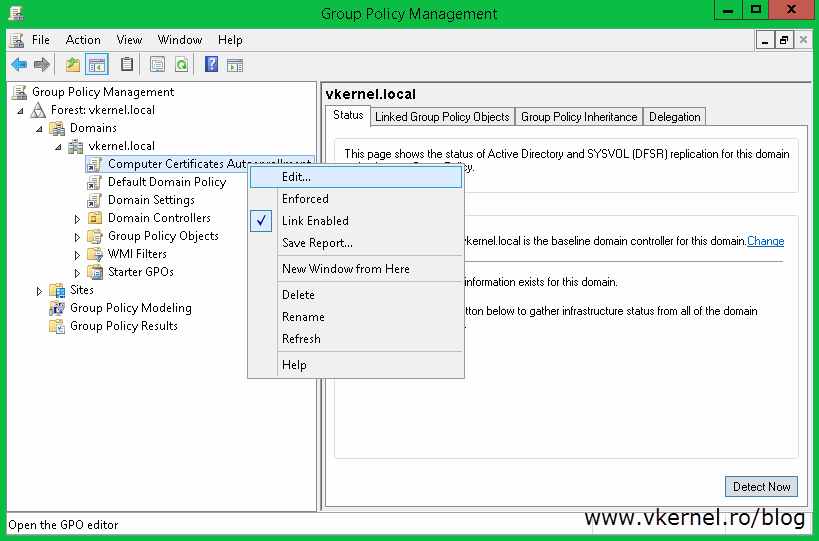
On the newly created GPO do a right-click and choose Edit.
Once the Group Policy Management Editor opens, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies. Here you will see Certificates Services Client – Auto-Enrollment policy.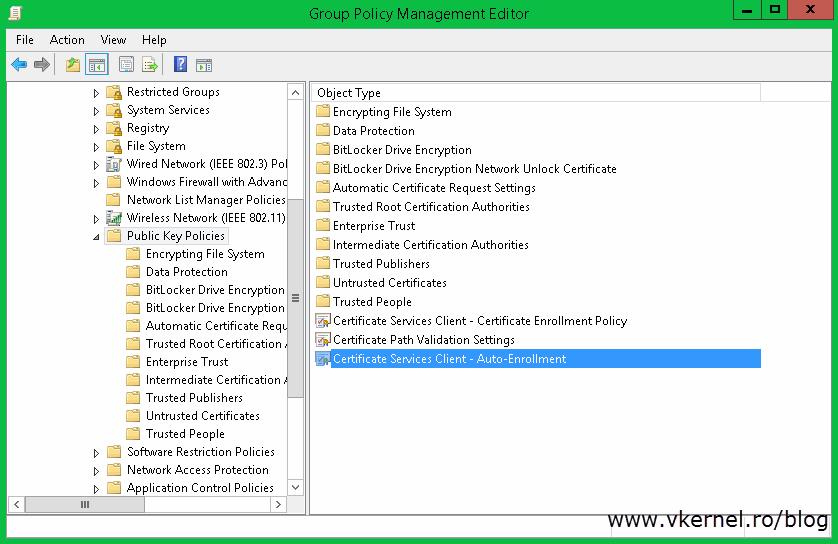
Open its properties and choose Enabled on the Configuration Model box, then check the boxes Renew expired certificates, update pending certificates, and remove revoked certificates and Update certificates that use certificate templates. Click OK when you are done. As you can see this policy will automatically renew any expired certificates and also cleans up the certificates store of any certificates that expired.
