How to configure Windows Event Log Forwarding
Even if you have a small environment with a few servers here and there, after a while is becoming more and more difficult and time consuming to read the events on all of them. Purchasing a dedicated software solution just doesn’t cut it because of the budget constraints, but you still have to know what errors, alerts or messages your servers are throwing. For this kind of situations Microsoft introduced Event Forwarding. Event Forwarding allows administrators to get events from remote computers, also called source computers or forwarding computers and store them on a central server; the collector computer. Like most of the services out there, Event Forwarding is also using Windows Remote Management (WinRM), which is Microsoft’s implementation of WS-Management Protocol to access and exchange information. This feature is already built into the latest versions of Windows starting with Windows Vista and Windows Server 2008, but it’s also available for down-level operating systems like Windows XP SP2+ and Windows Server 2003 SP1+.
Events can be transferred from the forwarding computers to the collector computer in one of two ways:
Collector initiated – Using this method, the collector will contact the source computers (clients) and ask them for any events they might have. The minimum operating system level required on the source computers is Windows XP SP2 with minimum Windows Remote Management 1.1 installed. For detailed information on how to find out which version of Windows Remote Management your clients have, follow this Microsoft Technet article. Using a collector initiated subscription works great for a few clients, but when their number start to increase it just doesn’t scale well. If that’s the case, the second method, the Source initiated subscription should be used.
[important]For Windows XP with SP2, Windows Server 2003 with SP1, Windows Server 2003 with SP2, or Windows Server 2003 R2, WS-Management 1.1 is not installed by default, which is a minimum required for subscriptions to work. This, or a later version will need to be installed in order for event forwarding to work on these systems.[/important]
Source initiated – By using this method the clients or forwarders transfer events to the collector as required. Systems like Windows Vista, Windows 7, Windows Server 2008/R2 and Windows Server 2012/R2 can be Event Collectors, but this feature is not supported for down-level operating systems. Even tough there are no limitations when a client operating system is used as an Event Collector, a server platform is recommended since will scale much better in high volume scenarios.
