Delegate Access Control and Management in Hyper-V
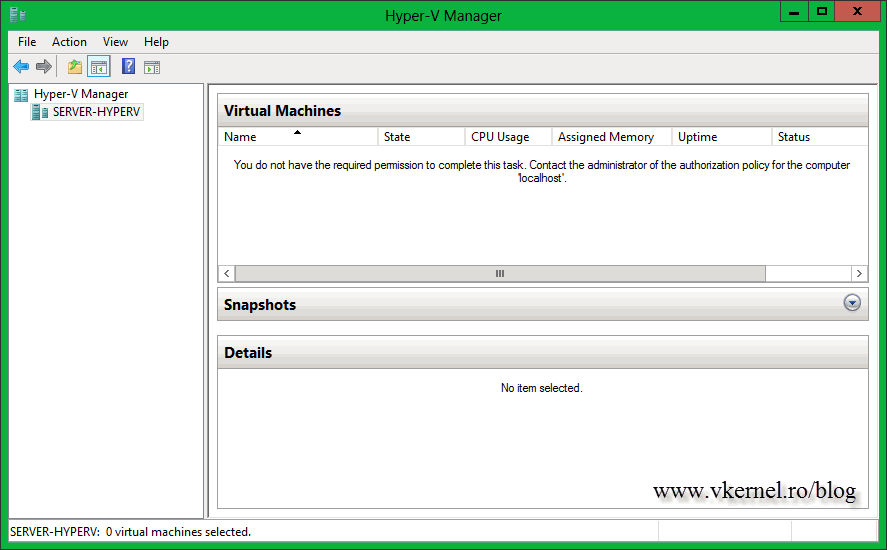
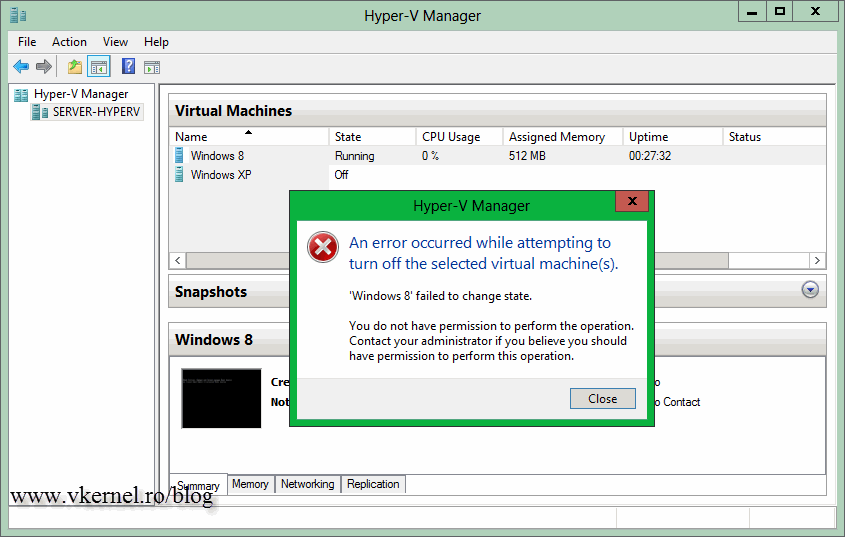
In a virtual environment security is vital, because you can’t give full permissions to everyone. Imagine just for a moment if a user connects to one of your Hyper-V servers, and by mistake power’s off some of the VM’s, or even worse, deletes them. But the user still needs access to his VM, right ? Yes, that’s right, so you decided to remove his account as local administrator. Now you have another problem, the user can’t even connect to the Hyper-V service, he gets the message: “You don’t have the required permission to complete this task. Contact the administrator of the authorization policy for the computer…“.
There is another way by which you can restrict what the user can do and cannot do once is connected to your Hyper-V server(s). For that you need to create delegation of administration by using the Authorization Manager console.