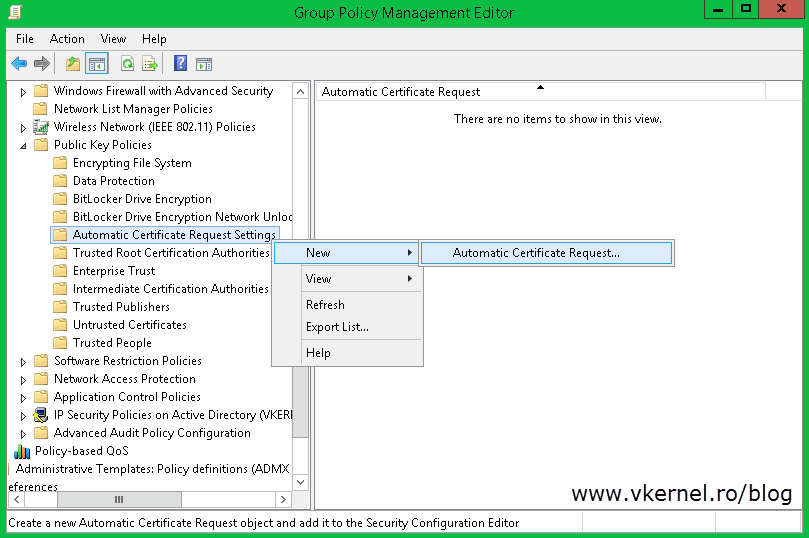
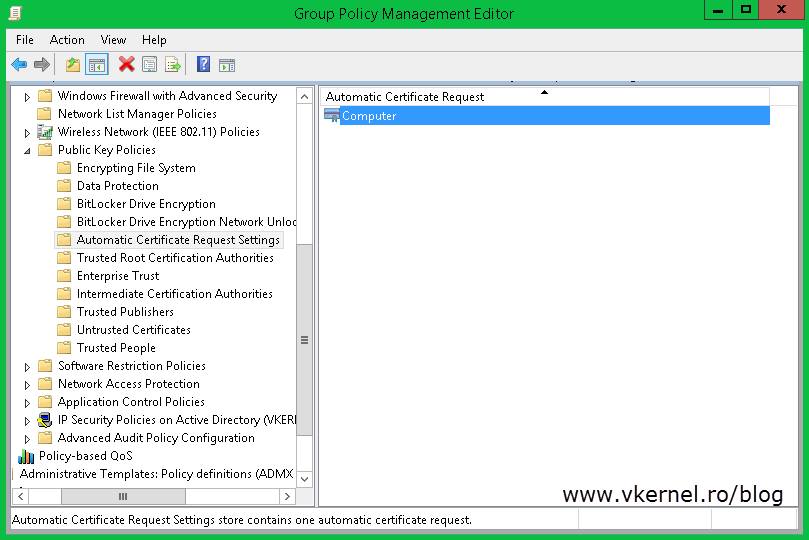
Only configuring this will not get the job done. You have to tell the clients what type of certificate they can request and this can be done by creating a Certificate Request Setting. To set it up expand the Public Keys Policies folder, right-click Automatic Certificate Request Settings and choose New > Automatic Certificate Request.
Click Next to skip the Welcome screen of the wizard.
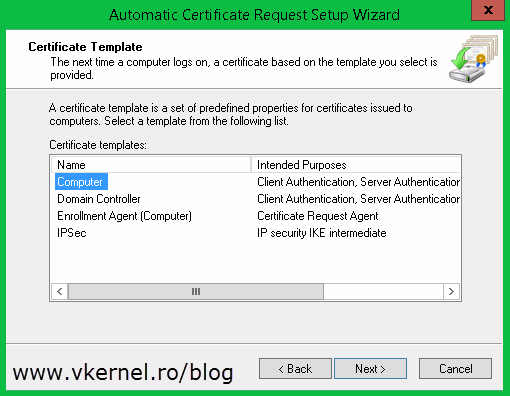
On the Certificates Templates page you can see all the templates that you can use to issue certificates from. The only one we are interested right now is the Computer certificate. Select it and click Next and at the end click Finish to close the wizard.
Now you have a Certificate Request Settings created. Let’s tests it and see if it works.
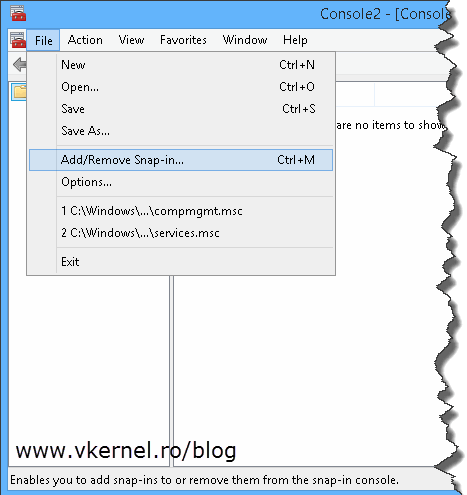
Log in to one of you clients and open the certificate store from Start > Run > mmc. Once the console opens, from the File menu choose Add/Remove Snap-in.
