Publish VMware vSphere client with TMG 2010
There are situations in small environments when you need to access your ESX/ESXi server from the internet, for troubleshooting or just to create or restart a virtual machine. I bet that’s a piece of cake for some of you, but what if you have a TMG server as a firewall. Well…things are not so easy any more, but they are not complicated either. If you have a situation like this, where a TMG 2010 server acts as a firewall for you or for some of your clients, and want to access an ESX/ESXi server from the internet, then you came to the right place.
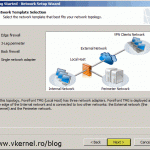
In this lab the TMG server is not joined to the domain, but even if it was things still be the same. To be able to connect and use the VMware vSphere console from the outside we need to open/forward three ports on our TMG server, 443 (for security certificate), 902 (for authentication), 903 (for the VM console). For a full list of VMware ports go here. Now, open your TMG console and click the Firewall Policy object. On the Actions pane click the link Publish Non-Web Server Protocols.
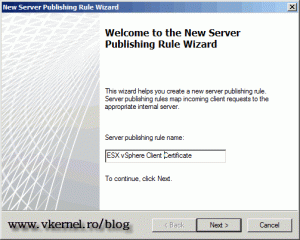
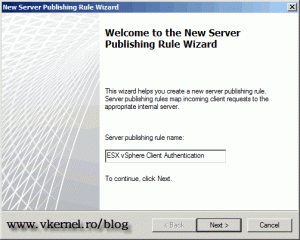
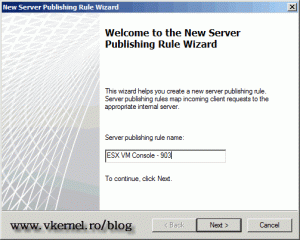
On the first screen of the wizard we need to type a name for the rule.
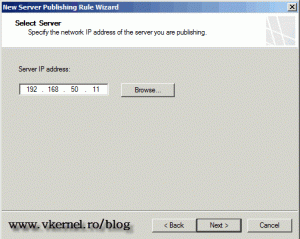
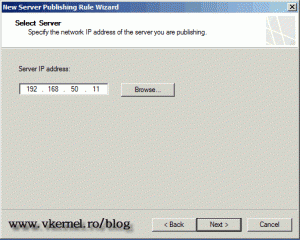
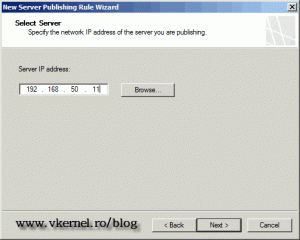
Here, type the IP address of your ESX server, then click Next. This is for the TMG server to know where to forward the incoming traffic.
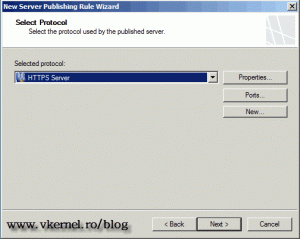
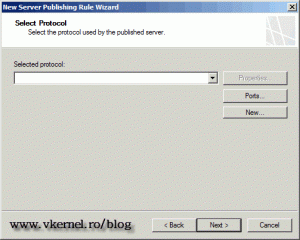
Since 443 is a standard protocol for security, is predefined in the protocol lists of the TMG server. For the drop-down list select HTTPS Server and click Next.
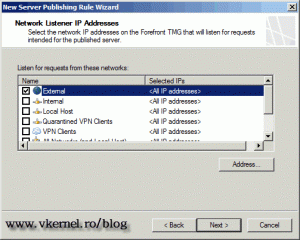
Since we are connecting for the internet, select External, so the TMG server will listen on that interface for the 443 traffic.
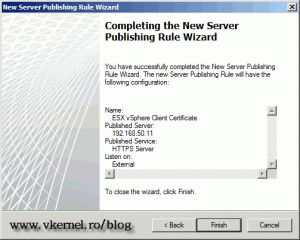
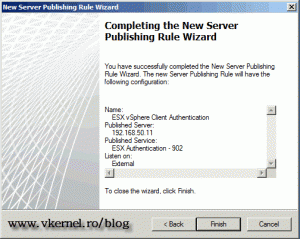
On the Summary page just click Finish to create the rule.
We are not done yet, I sad we need to open three ports, so again, click the link Publish Non-Web Server Protocols in the Actions pane. This time we are opening port 902 for authentication. Give the rule a name and click Next.
Type the ESX server IP address and continue.
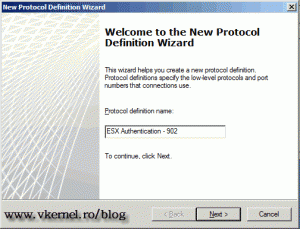
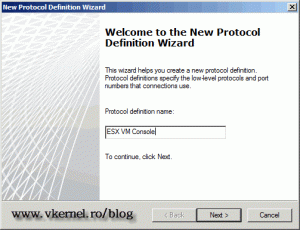
Since this protocol is not predefined in the TMG server we need to create it, so click the New button to start the New Protocol Definition Wizard. Give the protocol a name and continue.