1.Configuring event forwarding collector initiated subscriptions
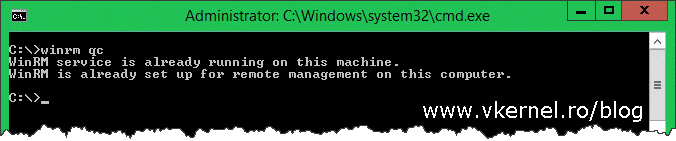
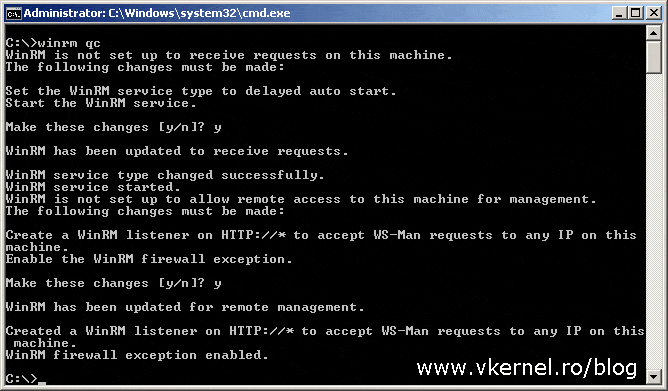
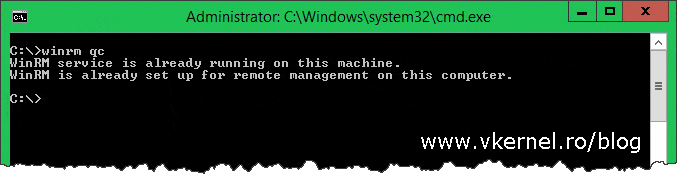
Let’s start by enabling WinRM on the Event Forwarders machines (the clients); and we have two choices here: we either use Group Policy to enable WinRM or we do it manually by issuing the bellow command on a client by client basis:
winrm qc
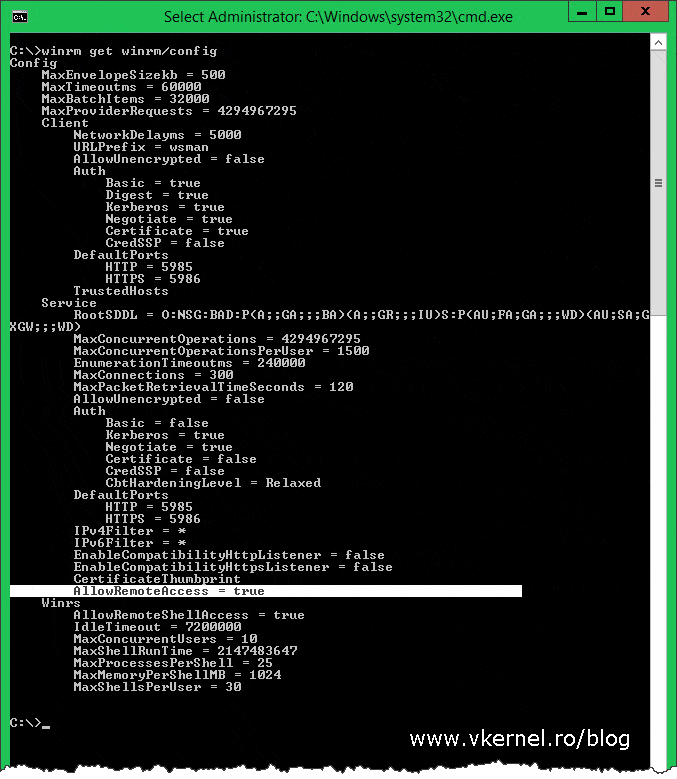
When prompted whether to continue with the configuration or not, type Y for yes then press Enter. If your clients are running Windows server 2012 and above, WinRM it’s enabled by default on them, but just to be sure, you can check the configuration using the bellow command line:
winrm get winrm/config
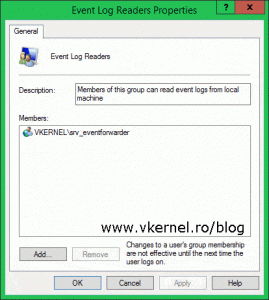
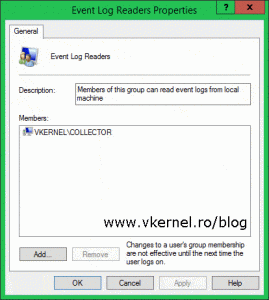
Now that WinRM it’s enabled on all our Event Forwarder computers, we need to give the collector computer rights to read the logs from this computers because right now it has none. We can use the Event Collector computer account itself for authentication, or we can create a user account in Active Directory and use that; either way works just the same. To follow the principle of least privilege rule we need to add the account to the local Event Log Readers group on the forwarder computers. This way we give it just the rights it needs and no more. We can use Group Policy for this or we can do it manually on every forwarder computer. For this lab demonstration I have created a user account in AD, but in the end you should have a result like in one of the bellow images.
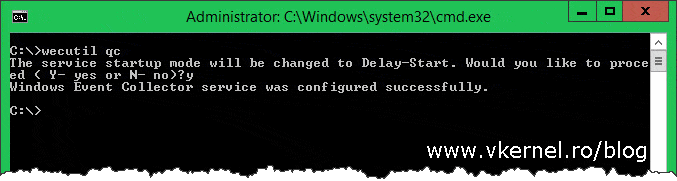
The next step is to enable and start the event collector service on the collector machine, so log in on this server and issue the bellow command:
wecutil qc
When asked, type Y and press Enter to configure and start the Windows Event Collector service. If everything looks good, let’s move forward and create a subscription on the collector computer which “tells” this one for what type of event logs to look for and collect from the forwarder computers. Open Event Viewer from the Administrative Tools page, or just search for it on the start screen.
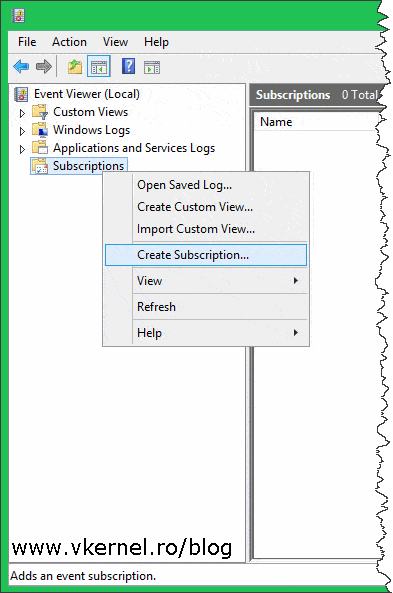
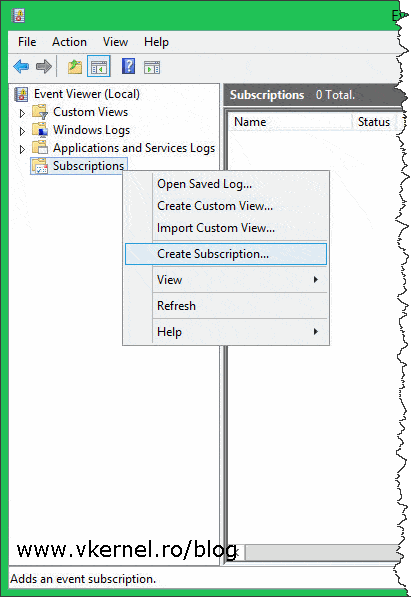
Once the Event Viewer console opens, right-click the Subscriptions folder and choose Create Subscription.