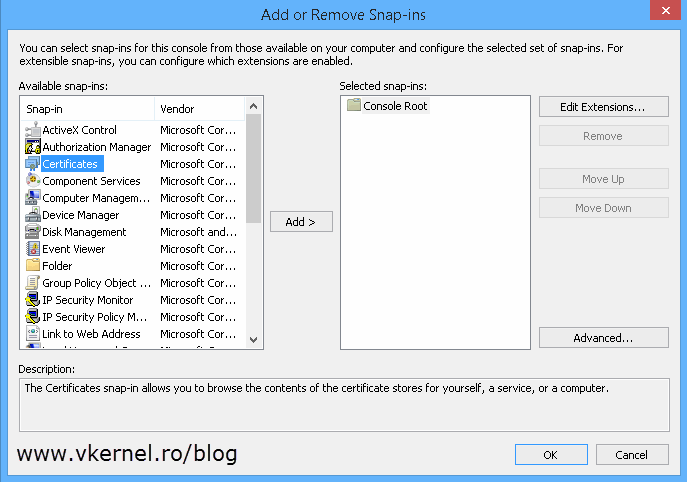
In the Add/Remove Snap-ins window select Certificates and click the Add button.
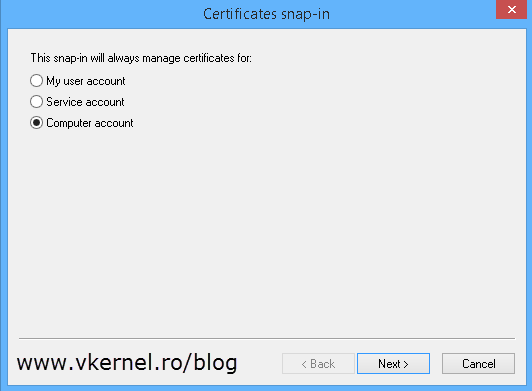
Choose Computer account > Local computer.
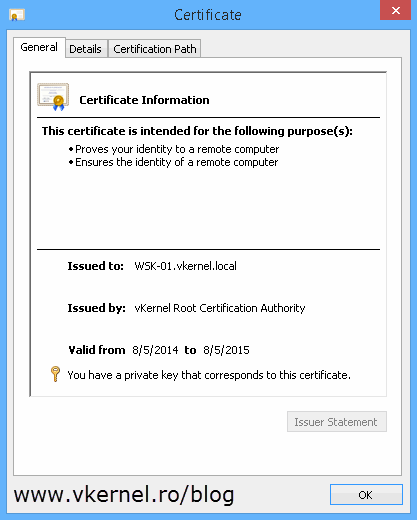
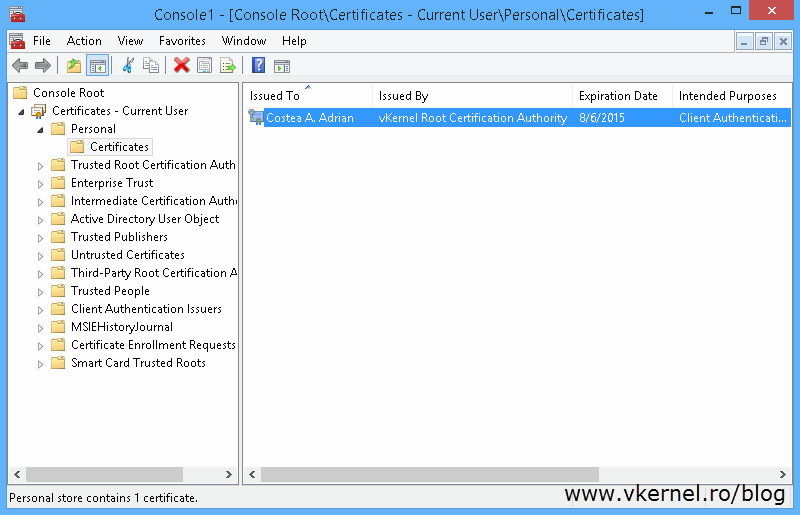
If you look in the Personal folder you can see that there is no certificate. Too see the magic happen in real time do a gpupdate /force then refresh the console. After this a computer certificate “magically” appears.
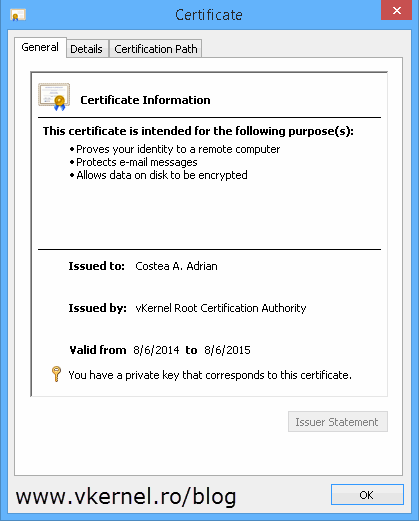
Oh yeahh, and the certificate also has a private key, which is what we wanted.
