Installing an Enterprise Certificate Authority in Windows Server 2012
A lot of things changed in server 2012 on the PKI model compared to his predecessors. We have version four certificates now, better security on the CA role service, you can install the AD CS role services on server core and many more features. The installation is straight-forward and you are guided by a wizard, and for those that are more adventurous there is PowerShell. You can install the AD CS role on a domain controller if you are running a small network, but a separate server is always recommended. For this guide I’m going to use a dedicated server since I can afford it, thanks to virtualization.
To begin, power up the Server Manager and go to Manage > Add Roles and Features.
Click Next to skip the Welcome screen. You can also check the box Skip this page by default so the screen will never show up, is annoying anyway.
Leave the default selection “Role-based or feature-based installation” and continue.
As you might know in server 2012 you can install roles and features remotely, so you don’t have to log in to that specific server for the operation. Select the server from the list on witch you want to install the AD CS role and click Next.
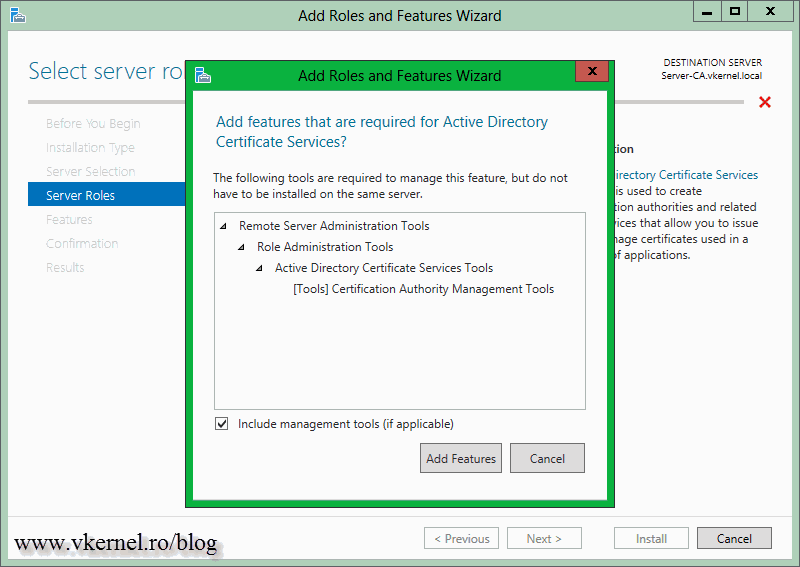
On the Select server roles page check the box next to Active Directory Certificate Services. On the window that pops-up click the Add Features button.
Don’t check anything here, just continue the wizard.
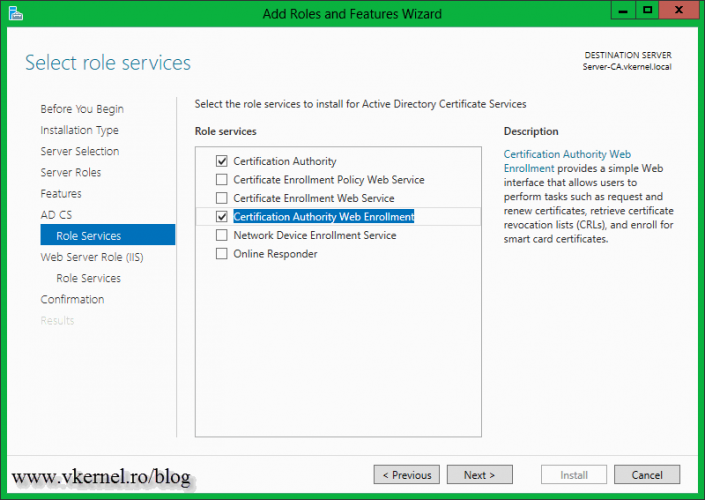
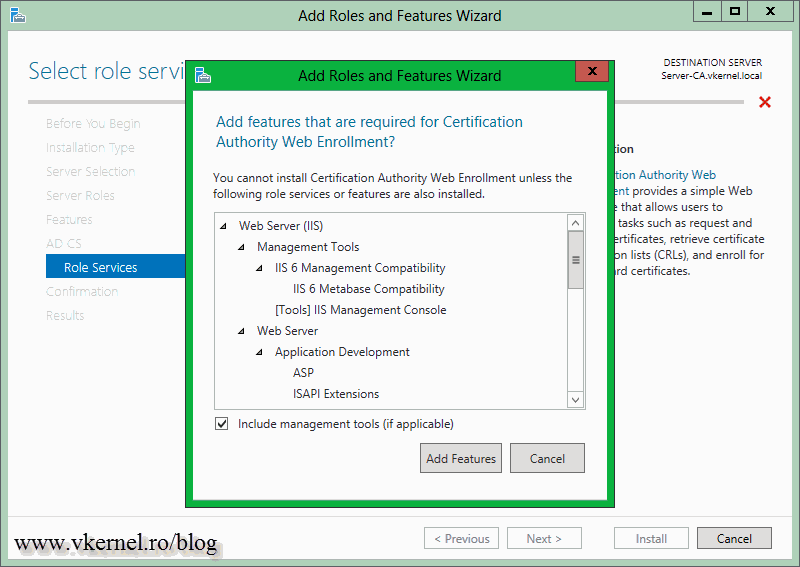
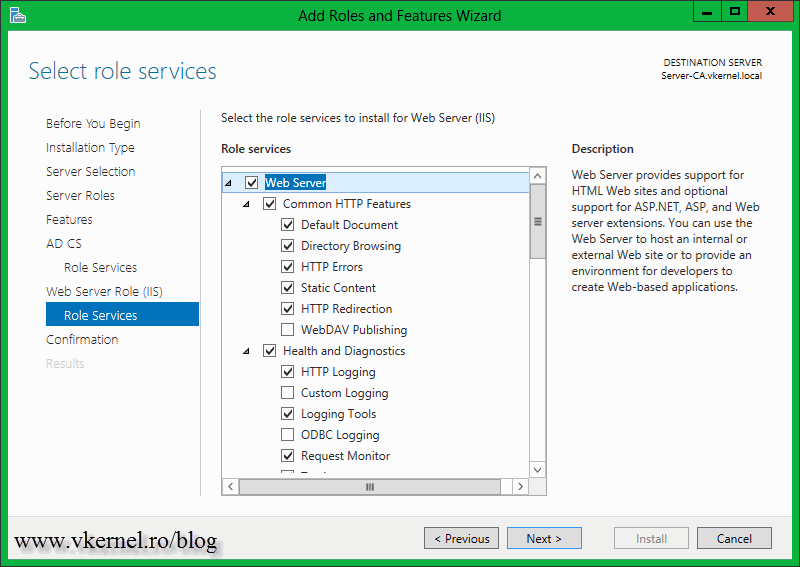
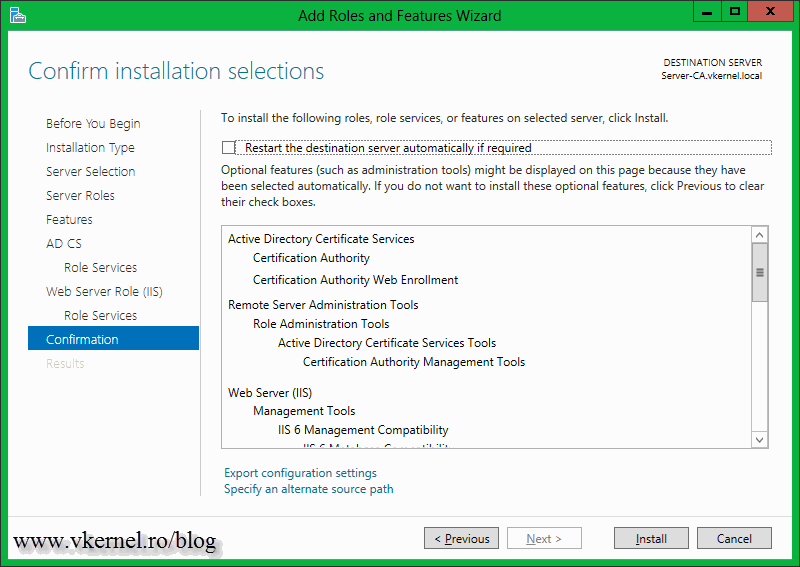
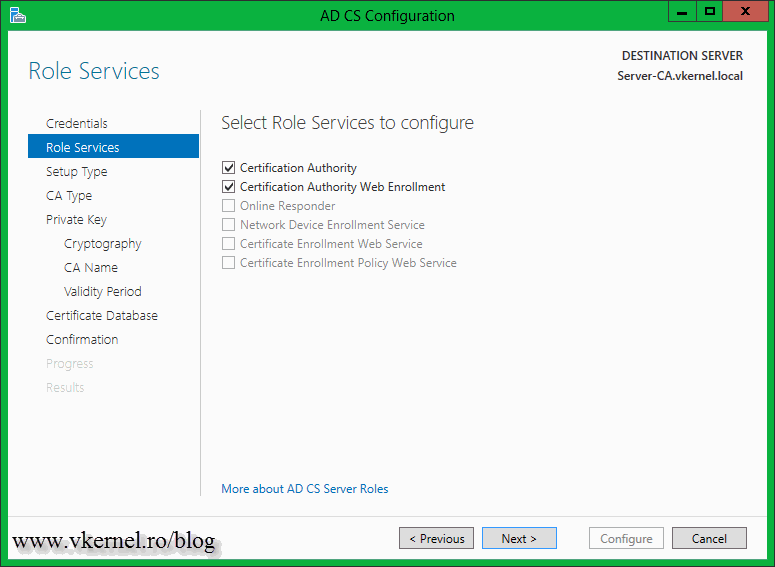
