Publish VMware vShpere 5 Web Client Server with TMG 2010
OK, you are using the VMware vSphere 5 Web Client Server for quite some time now in your network, but what about access from the internet. Wouldn’t be nice in case of an incident to just open a browser, type the address (public address) of your VMware vShpere Web Client Server and manage the infrastructure from here ? You can, and you should, since in the future version of vCenter the management will be only web-based; so I hear.
For this guide I have a TMG 2010 server, a VMware vShpere Web Client Server and a Domain Controller. Off course, all servers are joined to the domain. The certificate used here is a SAN certificate and is issued by an Internal Enterprise Root CA, and all my external clients have the root CA certificate installed in the certificates store. In a real production environment I recommend you purchase a commercial CA. Before we start I presume you already created an A or CNAME record on your public DNS server which points to the external IP address of your TMG server.
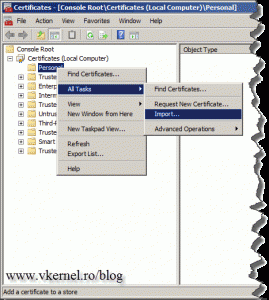
First we need to take care of the VMware vSphere Web Client Server certificate, by replacing the default one with the one issued by our internal CA. Since I already have a guide for this at this link, I’m not going to review it here. Read the post, replace the default certificate, then come back here and continue reading. After the certificate is in place on the vSphere Web Client Server, we need to copy the rui.pfx certificate on the TMG server. Here (on the TMG server) open the Certificates Store (Start > Run > certmgr.msc) and import the certificate in the Personal Local Computer folder. Right click the Personal folder and choose All Tasks > Import. Follow the wizard.
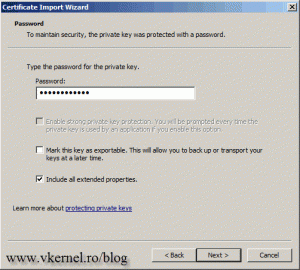
When you get to the password screen type the certificate password which is testpassword. This password is valid only if you followed along my post for replacing the VMware vSphere 5 Web Client Server certificate.
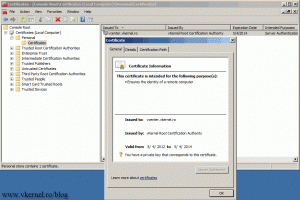
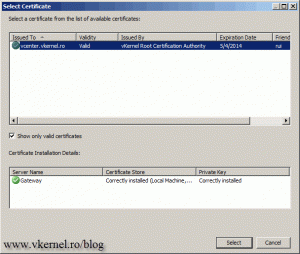
After you finish the wizard, you can see the certificate in the Certificates Store with its private key.
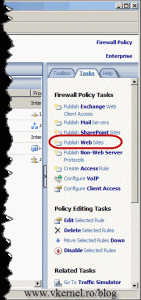
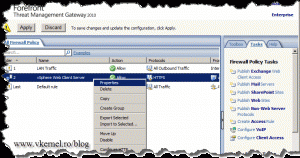
Now let’s publish the site with TMG 2010. Click the Firewall object, then in the Tasks pane click the link Publish Web Sites.
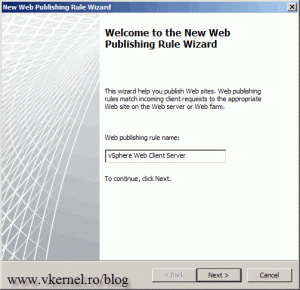
Give the rule a name, then click Next to continue.
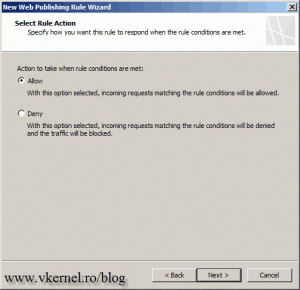
We need to allow the traffic since we want to publish this rule to the internet, so just leave the defaults here and continue.
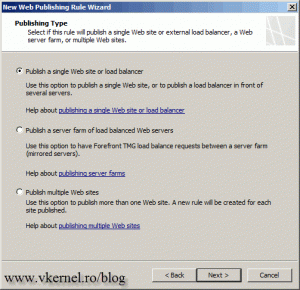
Since we publish only one web site the first option is perfect.
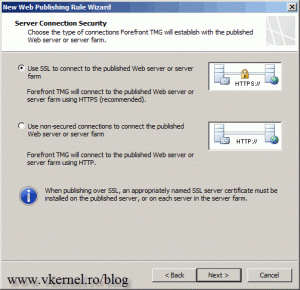
The vShpere Web Client Server site is using SSL, so we are going to use the first option here too.