[notice]Update – 17.Oct.2014: This feature (azman) has been deprecated starting with Windows Server 2012 R2 based on the Microsoft article Features Removed or Deprecated in Windows Server 2012 R2.[/notice]
To start, log in to one of your Hyper-V servers and go to Start > Run. Here, type azman.msc and press Enter.
Don’t worry if you see me do this on a 2012 server, it works with 2008 and 2008 R2 also. I just like to work with new stuff.
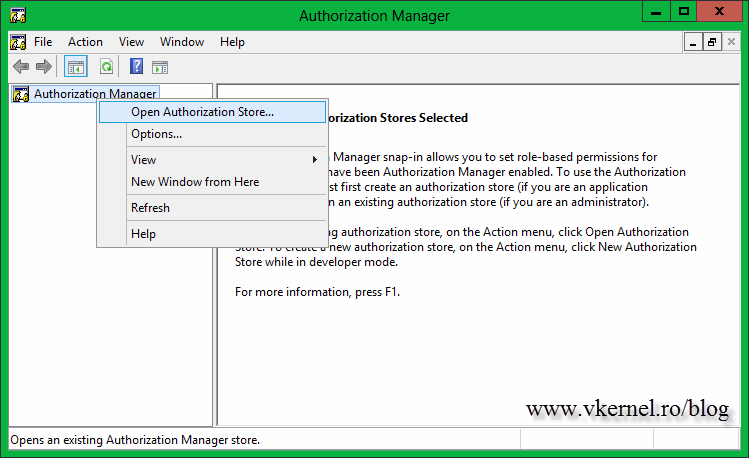
Once the console opens, right-click Authorization Manager and choose Open Authorization Store.
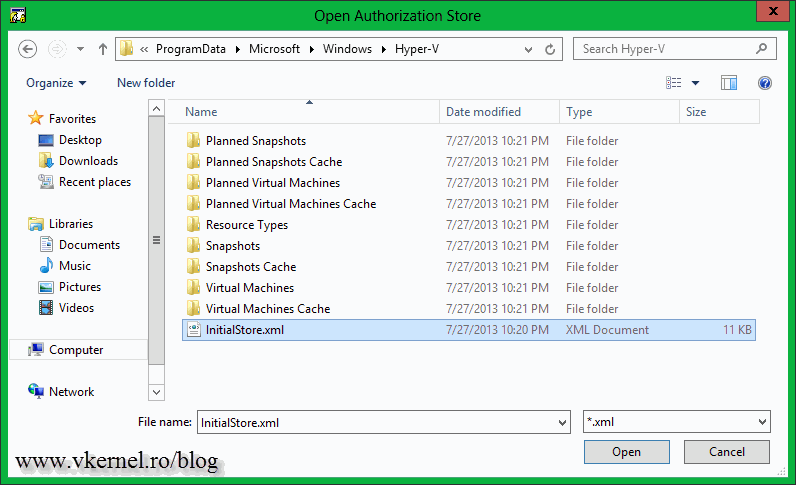
Leave the XML file option selected, click Browse, and go to C:\ProgramData\Microsoft\Windows\Hyper-V. Highlight the InitialStore.xml file and hit Open then OK.