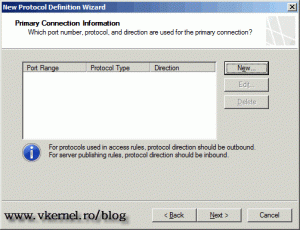
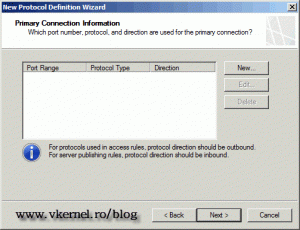
On the Primary Connection Information page click the New button to start creating the ports, direction and protocols.
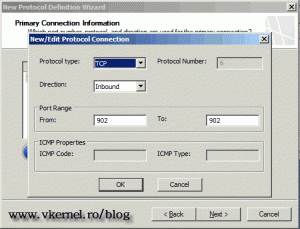
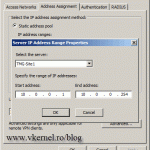
Here on the Protocol Type select TCP, and since the connection is coming from outside to inside on the Direction option select Inbound. On the Port Range boxes type 902 and click OKto close the window.
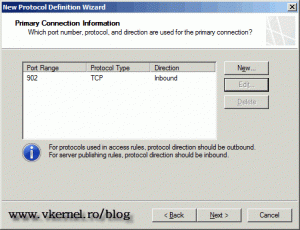
Back to the Primary Connection Information page click Next to continue.
Here just go with the defaults, because we don’t need secondary connections.
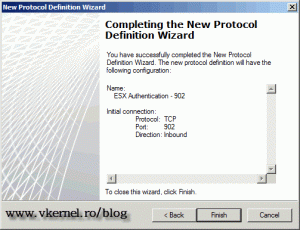
On the Summary screen click Finish to create the protocol.
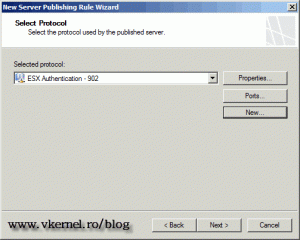
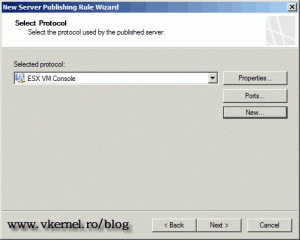
The new protocol is automatically select for us in the New Server Publishing Rule Wizard. Click Next to continue.
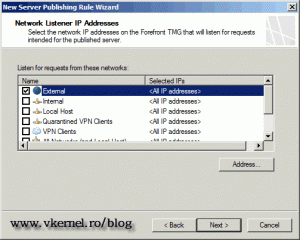
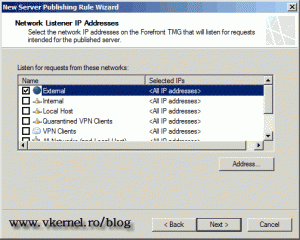
Here select the External network,
and on the Summary screen click Finish to create the rule.
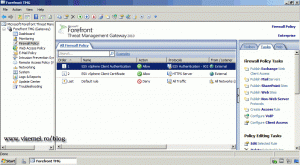
Don’t forget to click the Apply button on the TMG server, to save the configuration changes.
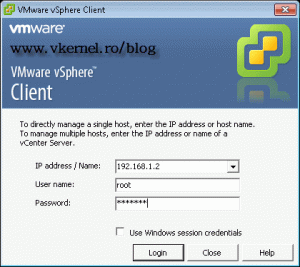
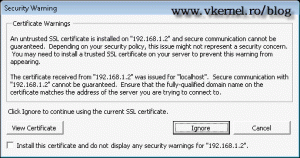
Now we can connect to our ESX server from internet using a FQDN or the external IP address. If your certificate is not trusted you will get a warning, just ignore it.
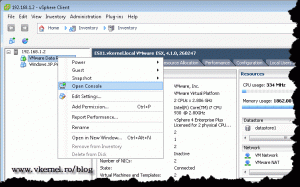
You might be thinking, what about the third port ? Yes, we’ll get to that in the following section, because if we don’t, we can’t open a console to our virtual machines. On the vSphere client console right-click a virtual machine and choose Open Console.
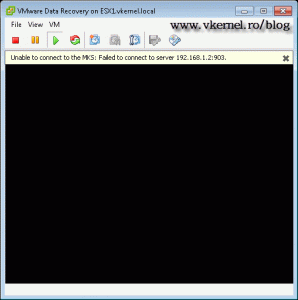
As you can see the connection fails, because port 903 is closed.
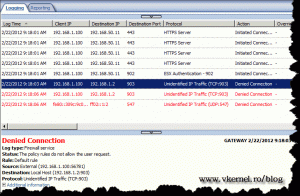
If we take a look in the TMG logs the connection is denied for the specified port.
