Working with VMware vCenter permissions
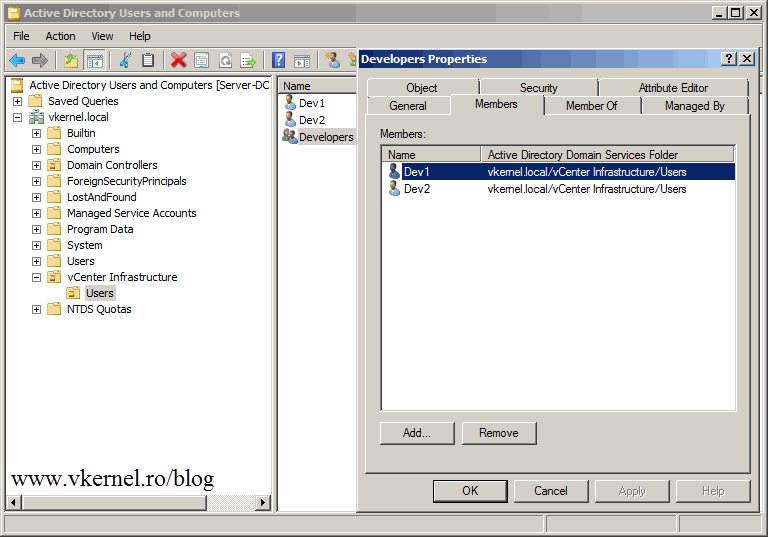
I wanted to extend my previous post and get in to some deep stuff with permissions in vCenter. It’s an important topic because there are a lot of times that users or some developers need access to their VMs but you don’t want them to mess with the all infrastructure. My vCenter server is joined to a domain, and all users in this lab are AD users not local ones. I’m a group guy, so I don’t like to give permissions directly to users, I like to put them in groups and give permissions to those groups. First, let’s create a group in AD called Developers, then we are going to put in this group the developers accounts that need access to vCenter.
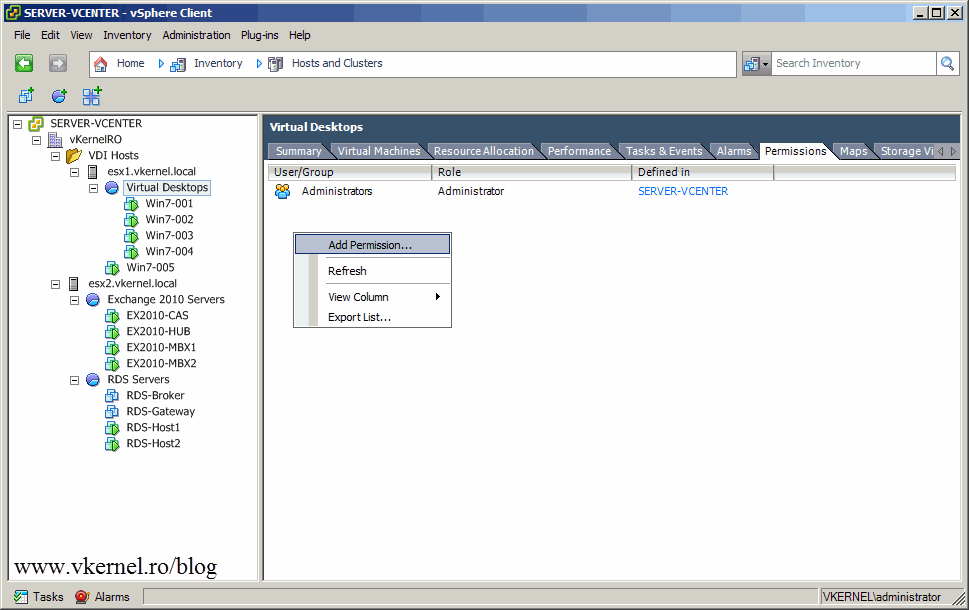
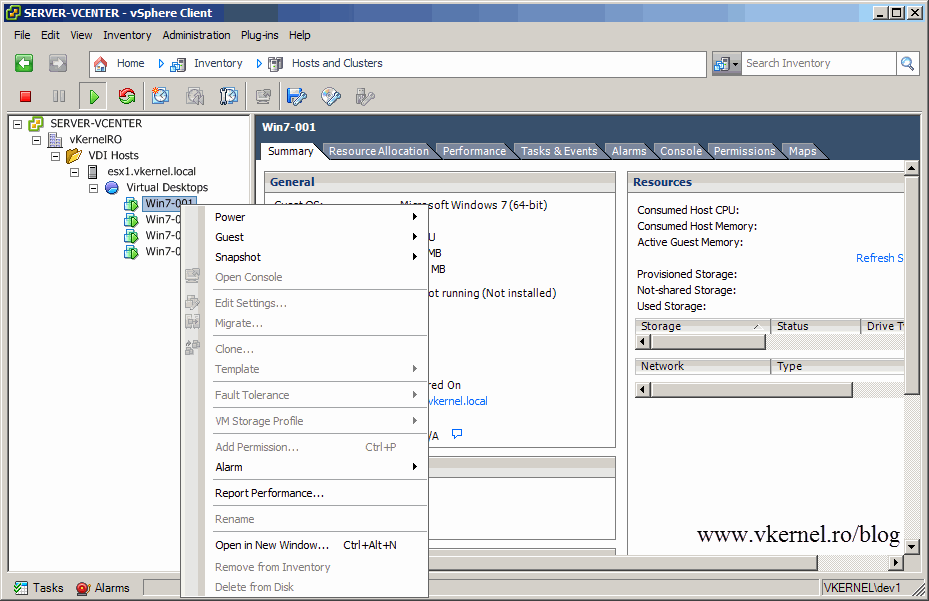
Now log in to vCenter using your administrative account. I created a Resource Pool for the developers workstations, first because I don’t want those workstations to consume to much resources on the ESXi host, and because I don’t want those developers to see all the vCenter infrastructure. Go to the Permissions tab, right-click somewhere on the white space and choose Add Permission.
