Replacing VMware vSphere 5 Web Client Server default (self signed) certificate
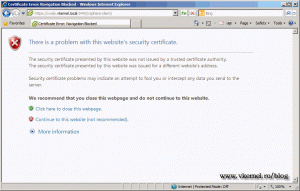
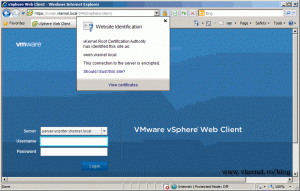
Yep…I’m the kind of guy that does not like those red bars in IE, and I created this post because I just got another one. Right after I finished installing VMware vSphere 5 Web Client Server and opened the web console to register one or more vCenter servers, I got the certificate error page in the browser. Is all about trust, and right now there is no trust since the certificate is self signed. In this guide I will request and install a proper certificate for VMware vSphere 5 Web Client Server from an internal Windows CA.
If your vSphere Web Client Server is accessed from the outside, I recommend you install a commercial certificate, or you’ll have to install the root certificate of your internal CA on every client that connects to the vSphere Web Client Server.
To test this I have a Domain Controller running Windows Server 2008 R2, and one vSphere 5 Web Client Server joined to the domain. To create the certificate private key I will use OpenSSL, so let’s start.
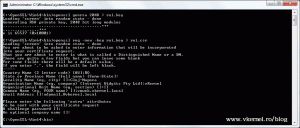
Open a terminal and go to the bin directory of OpenSSL, then type the following commands one at a time, and don’t set a challenge password at the end:
openssl genrsa 2048 > rui.key openssl req -new -key rui.key > rui.csr
Complete the required information and be very careful at the Common Name line. You need to type the FQDN that you and your clients will use to connect to the management server. In this example I used the internal FQDN of the server, since I am not going to publish this on the internet.
If you want to, or if you have the budget, you can use SAN certificates; they work great, I tested them. That way you can include the NetBIOS name, internal FQDN name, and the external FQDN name of the server/site.
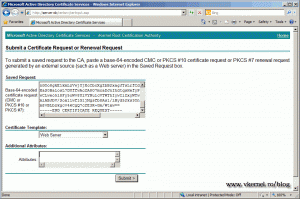
Now from your OpenSSL bin directory open with notepad or any other editor the rui.csr file and copy the request to your clipboard; be sure not to modify it in any way. On the internal CA Web page choose Request a certificate > advanced certificate request > Submit a certificate request by using a base-64-encoded… then paste the content (the request code from the rui.csr file) from your clipboard in the Saved Request box and choose Web Server from the Certificate Template. Click the Submit button.
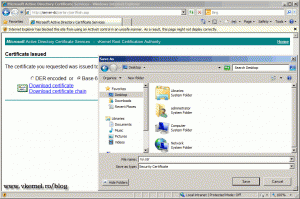
Download the certificate using Base 64 encoded option, and name the certificate rui.cer. It’s easier in the next section if you name it like this.
Copy the certificate in the bin directory of OpenSSL, then issue the following commands:
openssl x509 -in rui.cer -out rui.crt openssl pkcs12 -export -in rui.crt -inkey rui.key -name rui -passout pass:testpassword -out rui.pfx
Be careful, the password for the certificate (.pfx file) needs to be “testpassword” or is not going to work; the vSphere Web Client service will stop. I struggled with this for hours, until I realized what the problem was.
Open Explorer and browse to C:\Program Files\VMware\Infrastructure\vSphere Web Client\DMServer\config\ssl\. Here you can see the default certificate and private key. Backup these files and paste those we created and located in the bin directory of OpenSSL. You need rui.key, rui.pfx, rui.crt.
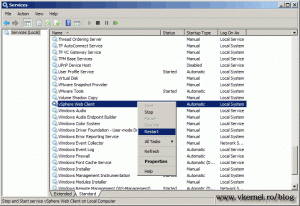
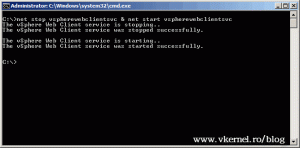
Now open the Services console and restart the vSphere Web Client service, or use the command line:
net stop vspherewebclientsvc & net start vspherewebclientsvc
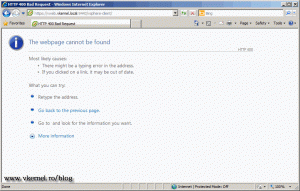
After the service is up and running again, connect to the vSphere Web Client Server using the address https:\\ServerFQDN:9443\vsphere-client. If you get the 400 Bad Request error just wait a couple of minutes, then refresh the browser.
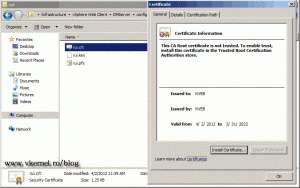
Now it works, and the web site is trusted and secure.
Want content like this delivered right to your
email inbox?





worked a treat !! thanks, great guide.