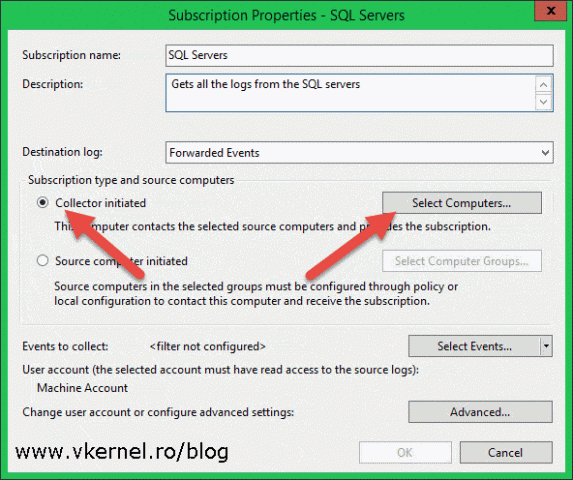
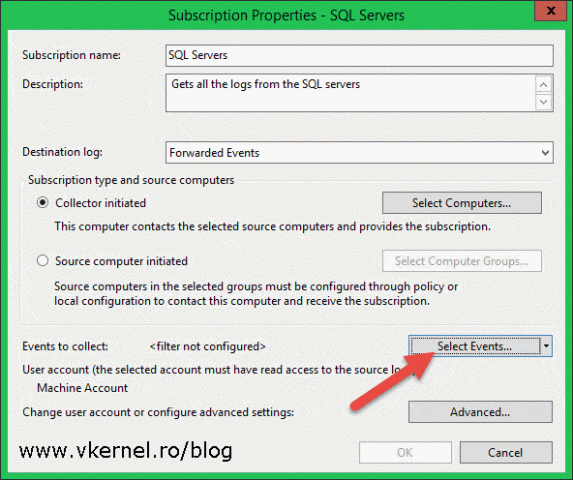
Give the subscription a name and description and choose the destination log from the Destination log drop-down-box. The destination log is where all the events from the forwarders are kept. Usually you will want to leave this as it is because it will be crazy to put all the forwarded events on the Application log for example.
Now click the Collector initiated radio button then hit Select Computers to add the source computers/forwarders from which the collector will pull the events.
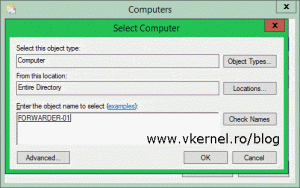
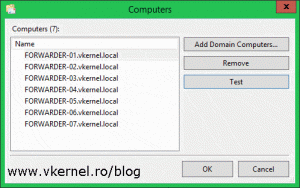
Click Add Domain Computers then provide the name of the first forwarder computer. Stupid thing here because it won’t let you add multiple computer accounts at once. Repeat the process for the rest of the forwarders you have, and once you’re done adding them click OK. You can also create a security group in AD which contains all the forwarder computers and add the group to this list. This way you don’t have to add the clients one by one to the subscription Computers list.
Back in the Subscription Properties window hit the Select Events button.
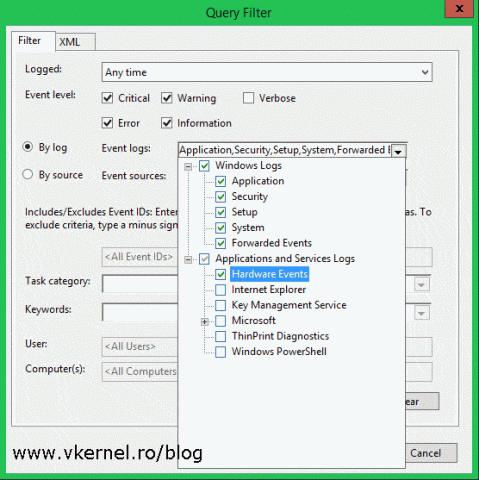
Here you can select which events the collector will transfer from clients. As you can see there are a lot of options to choose from, and for this example will go with a simple one, but fell free to explore. When you’re done click OK to save the changes.
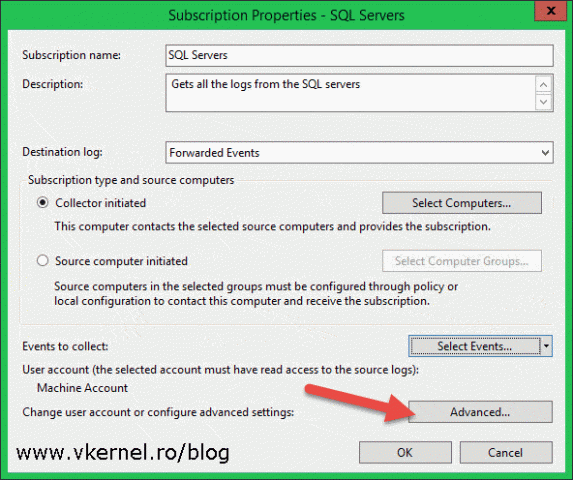
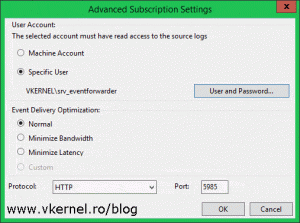
The last step to make this work is to configure the account used by the collector machine to connect to clients. We already added this account to the local Event Log Readers group on every forwarder, so we should not have access problems. To configure the account on this subscription click the Advanced button from the Subscriptions Properties window.
