Steps to check if Domain Controller was properly promoted
Many times after we promote a server to a domain controller, we want to know if it was promoted correctly. We want to know if everything is working fine, and if you are just starting in the Active Directory Services filed, you will need to know what and where to check. There are quite a few steps to go trough, but once you do this a few times it will be like second nature.
If one or more of these steps area failing and don’t see the expected positive result, I recommend trying to troubleshoot or even re-build, because if it’s left in an incomplete or broken state there will be a lot of issues later on. It might even break the other domain controllers since they sync/replicate with one another.
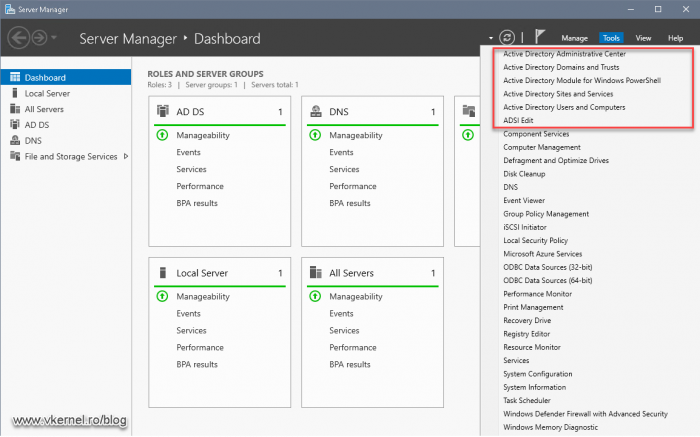
The first check that we can do is also the fastest and easiest one. On the domain controller that we just promoted, open Server Manager and click the Tools menu. Here we should see all of the Active Directory snap-ins installed and ready to be used.
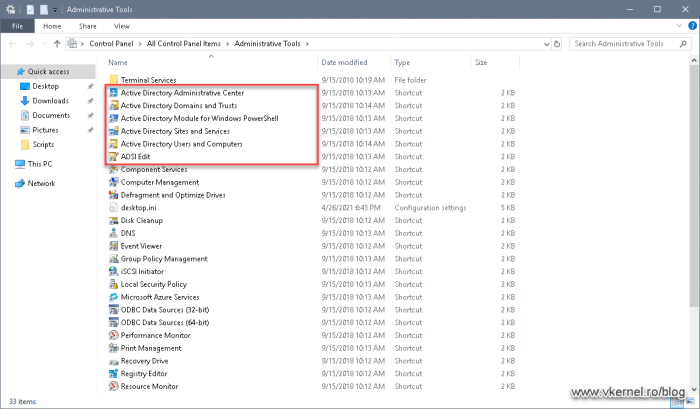
The same snap-ins should also be present in the Administrative Tools area from Control Panel. If they are not here, they were either not installed or the domain controller promotion failed.
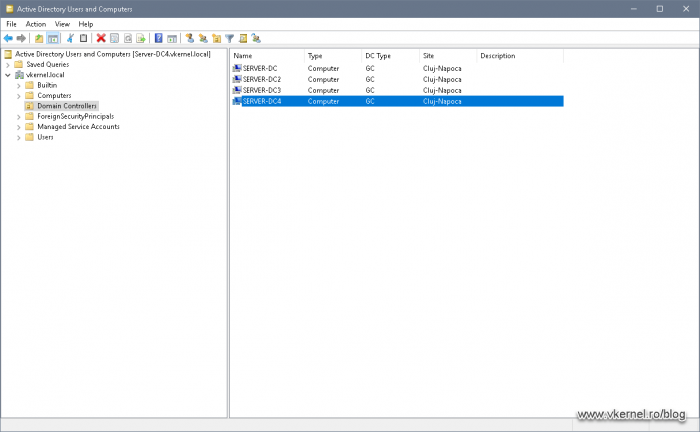
Since we still have our Server Manager open, go to the Tools menu again and launch the Active Directory Users and Computer console. Expand the domain name and click on the Domain Controllers organizational unit (OU). This is the OU where all of the domain controllers in the environment/forest are sitting. If we take a look at the right-hand side, the domain controller that was just promoted should be in the list.