Since this is group policy, you will have to wait between 90 and 120 minutes for the policy to get in effect. Then all clients that are affected by this GPO will auto-enroll for a computer certificate from your internal CA.
User certificates Auto-Enrollment
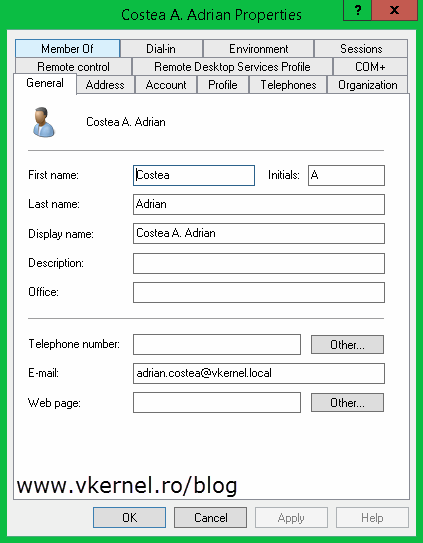
Now I know that most of you also need a way to auto-enroll for user certificates, so these users can encrypt their personal data or secure their emails. For this, a few things need to be modified or added to your Enterprise Internal CA and users accounts. Fist of all the users need to have an email address present in the E-mail field of their AD account
[important]You don’t need to have an email server present in your environment like Exchange server, just an email address typed in the user’s E-mail account field.[/important]
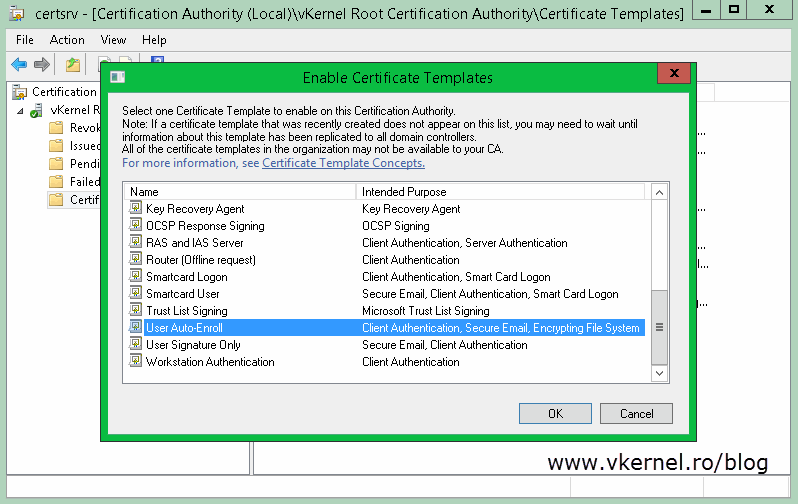
then, a new certificate template needs to be created. Log in to one of your domain controllers and open the Certification Authority console. Right-click the Certificate Templates folder and choose Manage.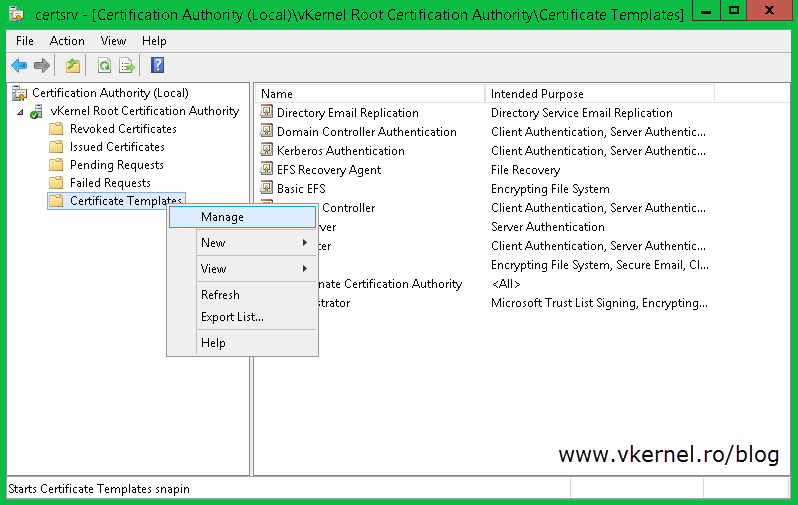
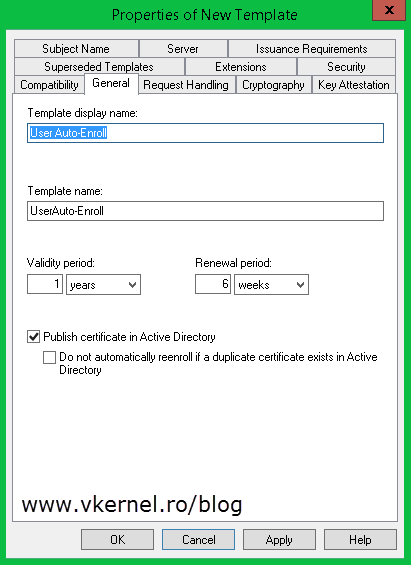
Search for the User template, right-click it and choose duplicate.