Now let’s open this port so we can use the virtual machine console. Again, in TMG click the link Publish Non-Web Server Protocols on the Actions pane. Give the rule a name and continue.
Type the IP address of the ESX server.
Since this protocol definition is not specified, we need to create it. Click the New button.
Give the new protocol definition a name then click Next.
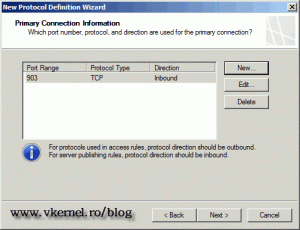
On the Connection Information page click the New button.
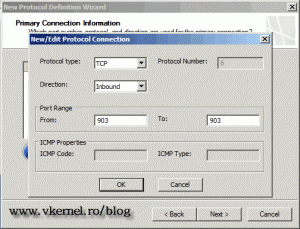
Select TCP on the Protocol type, and Inbound on the Direction list. Type 903 on the port rage boxes.
Now finish the New Protocol Definition Wizard using the default settings.
Back on the New Server Publishing Rule page click Next to continue.
Here select the External listener.
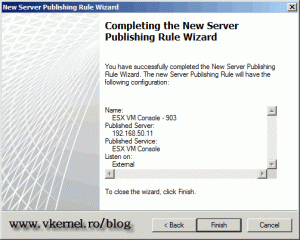
Click Finish on the Summary screen to create the rule.
Again, don’t forget to click the TMG Apply button to save the changes.
Now let’s open a virtual machine console to see if it works. And we have a success, no more KMS error.
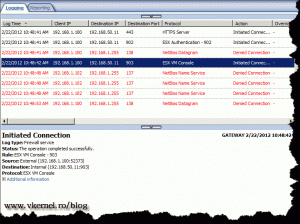
If we look in the TMG logs we can see the connection is allowed.
Want content like this delivered right to your
email inbox?
Can someone tell me how to change standard Remote Console port “902” in ESXi 5.x? I really need your help: https://communities.vmware.com/message/2449452
Hi,
Well… you can’t, and it’s not me who is saying this, is VMware “… VMware does not support configuring a different port for this connection.“. Your best approach, and a recommended one will be a VPN connection. This way you don’t have to open to many ports in firewall and everything works.
I also publish OWA with my TMG over https. So there is a listener on the external interface. Do I have something special to configure when I try the ESXi Client Cert rule, which is also https.
For that you will need two public IP’s and two certificates. This is not a TMG restriction, is an SSL one, since an SSL certificate can be binned to only one IP.
Adrian,
It worked fine when I first started 🙂
Not sure if it’s because the servers had beenr ebooted since I last implemented the rule or simply leaving it a while before trying again helped – either way your steps worked.
Thanks
Dan
I’m glad it worked. After you click Apply in the TMG console, rules are not in effect right away. The services needs a few seconds or even minutes to write the changes/rules to the TMG configuration store.
Cheers Adrian,
I’ll double check the settings when I’m back in the office next week. Should this also work for the TMG server itself? (I’m adding localhost, as well as external to allow a Vspehere client to a single ESXi host).
Thx
You don’t need to add any localhost for this scenario.
I’ve gone through this, but I’m still getting a problem connecting – failed to connect to server 902/903.
I’ve created a non web server protocol publishing rule, followed your instructions but no luck. I’ve also tried with standard client access rules using the inbound protocol definitions you’ve mentioned, but I always run into problems with console access.
TMG displays unidentified IP Traffic (TCP:902) – even though I’ve created the protocol and applied changes.
My TMG server has 2 NICs, with route behaviour setup between them (I’ve also tried NAT), but it fails every time – it’s almost as if TMG doesn’t recognise my protocol definitions
Please advise
Thanks
For sure you are doing something wrong here, because I did this for some of my clients and it works. I like to mention again that this is for a single ESXi host, not for vCenter.
Verify you are putting the right IP of the ESXi server in the TMG wizards, make sure your TMG server is functioning correctly (see my article of installing TMG on 2008 R2). When you connect form the outside you need to type the IP that is on the external interface of your TMG server (not the ESXi server IP). Do those verifications and let me know.
Thanks for passing by.
Hi,
Is your tutorial applicable to a single host or a virtual center server?
I am able to access the virtual center via vSphere client no problem but when I try to Open the console, I’m getting a MKS related error on port 902:
Unable to connect to MKS: Failed to connect to server FQDN_OF_THE_ESXi_HOST:902
I changed the publishing role to point to THAT host for testing purpose and it worked.
Question is: how do I access the VM Console for VM’s on other hosts?
The funny thing is that the rule for port 903 still point to the vcenter server….
Thanks for your help
This is for a single host. I have on standby a post to publish vCenter with TMG 2010, but I don’t know when I’ll finish it.