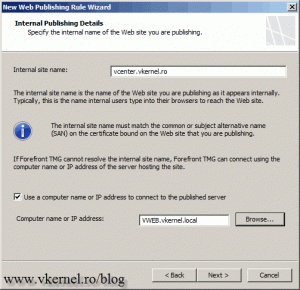
Because I like my internal site names to be the same as the external ones (it doesn’t confuse the users), I will type here the external name I will use to connect to the vSphere site. Check the box Use a computer name or IP address to connect to the published server, then bellow type the name of the server.
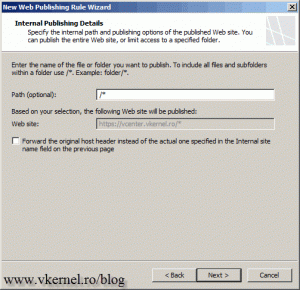
Here put /* to publish the whole website.
On the Public name box type the public name users/admins are using in their browsers to connect to the site. The public name needs to exist in the certificate (imported on the TMG server) SAN attribute or the Common Name.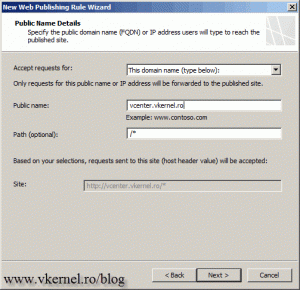
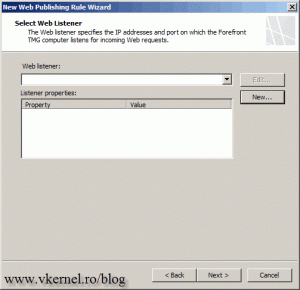
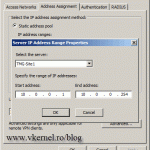
Now we need to create a new listener, so TMG will process the HTTPS traffic matching the FQDN we put in the certificate. Click the New button to start creating the listener.
Give the listener a name and continue the wizard.
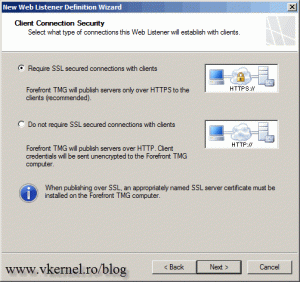
Here go with the default setting, because we are publishing a secure website.
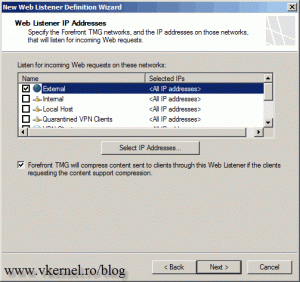
Select External, so TMG 2010 will listen on traffic coming on the external interface.
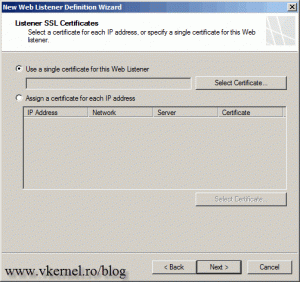
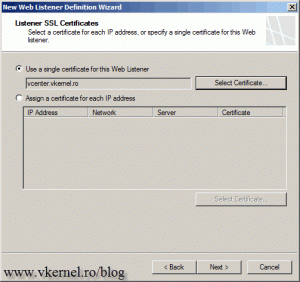
Now is time to get use of that certificate. Click the Select Certificate button, then in the list select the certificate and hit Select.
We now have a listener SSL certificate. Click Next to continue.
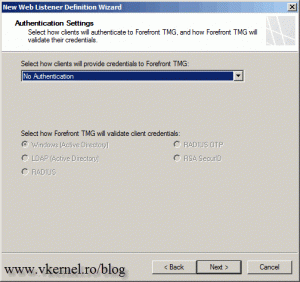
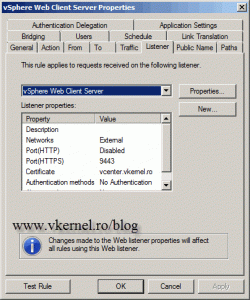
Here select No Authentication, because we don’t want TMG to authenticate the external clients, we want vShere Web Client Server to authenticate them.
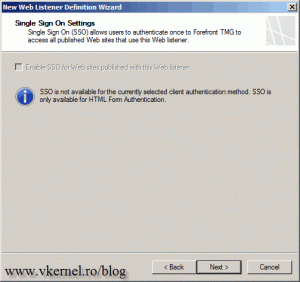
SSO is disabled, so click Next to go forward.