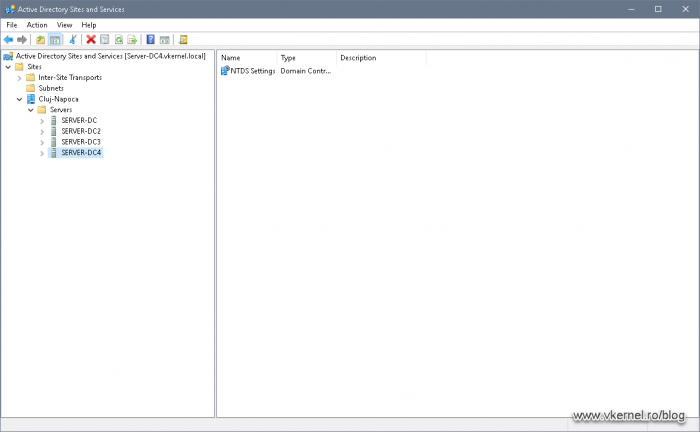
The next check is done by opening the Active Directory Sites and Services console, and see if the domain controller is listed in the site it was assigned to. This assignment is usually automatic if your sites and services subnets are properly configured.
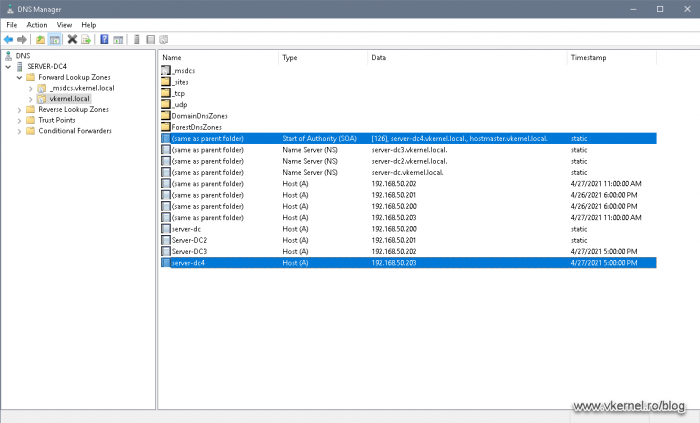
Now we need to open the DNS Manager console and see if the proper records were created. Bear in mind that this only applies if your domain controller is also acting as a DNS server, because in many large environments this service is offloaded to dedicated hardware appliances.
Once the DNS Manager console opens-up, check if the A and NS records exist in your DNS zone.
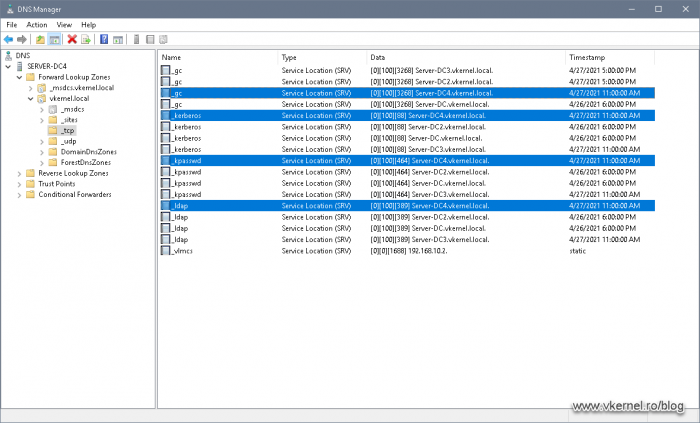
Also, if we expand the zone name and click the subfolders, we should have the proper SRV records created inside them.
