Configure WSUS to use SSL
You have WSUS in your infrastructure, and now you need to implement SSL because you want to be sure that your clients are connecting to the right WSUS server, the meta data is encrypted, or you are just curious to see how it’s done. Configuring WSUS to use SSL is a straight forward process, and all you need is a certificate, and some IIS configurations. For this guide I have a single WSUS server deployment in a single forest/domain environment running on Windows Server 2008 R2 SP1. The certificate is issued by an internal Enterprise CA. Information on how to install an Enterprise Certification Authority can be found here.
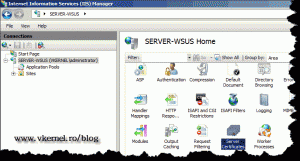
To get started, first we need to request a certificate for the WSUS web site, so open IIS, click the server name, then open Server Certificates.
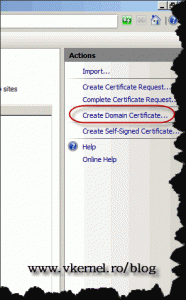
On the Actions pane click Create Domain Certificate.
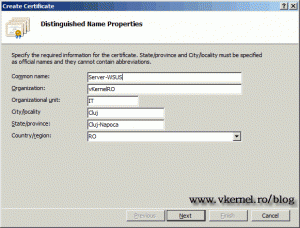
On the Common Name box we need to type the name we want appear in the certificate. I recommend to use either the name of the WSUS server, or the FQDN of the server. If you have external clients that use this WSUS server you need to type the FQDN (the internet public address) in this box. But now things are getting a little complicated, because you either need to create a split-brain DNS or create a SAN certificate that includes the FQDN and the WSUS server name. Complete the rest of the boxes and click Next.
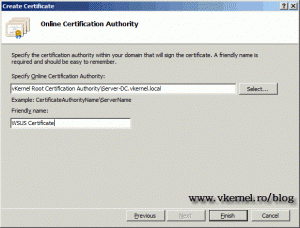
Select your internal CA by clicking the Select button, give the certificate a friendly name and click Finish.
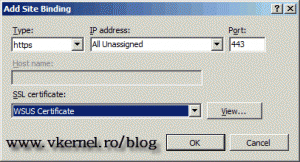
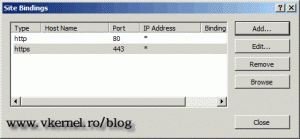
Now that we have our certificate in place we need to add this certificate to the web site. Expand Sites and click the Default Web Site. On the Actions pane click Bindings. Now click Add, on the Type drop down box select https, and your WSUS certificate on the SSL Certificate drop down box.
The next step is to enforce SSL encryption on the following virtual roots:
• SimpleAuthWebService
• DSSAuthWebService
• ServerSyncWebService
• ApiRemoting30
• ClientWebService
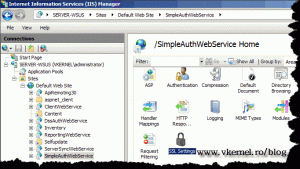
Select SimpleAuthWebService and open the SSL Settings.
Check the box Require SSL, and make sure Ignore is selected under Client certificates. Click Apply on the Actions pane to save the changes.
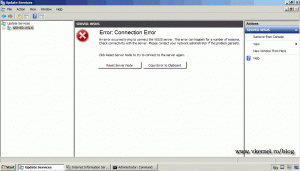
Repeat this operations for the rest of the virtual roots, mentioned before. By now, the connection to the service should be lost, and a connection error message appears in the WSUS console. This is because the console is trying to connect using the default port 80.
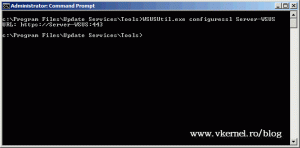
To fix this, open a terminal and issue the following command from <WSUS Installation Folder>\Tools:
WSUSUtil.exe configuressl FQDN of the software update point site system> (the name in your certificate)
in my case is:
WSUSUtil.exe configuressl Server-WSUS
I managed to get access to the console only after a system restart, but after restart I am connected using SSL.
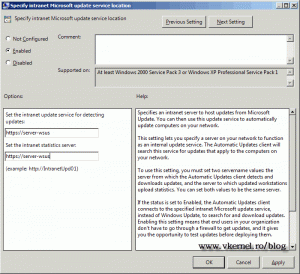
The next step is to point your clients to the correct url, by modifying the existing GPO or creating a new one. Open the policy Specify intranet Microsoft update service location and type the new url in the form https://YourWSUSserver.
To see if all this is working correctly, go to one of your clients and force the new policy to apply using gpupdate /force.
The gpupdate /force command will just download all the GPO’s and re-apply them to the client, it won’t force the client to check for updates. For that you need to use wuauclt /detectnow.