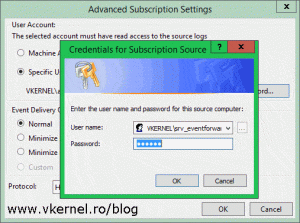
If you are using the collector machine account for authentication, you have nothing to do here since this is the default authentication mechanism. In this example however, we are using a user account that we created earlier in AD and now we need to specify it here. Click the Specific User button, provide the account and credentials and click OK, then move down to the Event Delivery Optimization section where we have three options:
Normal – This option ensures reliable delivery of events and does not attempt to conserve bandwidth. This is not the appropriate choice if you need the events to be forwarded as soon as possible or you need tighter control over bandwidth. It gets the events every 15 minutes by using a pull delivery mode.
Minimize Bandwidth – This option ensures that the use of network bandwidth for event delivery is strictly controlled. It is an appropriate choice if you want to limit the frequency of network connections made to deliver events. It uses push delivery mode and it uses a heartbeat interval of 6 hours.
Minimize Latency – This option ensures that events are delivered with minimal delay. It is an appropriate choice if you are collecting alerts or critical events. It uses push delivery mode every of 30 seconds.
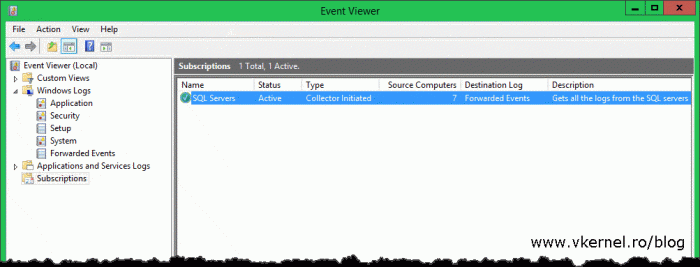
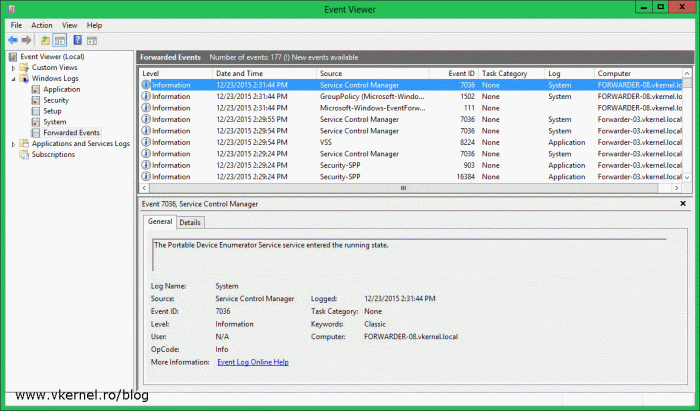
Now you can see the new subscription in the Subscriptions folder. In the columns, it also shows you the type of subscription and how many source computers are part of this subscription.
After ~10 minutes or less, depending on how you configured the Event Delivery Optimization options, logs should start coming in. Bear in mind that past events, before the event forwarding was configured will not show up, only those after the configuration. When new events are available you are notified in the upper bar, and all you need to do to see them is to refresh the console.
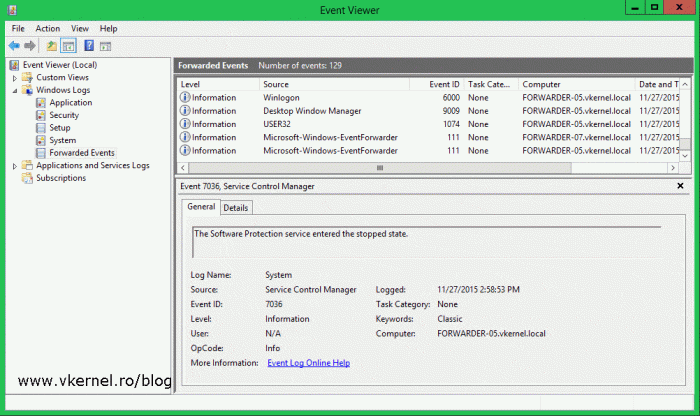
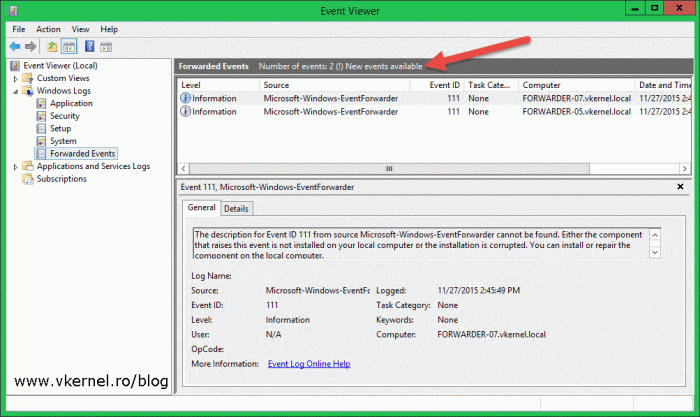 Now as I’ve said, you configure collector initiated events if you have a small number of clients, since it does not scale well on large networks. For that, there is the source initiated event forwarding which I’m going to talk about next.