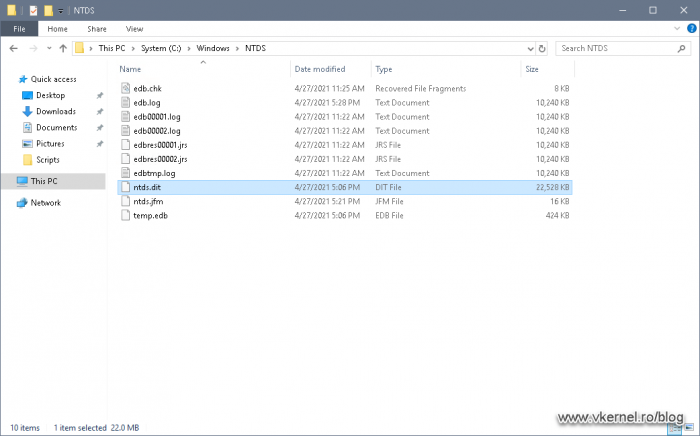
The next check is done by opening Windows Explorer and browse to C > Windows > NTDS. By default, this is where the Active Directory database and logs are saved. We should have the database file ntds.dit, along with some other files like *.log -transaction log files-, edb.chk -checkpoint file used when backing up the Active Directory database-.
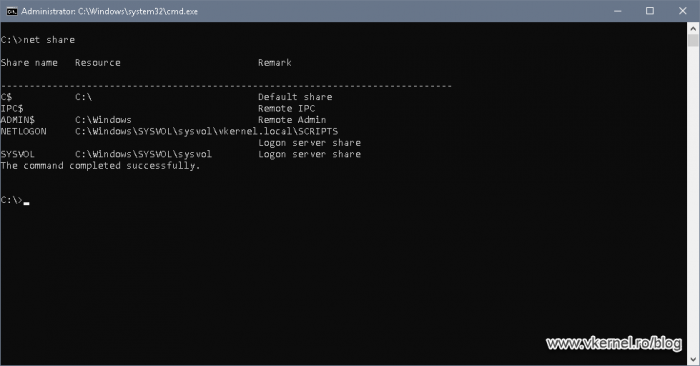
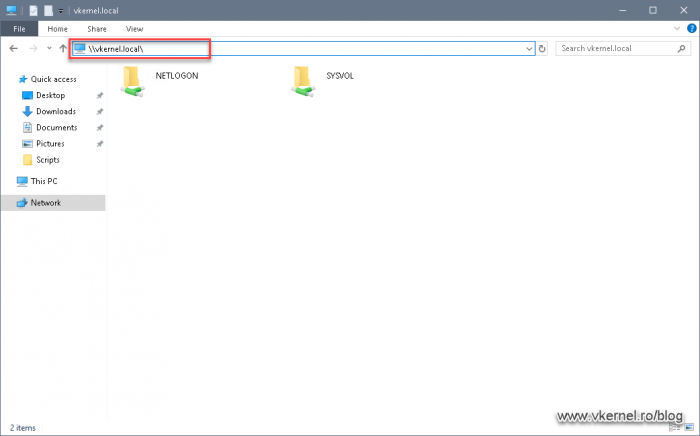
Now we need to open a command prompt or PowerShell window and issue the net share command. This will list all the shares the domain controller has, and we should have two important ones listed here: the the NETLOGON and SYSVOL one.
The same can be accomplished by using a UNC path to the domain name (\\domain.name\). We should see the same two shares listed in the Explorer window. These shares are used for logon scripts and group policies delivery to domain members.
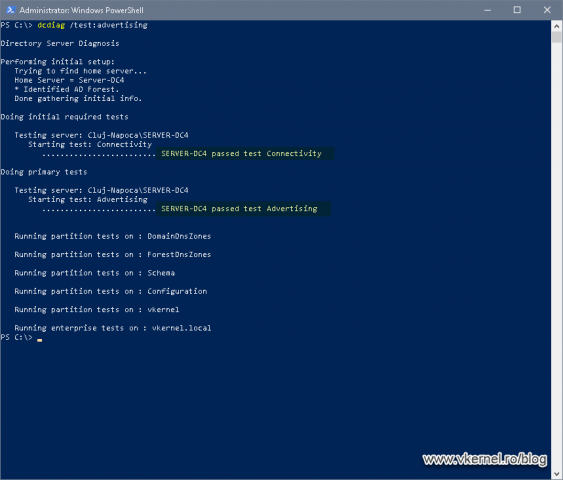
Moving forward, we need to open again a command prompt or PowerShell window and use the bellow command line to analyze the state of the domain controller in the forest.