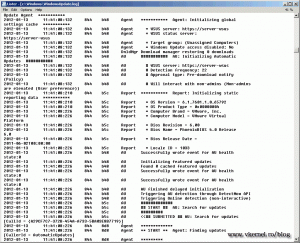
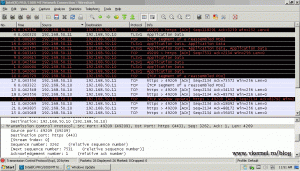
First let’s see the client update log
WireShark is showing me that an encrypted connection is made between the client (192.168.50.11) and the WSUS server (192.168.50.10),
and updates are downloaded by the client.
Want content like this delivered right to your
email inbox?

Thanks for the walkthrough Adrian,
Built out a Certificate Authority & WSUS server from scratch to mirror my production environment. (Pushed out the root CA Cert to clients in the test environment)
Followed your article + confirming steps from Microsoft KB article here:
https://learn.microsoft.com/en-us/windows-server/administration/windows-server-update-services/deploy/2-configure-wsus#23-secure-wsus-with-the-secure-sockets-layer-protocol
– bind cert in IIS
– set specified IIS directories to require SSL
– run “wsusutil configuressl ”
I still receive a ‘cannot connect to please make sure Post-Installation task…. etc etc etc
Even modified the app pool per these instructions:
https://ch3rmes.medium.com/fix-wsus-connection-error-reset-server-node-on-windows-server-2012-2012-r2-2016-7a2b88cdc6e6
I have confirmed that *wsus* services are running as well & ports are open, the WSUS configuration is out of excuses to work & I am out of ideas.
You seem to know what may / may not be the issue, so any assistance would be appreciated.
Hi,
Sorry for the delay. Can you post a screenshot so I can see the error?
hi
does those steps
but error still comes up
need help
from Oliver
Hi Oliver,
Please use the Contact form, and I will get back to you and try to fix this.
I know this is a really old article but you seem to know your stuff. Could you tell me if it is possible to use WSUS without using an unsecured connection? So that even the updates are downloaded over SSL? I have a public facing server so users not on the network will still be updated so am trying to make it so someone can’t inject an update in transit.
Hi,
If you follow this article you can set up WSUS with a secure connection between WSUS and your clients. Go ahead and try it.
I think Tracey is asking how you secure the content downloads as well as meta data communications. For instance, I see both ports 8530 and 8531 being used for communication, but the large data pulls seem to be on 8530 only. So, I’m assuming the actual packages are downloaded on the http port.
Sorry my bad. By design WSUS does not encrypt content download between the server and clients, but it DOES encrypt the metadata. You cannot set up the entire WSUS Web site to require SSL, just the specified virtual roots mentioned in this article. I hope this answers your question.
Is it possible to use SSL on WSUS Server but keeping the clients point to a url on port 80?
Hmm, I don’t know about this because I never try it, but if you are willing to test this, please put a comment in here with your findings.
Great guide. I have done this using port 443 and clients are contacting and updating fine, I can access WSUS admin console from the server itself with no issues. My only issue is I get these periodic errors in the event logs. 13042, 12002, 12012, 12032, 12022, 12042, 12052. All saying that DSS Authentication Web service or whatever other random service is not working.
Any idea how to get rid of these infernal errors? Again, everything seems to be working.
Post the error here if is not to long so I can take a look at it.
I think every article on how to enable SSL for WSUS should end with these two steps:
1. Run C:\Program Files\Update Services\Tools>wsusutil checkhealth
2. Look in Event Viewer for Event ID 10000 in the Application Log. Check you don’t have errors with all 7 web apps (12002 – 13042).
I have WSUS running on Server 2019 Core from a remote SQL server, and a fresh Server 2019 GUI build on local WID, and as soon as I enable SSL I get the exact same issue. The errors appear about every 6 hours, and apart from remote consoles having to reconnect it is still working. Many other people on the internet have it, but nobody had found the cause or how to solve it. So far I tried increasing the AppPool memory. For now I have turned off requiring SSL, but left the clients and consoles configured to use 8531.
Hi,
Thanks for the tip, much appreciated.
Adrian,
I need some help getting my WSUS off the ground. I’ve used your guide to try and configure WSUS using SSL and one issue I’m somewhat confused about is how to setup the certificate. At our organization, we want to be able to connect to our WSUS server from home w/o having to fire up our VPN. We have the split brain DNS entries setup and I can connect to the update console using the local machine name.
Hi,
First of all you will need a public commercial certificate; or if you want a FREE thing import the root certificate from your internal CA to your home clients. The second thing is open the ports 443 and 80/8530; it depends witch one you configured during the WSUS wizard. The third thing is to configure the home clients; follow this article. Have fun.
Hi!
Please add information that port for SSL connections to WSUS 443 or 8531 must be opened on WSUS server also. By default the rule on Windows Firewall that open this port is disabled.
Hi,
Indeed, I did not said that because I taught it was obvious. Thanks anyway.