On the General tab type a name for the new template then go to the Security tab. Here select Domain Users from the ACL (Access Control List) and in the Permissions section check the Enroll (should be already checked, but just in case) and Autoenroll box. Click OK.
Back on the Certification Authority console, right-click the Certificate Templates folder one more time and choose New > Certificate Template to Issue. From the list, search for the new template, select it and click OK.
Now that the template is ready we need to set up the GPO that request certificates on behalf of the user. Still on this domain controller, open the Group Policy Management console and create a new GPO. Again this can be created/linked to the root of the domain or an OU. If you link it to an OU make sure is the one where users are present not computers.
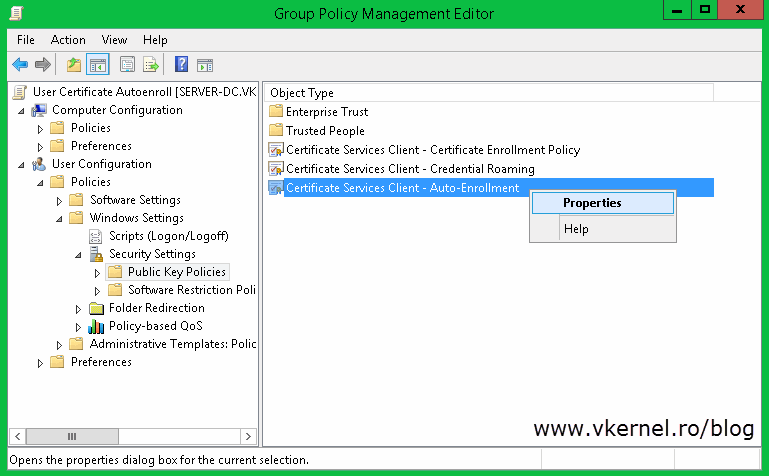
Once you create the GPO, right-click it and choose Edit. In the Group Policy Management Editor console expand User Configuration > Policies > Windows Settings > Security Settings and click on the Public Key Policies folder. Here we have a view almost exactly we had when we configured the computer certificate auto-enrollment. The policy that we are interested in is Certificate Services Client – Auto-Enrollment, so double click it to open its properties; or right-click > Properties.
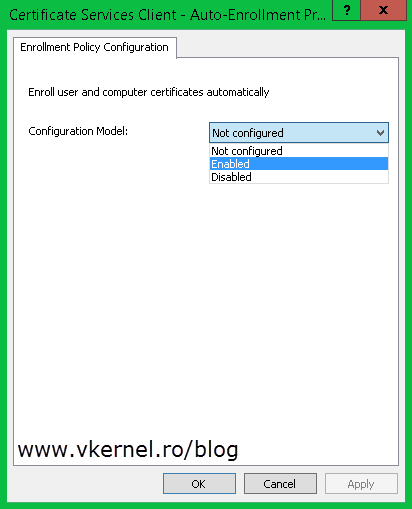
From the Configuration Model drop-down box choose Enabled then check the Renew expired certificates, update pending certificates, and remove revoked certificates and Update certificates that use certificate templates boxes. Click OK when you’re done.
All you have to do now is wait for the users to get the new policy, and that can take between 90 and 120 minutes. If you don’t want to wait and force this process to see if it works do a gpupdate /force on the client computer. Then if you open the user certificates store you should see the certificate issued for the user that you are logged in with.
Taking a look at the certificate itself it has a private key, it was issued using the template we created and it has all the key usage necessary for the user to encrypt data and email.
As you can see, this is a great feature that comes with AD and it only takes a couple of minutes to set it up, but gets you rid of days of working.
Want content like this delivered right to your
email inbox?