dcdiag /test:advertising
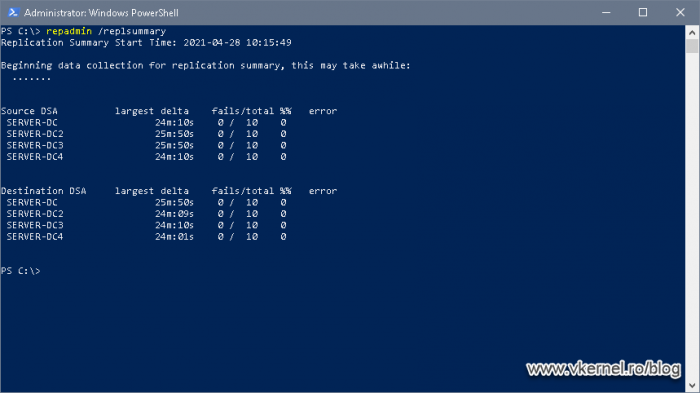
In the same PowerShell or command prompt window we can also test the replication of our latest promoted domain controller with the rest of them -if many- by issuing the bellow command line. If the number is zero in the fails column, then everything is working fine, if not, we will be present with the error so we can treat it.
repadmin /replsummary
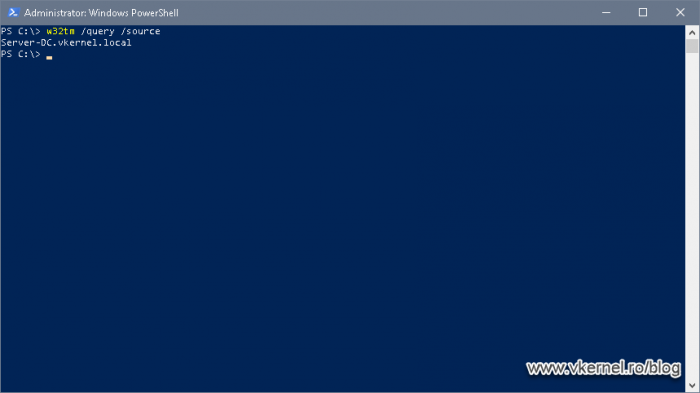
Because time it’s very important especially in a domain environment, we need to make sure that our domain controller is synchronizing its time from the PDC or external if you only have one. By issuing the bellow command we can very easily find out the source of time. More information can be found in a previous article of mine on how to configure a time source for domain controllers.
w32tm /query /source
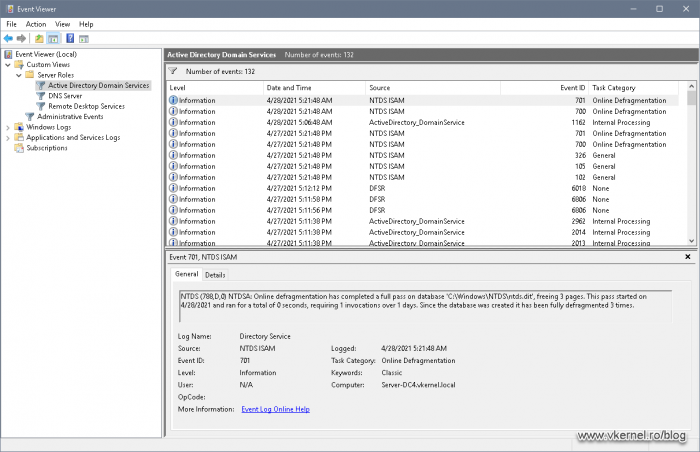
The last check that I can think of is to take a look at the logs. If we open Event Viewer and expand Custom Views > Server Roles > Active Directory Domain Services we can see all the logs we need in order to identify if there is something wrong with our Directory Services service. This view it’s a custom view which includes the File Replication Service, DFS Replication, DNS Server, Directory Service and Active Directory Web Services. As you can see it includes a lot of logs into a single view, which in my opinion it’s a great thing.
Summary
Checking the domain controllers it’s a task that must be done regularly not only after Active Directory was installed. In large environments there are tools that do this kind of tasks, but in the small ones there are either done manually or using scripting.
If you are using some other type of tools or commands to verify your domain controllers that I missed in the article, please let me know in the comments area. Hope this helps!
Want content like this delivered right to your
email inbox?


This is really good
Thank you. Glad I could help.