Now as I’ve said, you configure collector initiated events if you have a small number of clients, since it does not scale well on large networks. For that, there is the source initiated event forwarding which I’m going to talk about next.
2.Configuring event forwarding source initiated subscriptions
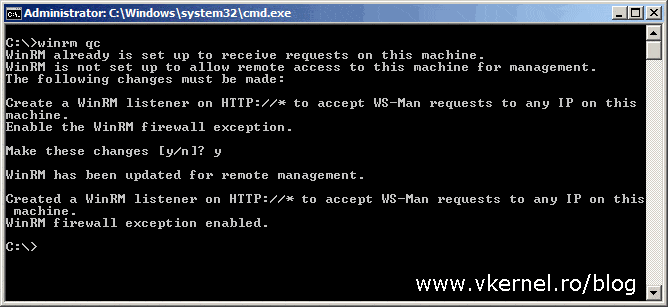
This is a little bit different, and to be honest it’s easier to configure than the other method, but again, it all starts by enabling and configuring WinRM on the forwarding computers. You can use Group Policy to configure WinRM, or you can do it manually by using the bellow command:
winrm qc
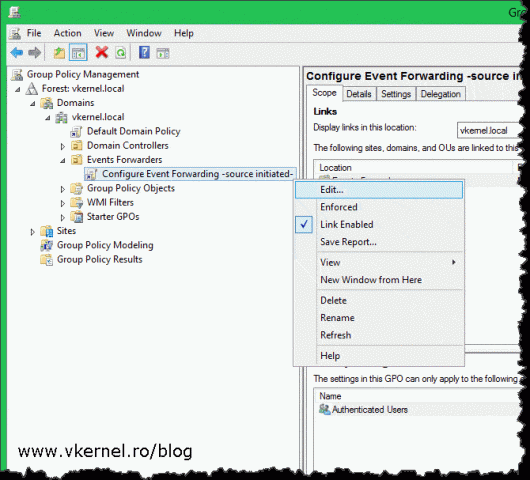
Now that WinRM is running and configured we have to “tell” the forwarding computers where to send their events and again we can use Group Policy or we can do this on a client by client basis by opening the local Group Policy Editor (gpedit.msc). No matter which option you choose, the policy settings are located in the same place. Since the source initiated subscription method is used in environments with a large number of clients, Group Policy will be the preferred choice.
Create a new GPO, link it to your OU where the forwarding computers are sitting then edit the GPO.
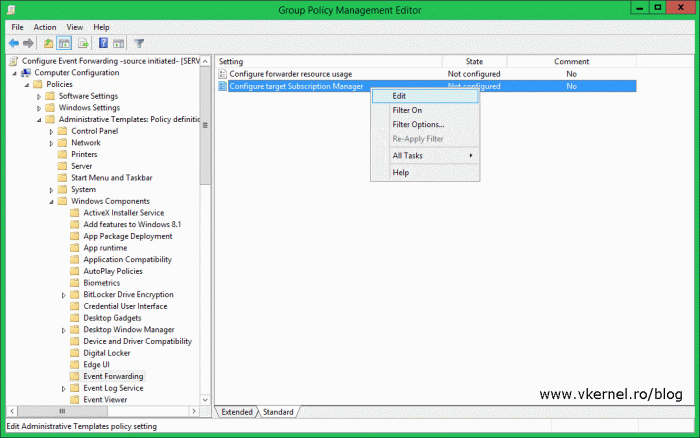
Expand Computer Configuration > Policies > Administrative Templates > Windows Components > Event Forwarding. On the right hand side of the window right-click Configure target Subscription Manager and choose Edit.