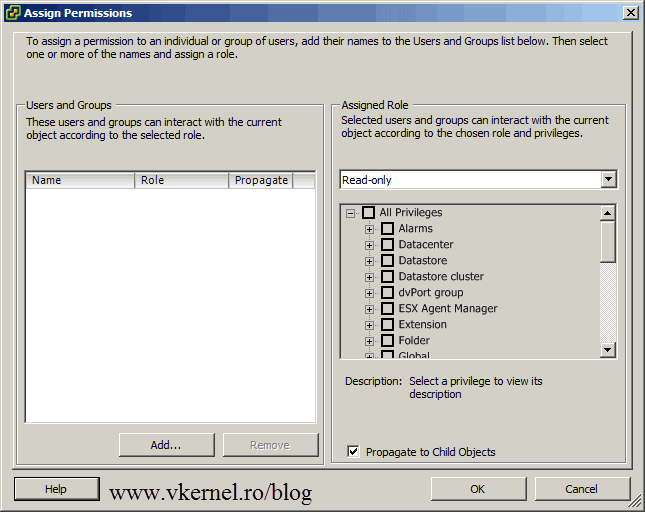
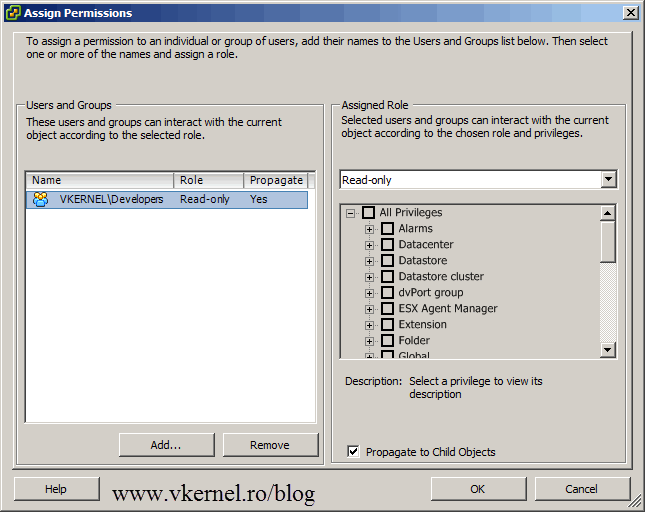
Click the Add button, so we can select the users/groups to assign permissions to. On the Domain drop-down box select your domain, then click the Developers group we created earlier and hit the Add and OK button.
Right now this group has only Read Only permissions. We want to give more permissions to developers, like power on/off the VMs, create and restore snapshots, but as you can see we can’t modify the roles, not from here anyway. To modify or create new roles we need to go to the Roles section. Click OK here so we can add the Developers group to vCenter, but we will return to change the permissions.
Click the Home tab then the Roles icon under Administration.
Here we can clone an existing role, or create a new one. Let’s create a role for those developers from scratch. Click the Add Role button from the top.
Give the role a name, then set the permissions. We want developers to be able to power on/off the VMs, create and restore snapshots. Go to Virtual Machine > Interaction, and Virtual Machine > State sections and check the necessary boxes. Click OK when you’re done.