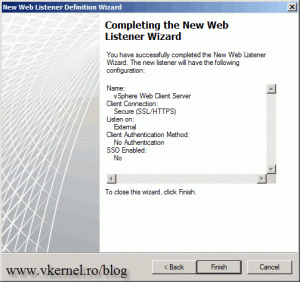
On the Summary screen click Finish to create the listener.
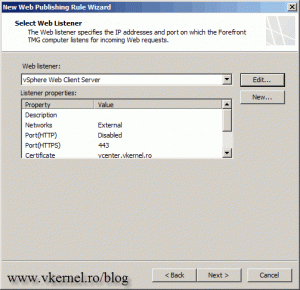
Back on the Publishing Rule Wizard, select the new listener and click Next to continue.
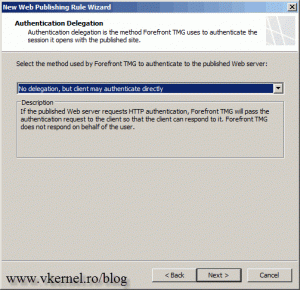
Select No delegation, but client may authenticate directly.
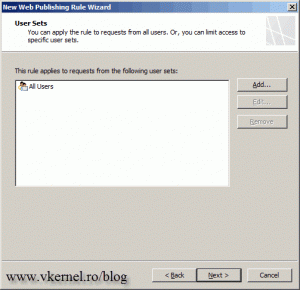
On the User Sets page leave All Users, meaning we want everyone to be able to connect to the web site.
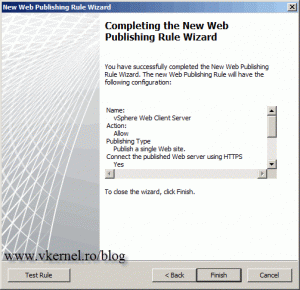
On the Summary screen click Finish to create the rule.
Don’t hit the Apply button yet on the TMG server, because we need to do some modifications on this rule. Right-click the rule and choose Properties.
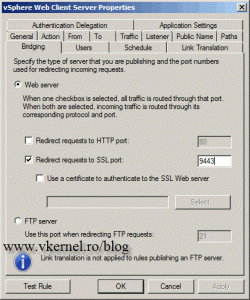
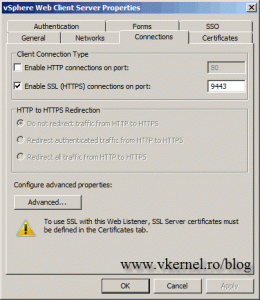
Go to the Bridging tab and in the Redirect requests to the SSL port box, type 9443.
The same change needs to be done on the Listener tab. Click Properties, go to connections and type 9443 on the Enable SSL (HTTPS) connections on port box.
Click OK and close all the windows, and now you can Apply the changes on the TMG server, by clicking the Apply button.
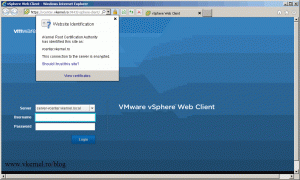
Go to one of your external clients and connect to the web site by typing https://server FQDN:9443/vsphere-client. As you can see I have an internal domain (vkernel.local) but I’m using the external domain name to connect, and is working just fine.
Want content like this delivered right to your
email inbox?

Hi, Thank you for this article, i used it to publish my web client and it works great 🙂
But, there is one thing that not work : remote console.
Do you know a way to make it functional ?
Regards
Hi,
For that you will need to open port 903. Here are the list of ports that VMware uses.
Adrian
Hi,
Thank you for this post. I managed to publish the web client, however I get the below error when the blue screen is loading externally – internally it loads but externally I get Error #2032 at the bottom. Any ideas?
Here you go Accessing the Heartbeat tab in vSphere Client or vSphere Web Client for the first time causes a #2032 error. Let me know how it works.
Thanks for the tip!
Hi,
I tried the above with vSphere 5.1 web client. The problem is we have a back to back TMG Firewall. I published the vsphere site on the back firewall (TMG 2010) as above, and forwarded port 9443 to the back firewall from the front firewall (TMG 2010) but can not access. We do the same thing for port 443 for OWA and that works fine.
I’m not sure what I am doing wrong, any pointers please?
Regards
H
It’s the Web client certificate valid ? Try by importing the certificate on the front firewall too. I never tried this configuration before, but looks like I will have too in the future. Let me know how it works.
Surely you want TMG pre-authenticating at the edge, and delegating credentials to the published website, rather than allowing non-authenticated traffic through to your vcenter server?
Will vcenter web access accept delegated credentials? It seems to run on Tomcat.
(yes yes – and don’t call me Shirley….) 😉
Never tested this way, but I think you will get two authentications screens. One from TMG and the other one from vSphere Web Client. I will look into it when I have some free time.