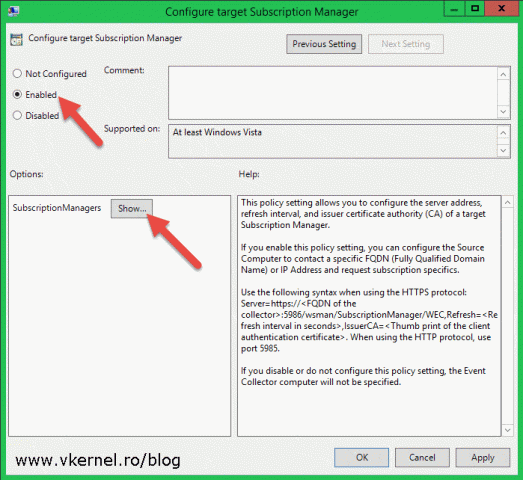
Select the Enabled radio button then click Show.
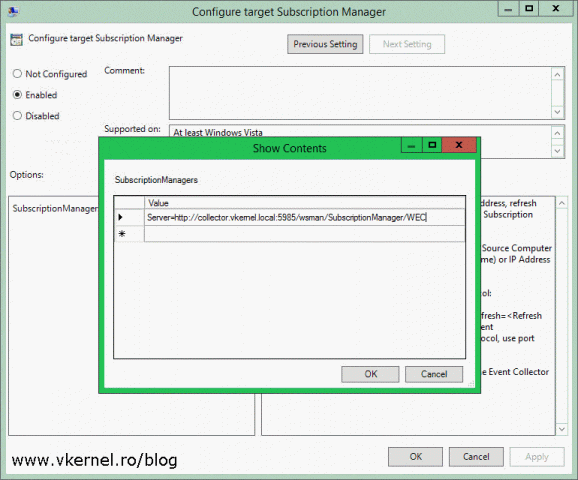
In the Value box, type the address of your collector computer in the following format then click OK.
Server=http://<Event Collectors FQDN>:5985/wsman/SubscriptionManager/WEC
HTTPS can also be used as the address here, but in order to work, we need to have certificates put in place on the machines. I will talk about this in a future article, for now just go with HTTP.
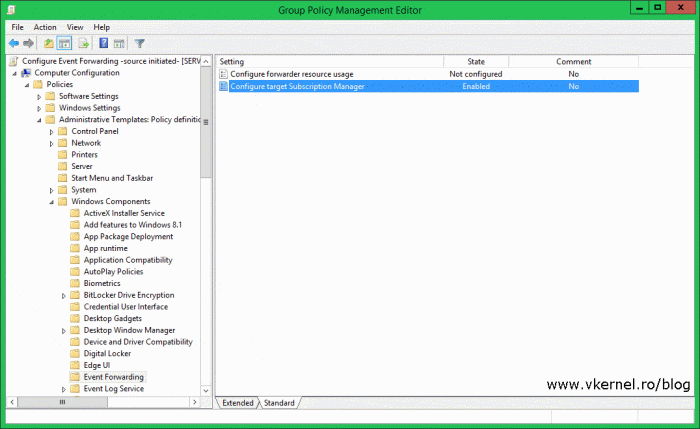
Now the policy setting should show as being enabled.
This completes the forwarders configuration, but we still have to configure the collector computer, so let’s move on and set this one up. From a command prompt, issue the bellow two commands to enable and start the WinRM service, set up the ports in firewall and to enable the creating and managing of subscriptions on the collector computer:
[notice]If you get the message that the WinRM service is already set-up and running, don’t worry, this is because you are using server 2012 or above. As I’ve said earlier, WinRM is already configured on this operating system version.[/notice]
winrm qc
wecutil qc
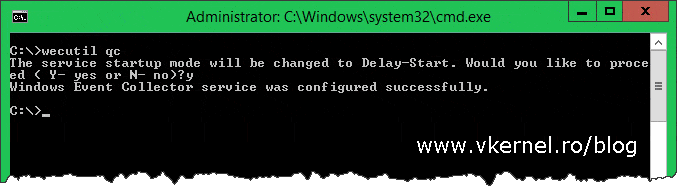 Now we can go ahead and configure subscriptions. From the Administrative Tools or Start screen open Event Viewer and navigate to the Subscriptions node. Right-click this node and choose Create Subscription.
Now we can go ahead and configure subscriptions. From the Administrative Tools or Start screen open Event Viewer and navigate to the Subscriptions node. Right-click this node and choose Create Subscription.
