Digitally Signing RemoteApp Programs on Windows Server 2008 R2
Those of you that have one or more Remote Desktop Session Host (RD Session Host) servers in the network, that host RemoteApp programs, know how frustrating is that certificate error when clients connect to their virtualized applications. To re mediate this you will need to install a proper/trusted certificate on the server to sign those applications; actually you are signing the .rdp files, not the applications, just to make a quote here. You can use a commercial certificate, if you have the budget and a lot of external clients, or you can use your internal Certification Authority. If you use the second solution, clients that are not part of the domain will need to have the root certificate installed for this to work properly. So enough with the talking and let’s get started.
To demonstrate this I will use a Domain Controller running on Windows Server 2008 R2, and a Remote Desktop Session Host server also running on Windows Server 2008 R2, joined to the domain. On the Domain Controller I installed the Enterprise Root Certification Authority, so looks like we are going to use our internal CA; since the budget is tight.
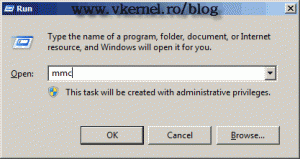
To start, on the RD Session Host server and open a certificate mmc (Start > Run > mmc.exe), because we need to request a proper certificate from our internal CA to sign those applications.
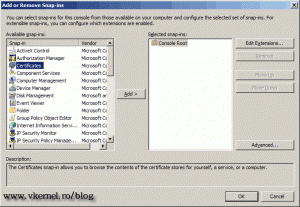
Here go to File > Add/Remove Snap-in, and from the Available snap-ins list select Certificates and click Add.
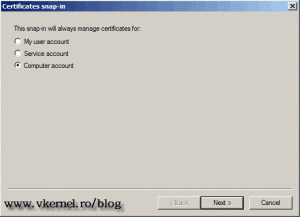
On the window that just opened select Computer Account then click Next.
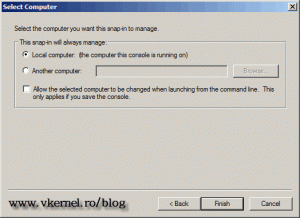
Select Local Computer and click Finish, and OK.
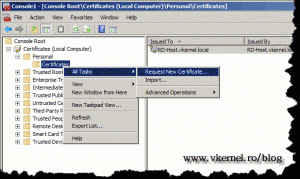
Expand Certificates > Personal and click on the Certificates folder. As you can see we already have a certificate that we can use to sign applications, but this is a self signed certificate, and is kinda useless.
Right click the Certificates folder and choose All Tasks > Request New Certificate.
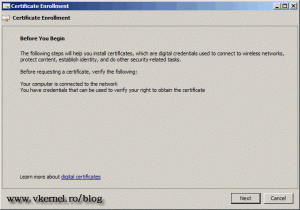
Click Next on the Before you begin screen.
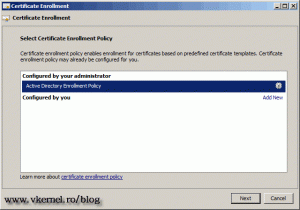
Leave Active Directory Policy Enrollment option selected and continue.
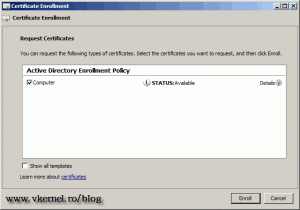
Check the Computer box and click Enroll.
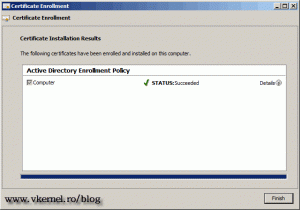
If the certificate was installed without errors, a success message will appear next to a green check box. Click Finish to close the wizard.
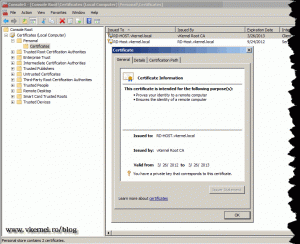
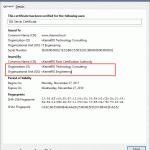
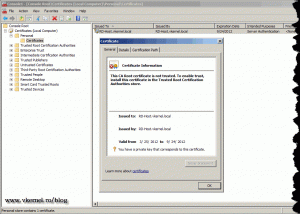
As you can see we have another certificate installed, but time it was issued by a Certification Authority. You can now close the certificates console.
Now, on the RemoteApp Manager click the Change link next to Digital Signature Settings.
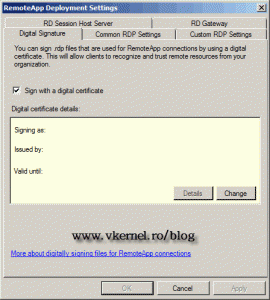
On the window that just opened check the box Sign with a digital signature, then click the Change button.
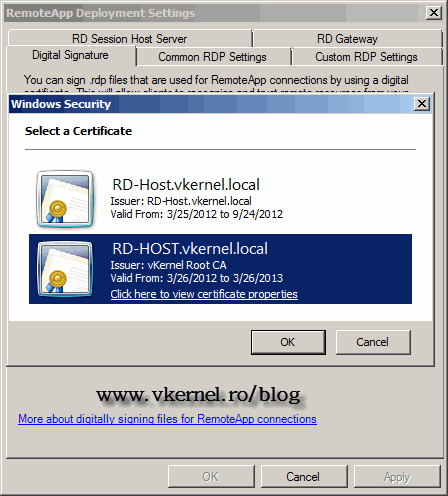
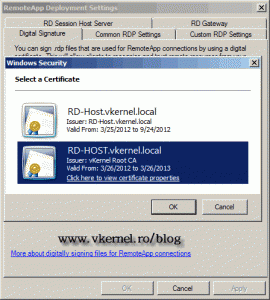
Select the certificate issued by our internal CA then hit OK. To find out which one is it you can click the link Click here to view certificate properties.
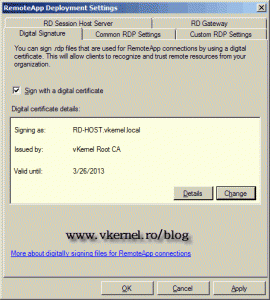
Click OK to save and close the RemoteApp Deployment Settings window.
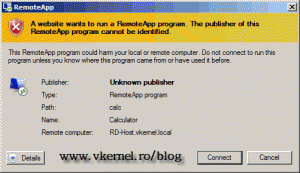
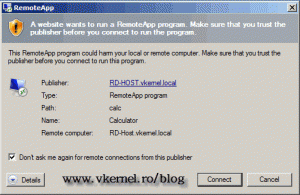
Now if you try to open a virtual application from a client, you still get a warning message but now you have the option to suppress that by checking the box Don’t ask me again for remote connections from this publisher. And as you can see the application is signed by RD Session Host server certificate we just installed.
Looks like everything worked out just fine, and all you need to do is train your users to open only signed applications. Good luck with that.
Want content like this delivered right to your
email inbox?