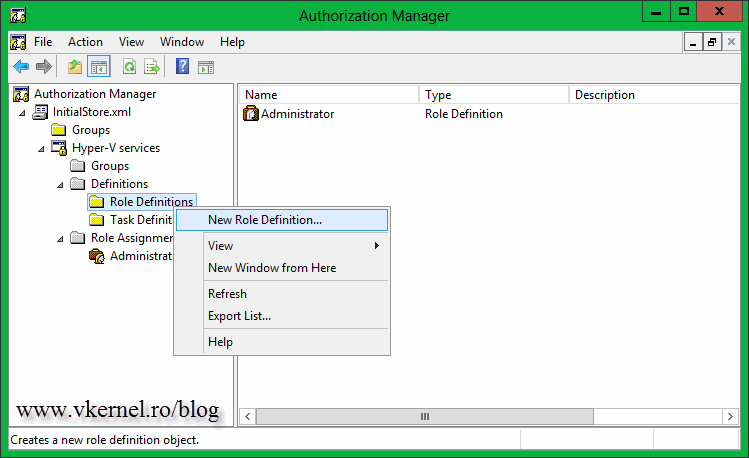
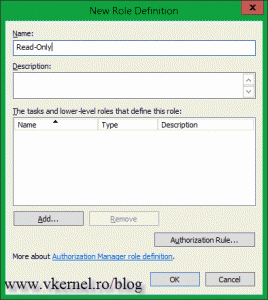
If you expand Hyper-V services and click the Definitions folder, you will see two other sub folders called Role Definitions and Task Definitions. The first one is used to create groups to control access to Hyper-V, and the second one to centralize the permissions settings for the VMs (shutdown, power on, snapshot, etc). Right-click the Role Definitions folder and choose New Role Definition.
Give the group a name then click OK. I’m going to call mine Read-Only, because I will use it to give users only read access to VM’s. So everyone that is part of this group and connects to my Hyper-V server using the Hyper-V Manager console, they will not be able to change VM’s and Hyper-V settings, or even power on or off VM’s.
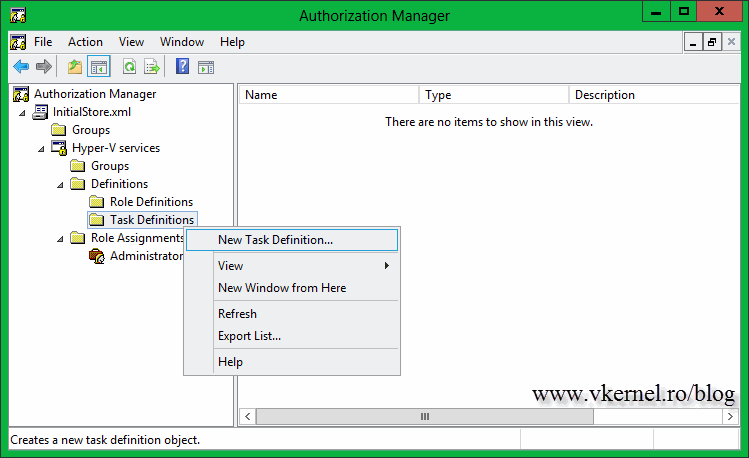
Now go to the Task Definitions folder, right-click it and choose New Task Definition.
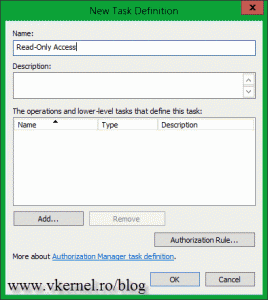
Give the task definition a name then click the Add button. Ignore the message that pops-up and hit OK to dismiss it.
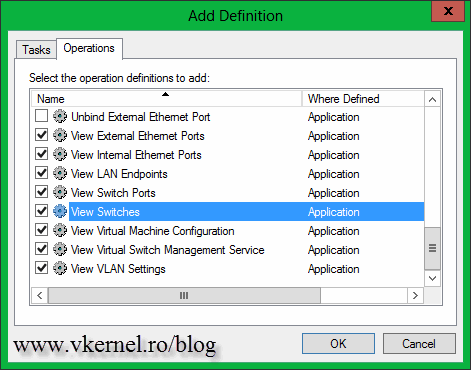
On the Operations tab check everything that starts with View (at the end of the list), this is if you want your users that are part of the Read-Only group to view your switches settings or any other configuration. If you also want your users to see what VM’s are running on your Hyper-V server(s) you need to check the first two definitions from the list. Don’t close the window yet, because there is a definition, a very important one, that if you don’t enable, your users will not be able to connect to the Hyper-V service. They will get message that you read at the beginning of this guide.