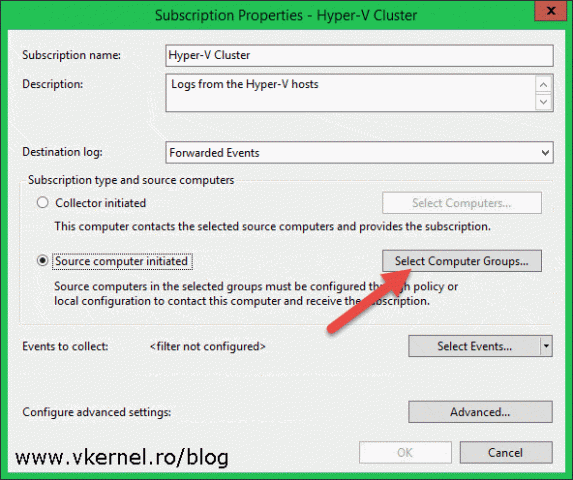
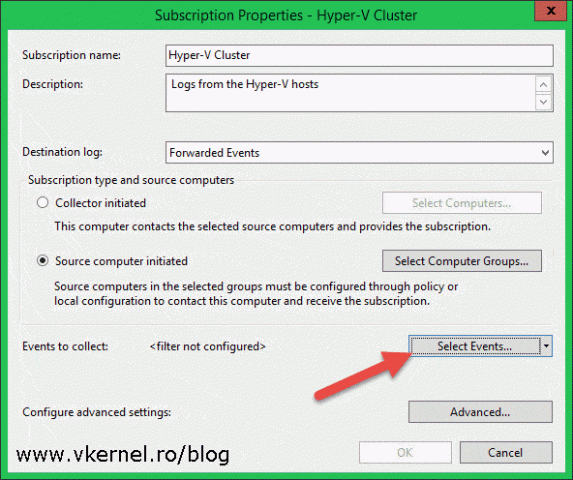
Give it a name and description, then from the Destination Log drop-down-box select where the forwarded logs should sit. Usually you will want to leave this at the Forwarded Events just so events are kept separate from the regular events. From the Subscription type and source computers section select Source computer initiated then click the Select Computer Groups button.
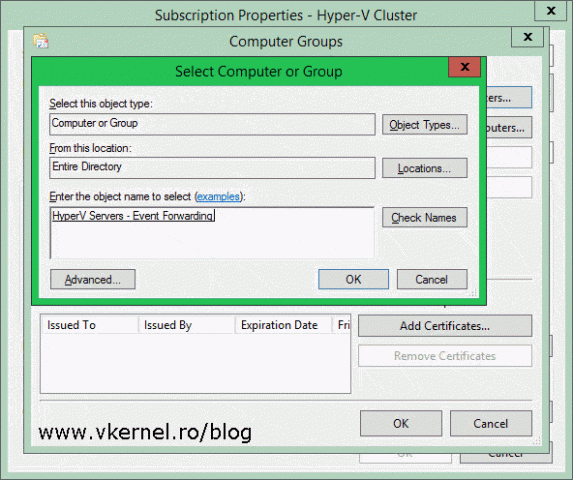
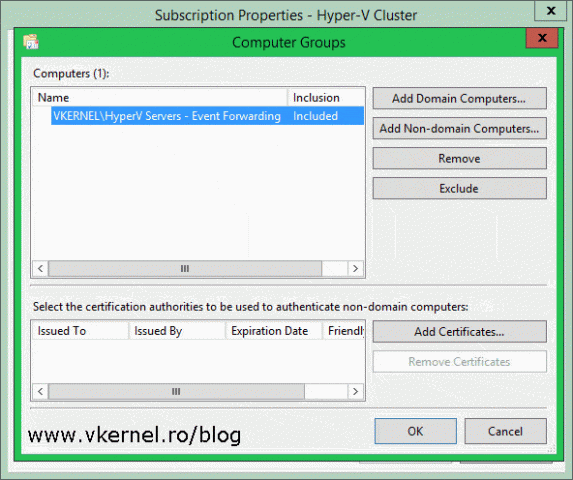
In the window that opens hit the Add Domain Computers button then search for the computers (forwarder computers) you want them to have access to send events to this collector. In the previous section where I discussed the collector initiated subscriptions I added a few computers in this list on by one. This is because that method is used for small networks, but here, we have more than a few clients. Imagine adding 200 servers in this list. Now that could take some time! To make it easy, we have two options: we either create a security group in AD and add our forwarder computers there, then add this group to the list, or we use the already built in Active Directory Domain Computers group which contains all the domain computers.
[notice]If you are thinking on using the second option, make sure you link the GPO (created earlier) that enables WinRM and Forwarding Events on the OU where the servers/workstations that you want them to send events are located. Do not link it to the root of the domain because all computers in your domain will forward events to the collector.[/notice]
Back on the Subscription Properties window click the Select Events button to configure which events should the collector keep.
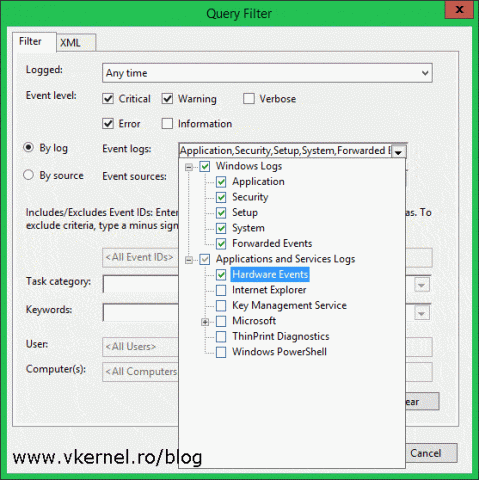
From the Event logs section select what type of events you need, then choose how you want them to be filtered, by log or by source. In the All Events IDs box you can also be specific and filter events by their ID. Click OK when done configuring filters.