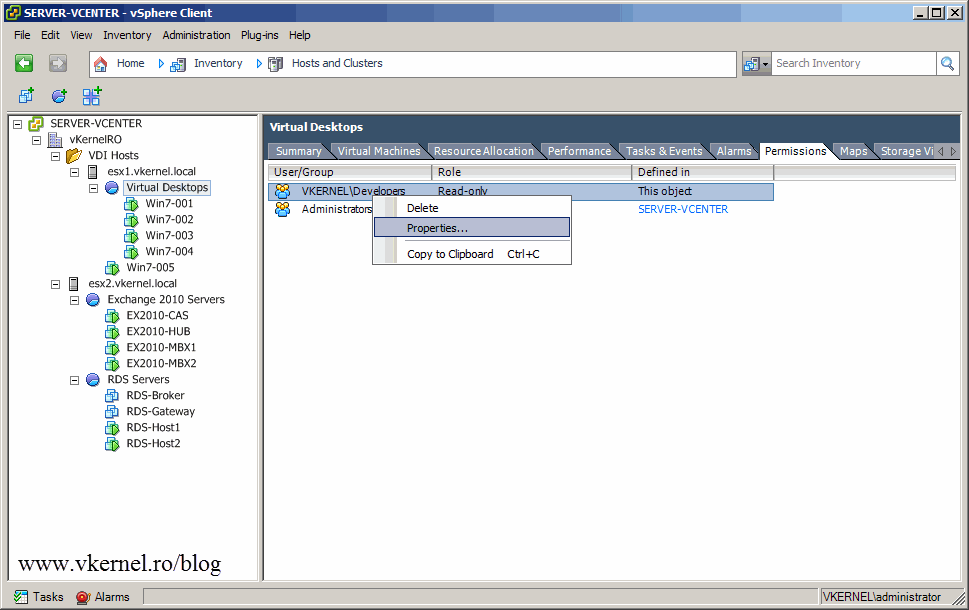
Back to our Permissions tab, right-click the Developers group and chose Properties. From the Change Access Rule window select the Developers role we just created and click OK.
Let’s test and see if it works. Open the vSphere Client and log in to vCenter using one of those developers accounts.
Using this account you can’t see all the infrastructure, because we set the permissions only on the Resource Pool, so only that Resource Pool and what’s under neath can be seen. Permissions were propagated.
Try to create a snapshot, then rename it, then delete it, see if it works. If it works you can send an email to the developers team to log in. If they need more permissions, you can just go to the Developers role in vCenter and edit the permissions role.
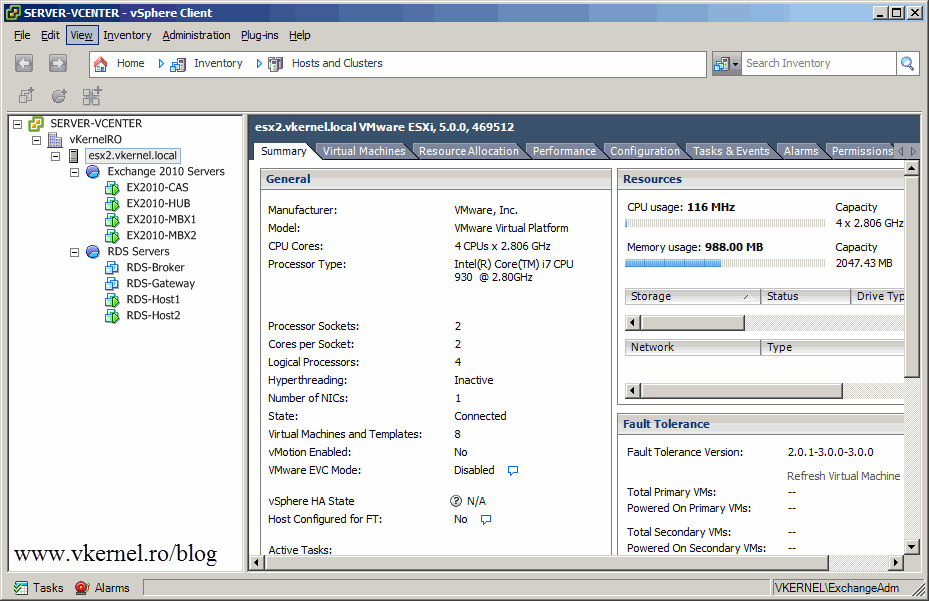
You can assign permission to folders, ESXi hosts, clusters practically on every object present in the vCenter inventory. Now I’ve created in AD a group named Exchange Admins, and put some users in it, and in vCenter a role named Exchange/RDS. The admins will also take care of the RDS infrastructure, so I will need to set the permissions on the host or separately on every Resource Pool. Another option is to create a folder, put the ESXi host in the folder then assign permissions on the folder with the propagate option. Right now I will set the permissions on the ESXi host. On the Permissions tab add the Exchange Admins group with the Exchange/RDS role.
Now log in to vCenter with one of the Exchange admins accounts.
This users can see/manage another part of the vCenter infrastructure, and can’t see the developers workstations at all. You can mix and match permissions in vCenter so you can assign the proper rights to the proper people.
Want content like this delivered right to your
email inbox?