The definition is called Read Service Configuration. Check the box next to it then hit OK;
and OK again.
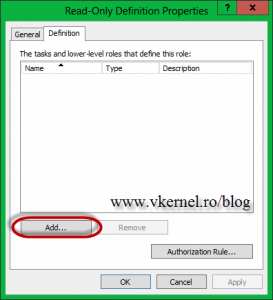
Go back to the Role Definitions folder and open the properties of the Read-Only group (right-click > Properties). On the Definition tab click the Add button.
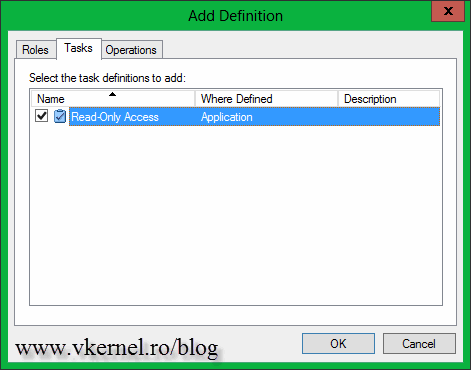
On the window that just opened, the Add Definition window, go to the Tasks tab and check the Read-Only Access definition created just a minute ago. Click OK twice.
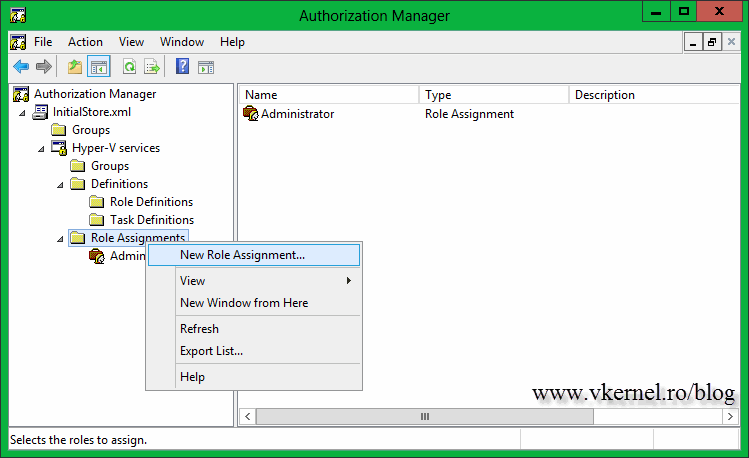
The final step is to assign an Active Directory or local group or user to the role definition we just created. For that right-click the Role Assignments folder and choose New Role Assignment.
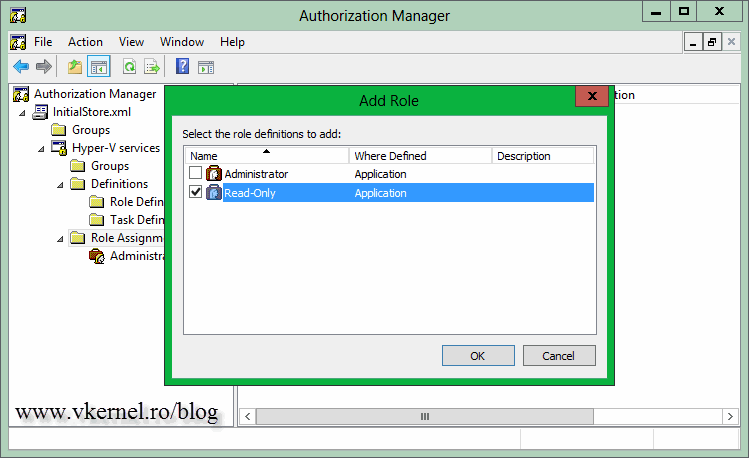
Check the Read-Only role definition then hit OK.