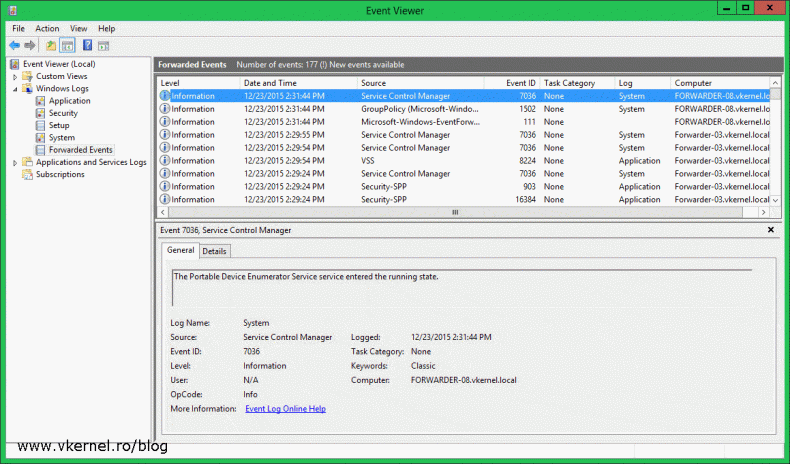
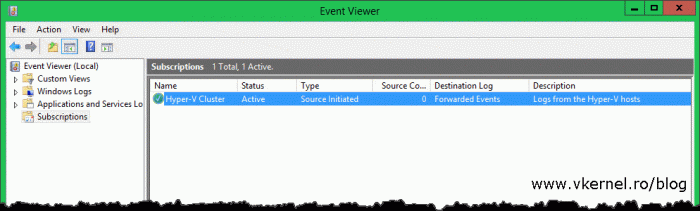
The newly created subscription should appear in the console,
and after a few minutes logs should start popping-in.
Event forwarding it’s a must have if a dedicated log collector software is not present in your infrastructure. Think about it, it’s free, you can set it up using Group Policy and it’s easy to configure. You can implement it on your domain controllers, or on some secure systems and you will be notified when an error happens, when someone logs in or gains access to the network. This provides you with a very powerful tool-set for disaster recovery and action identification. Pretty neat !
Want content like this delivered right to your
email inbox?
Hi thank you for this article.
Please can you point me to the location of the Event logs readers group am trying to add manually the account to the local Event Log Readers group on the forwarder computers
I just wanted to say thank you very much
I’m glad I could help.
Nice article. One important factor to keep in mind is that the security event log on domain controllers require are locked down so you may have to issue a special command at the powershell or command prompt to have acces to a DCs security event log.
Basically the network service account on the DC needs special channel permissions to the security event log
Here is a link to article where I had to run this command on my DC for my collector to pull the D.C. Security event log
URL – https://www.petri.com/configure-event-log-forwarding-windows-server-2012-r2
Thanks
Steve
Never happened to me. If the security permissions are set up right you don’t need that.
Hi,
This was really helpful.
However, I am trying to forward logs from a Non-AD host to a subscription server on my AD, but I am unable to see any logs in “Forwarded Events”.
I have skipped the below step as it requires me to add a forest :
” Now that WinRM is running and configured we have to “tell” the forwarding computers where to send their events and again we can use Group Policy or we can do this on a client by client basis by opening the local Group Policy Editor (gpedit.msc). No matter which option you choose, the policy settings are located in the same place. Since the source initiated subscription method is used in environments with a large number of clients, Group Policy will be the preferred choice.
Create a new GPO, link it to your OU where the forwarding computers are sitting then edit the GPO. ”
Could you please help?
Hi,
Event log forwarding is 99% of the time implemented in AD environments. In workgroups, is not implemented because of the small number of clients, but there are exceptions, like in your situation. There is a Technet article that can guide you do this. Hope this helps.
Hi.
It’s nice job. I have a problem, how to redirect collected events to another disk for example disk D:\EVENTS on Collector machine. It is possible? 😉
Thansk a lot.
Hi,
Never tried it but here are two links that might help you.
How to move Event viewer Logs to another drive connected to the system
How to move Event Viewer log files to another location in Windows 2000 and in Windows Server 2003
Keep forward! Thanks 🙂
Thanks for passing by…
Thank you for this helpful guide! The screenshots really help make everything clear.
It’s really useful share with complete steps !!
This is great, I am just started using event viewer to record user log in time, and found quite cumbersome if I have to do checking one by one remotely to each computer. Nice post, will try this as soon as possible. Thanks.
its nice sharing…!!!!
Thanks 🙂