Hi, thanks for the great post. I have setup autoenrollment based on this informaotn. But for Emial Signature and Encryption certificates it happen for someusers to get issued new certificates based on a new private key even though a still valid certificate exists in AD and PKI. Any idea under which circumstances, the user itself has not enrolled any certificate manually for sure, a new certificae is issued when another valid one already exists in PKI and AD?
Also which certiicate is used in an AD/Outlook/Exchange environment if for a certain recipieint user more thenone valid certificates is found in AD user object –> Published Certificates? Also see https://social.technet.microsoft.com/Forums/en-US/5f3c0a95-13f6-4872-8ae0-6c285d04841c/autoenrolled-gpo-email-encryption-certificates-multiple-and-why
thanks
Hi,
It is the same template for the MIME certificate?
Great Post, my question is that the first time when a domain user logins on, how to issue a certificiate for user/computer?
As my WI-FI is using EAP-TLS authentciation, user/computer must have a valid cert and then he/she is allowed to connect WI-FI.
Once he/she connects to WI-FI, he/she is able to use domain accounts to login on, and reqeust a cert via Group Policy.
So it is contradictory, user needs cert to auth first, but user’s cert needs to network first(WI-FI).
So do you have any idea how to resolve this?
something like group polic is deployed and cert is ready before user tryies to login on as domain users。
HaHa, first use computer certificate, so WI-FI is avaiable before user tries to login on.
Thanks a lot, pretty nice post, again. Lol.
Thank you
Hi I am using User Auto Enrollment for 802.1x and for computer I am using the ACR but its not using the template i created its using the computer template that was already in my Certifciate Authority will that still work and will it auto renew expired certs?
Hi,
Yes, it will but make sure you have the proper permissions on the template so computers/users can access it.
I am configuring GPO to auto enrol computer certificate for all my Win10. I have duplicated the “computer” template to “Win10 computer” with “authenticated user” permissions = “enrol” and “autoenrol”. However in GPO \ Computer configuration … Auto cert Settings > “new”, it does not show “Win10 computer”, only “Computer” which people call as V1.
How can I enrol upon “Win10 computer” template as well as can we choose which CA server (we have 2 intermediate CAs with same templates).
Thx
Hi,
After creating the template you need to make the certificate available for enrollment. On your CA right-click Certificate Templates > New > Certificate Template to Issue. Choose the Windows 10 certificate that you duplicated and it should work. Let me know if it doesn’t, and I will give more details.
the “Automatic Certificate Request Settings” is only vor V1 certs, with V2 and V3 certs you can ignore setting this setting.
Hi! I have been trying to configure auto enrollment but i want it to enroll smart cards certificates automatically to people that log in using a smartcard without any certificate on it. Any ideas??
You will have to create a Smart Card template in your CA then it will work. From what I can remember there is one by default. Check the Security tab of it and make sure the domain users have the Enroll and Auto Enroll rights.
Let me know how it works or if you need further help I will create a lab. It’s been a while since I used smart card.
Great article! Now my User Autoenrollment works finaly. Thank you very much!
You are more than welcome.
Another question regarding Domain Controllers: are they auto-enrolling their certs out of the box? Or would I have to repeat the same procedure to create a GPO using the “Domain Controller” template?
Thanks again!
Nope. You need to create the template, set it up for issuing then configure the auto-enroll policy. It is not out of the box.
Hi and thanks for this tutorial. I want to add a template to the list of available templates (Workstation Authentication Certificate Template). Do you know the way to do that?
Hi,
You will have to clone an existing template, modify it the way you want (expiration period, security etc) then give it a name and you should be good-to-go.
Is there a way to configure automatic enrollment for remote desktop users?
Hello , Excellent Article!.
One question I have. You explained the way how a specific computer template is selected for putting in Group policy edit.
Like wise can you explain how to how to select a specfic user template to target in the GP edit?
Hi,
The information is already in the article. What are you exactly trying to do so I can help you with ?
I know It’s been a while but I stumbled over the same question Jayesh had (I think): why is it necessary to use “Automatic CSR Settings” only for the “Computer” template and not for the “User” template? I see that this option is not available at all in the User Configuration section of the GPO.
Just wondering why Certificate Services Client would NOT need it to select the correct User type template? Technet articles do not mention this step for the Computer Configuration.
Maybe you can shed some more light on this specific setting and what it does (or what might go wrong if you don’t use it)?
Thanks a lot!
Hi,
I guess is more of a security thing why there is not a user auto-enroll policy. Not every user needs to have a certificate, and when they do, these are issued by an admin.