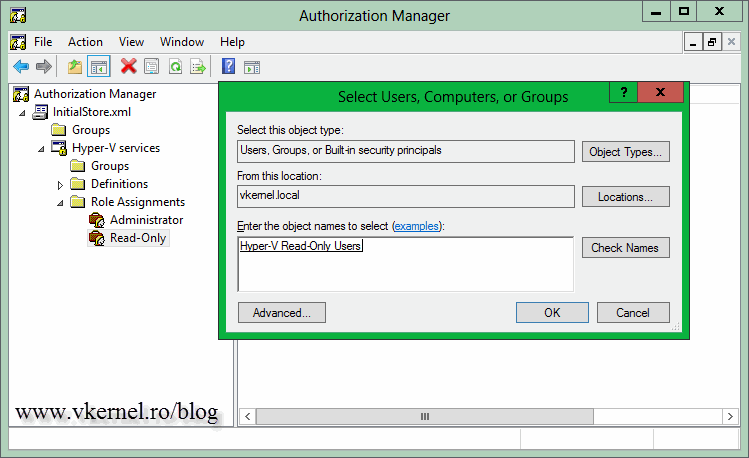
Now right click the group and choose Assign Users and Groups > From Windows and Active Directory.
Type the AD user-name or group and click OK. I recommend you create a security group in AD (like in this example) and work with that. Then when you need to give read-only access to your Hyper-V server(s) to another user, all you have to do is add his/her user account to this security group.
Now let’s do some testing. Log in with one of the accounts that is part of the Read-Only group, open the Hyper-V Manager console and try to modify some settings or power off a VM; anything. As you can see, all the operations are failing, because the user does not have access to modify them.
All you have to do now is create the desired tasks, roles and definitions for your users. This way, they can do their jobs without compromising availability or security.
Want content like this delivered right to your
email inbox?




Windows Server 2012 R2 not working for me either.
You do not have the required permission to complete this task. Contact the administrator of the authorization policy for the computer ‘localhost’
Did everything 100% right 5 times.
I think Microsoft changed something on their Hypervisor, but I need to look into it and update the article.
This does not work on Server 2012 R2. AzMan has been deprecated, but there is nothing to replace it. I have been trying to get this to work for over a month now, and so far I keep coming up empty handed.
Hi,
Yes, you are right, azman has been deprecated starting with 2012 R2 (article updated), and right now I could not find a replacement. Let’s hope Microsoft thinks of something.
Has anyone tried this on 2012 or 2012R2 server?
I tried it on windows server 2012 R2 but I did not work. Its keep giving me the same error.
Hi,
Never had the chance to do this on a 2012 server. I will and I will update the article or create a new one just for 2012.
I used the read only access method found elsewhere, and that worked ok (by creating a new role and definition). Thanks
It is not working for me either.
It does not work if I add my non administrator user account to the Administrators Role assignment as well??
Try and create a new role and give it administrative rights then add your non-administrator account to this role.
This tutorial is great, but unfortunately, doesn’t appear to work, or you’ve left out some key steps.
I’ve followed this to a T and added a normal account to the AD Security Group (No Administrative access on local box…we cannot allow this for delegation of VMs).
I granted remote desktop access to the same group so we are not dealing with remote connectivity or firewall issues.
I can login directly to the server with the account but when launching the Hyper-V Manager directly on the server, This is the message that appears:
You do not have the required permission to complete this task. Contact the administrator of the authorization policy for the computer ‘localhost’
Hi,
I can tell you that is working, I did this at my workplace. Create a test environment and do it again.
Uhm, No, Sorry.
I setup a brand new environment and this still does not work, unless you make the person or security group a local admin, which defeats the purpose.
I really, need something else, other than “do it again”.
Let me look into it and I’ll get back to you.
Just tested again and it works great. There is something you are not doing right. Make sure the security group (from your AD environment) is added to the Role Assignments group in Authorization Manager. Also the security group needs to have Read Service Configuration (in Tasks Definitions) right.