Here we have the option to install some additional AD CS role services. If you click the items in the list, on the right side you will have a short description of what that role service is doing. For more information about it just click the link in the description. Select the role service you want to install and click Next. For this example I will also install the Certificate Authority Web Enrollment, so users can request certificates via a web browser.
Continue the wizard using the default options.
On the Confirm installation selections page click Install.
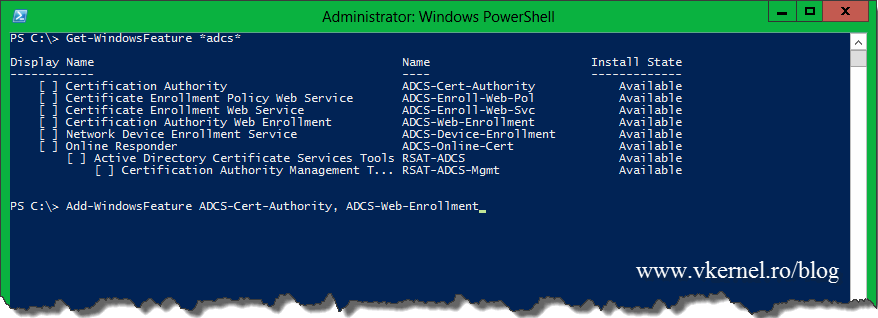
If you want to do this using PowerShell use this command:
This will install the binaries for the Certification Authority and the Web Enrollment role service.
Add-WindowsFeature ADCS-Cert-Authority, ADCS-Web-Enrollment
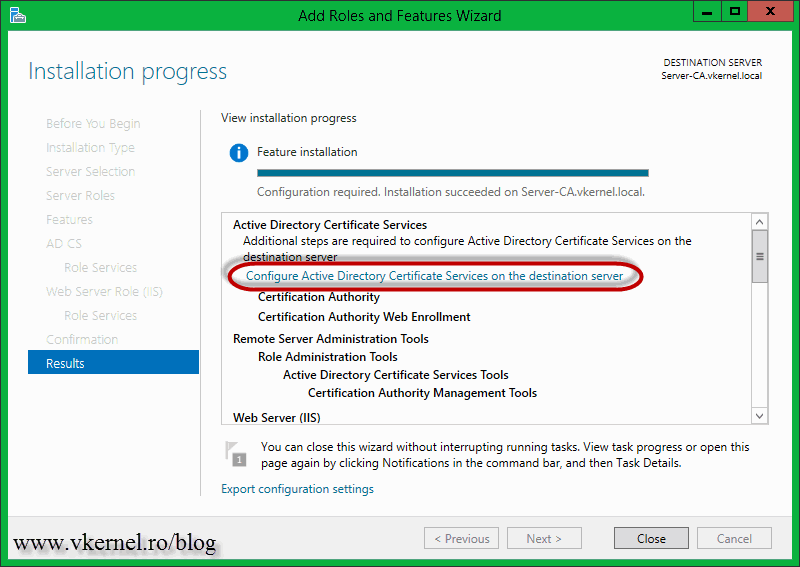
The installation will take a few minutes, and when is done click the Configure Active Directory Certificate Services on the destination server link.
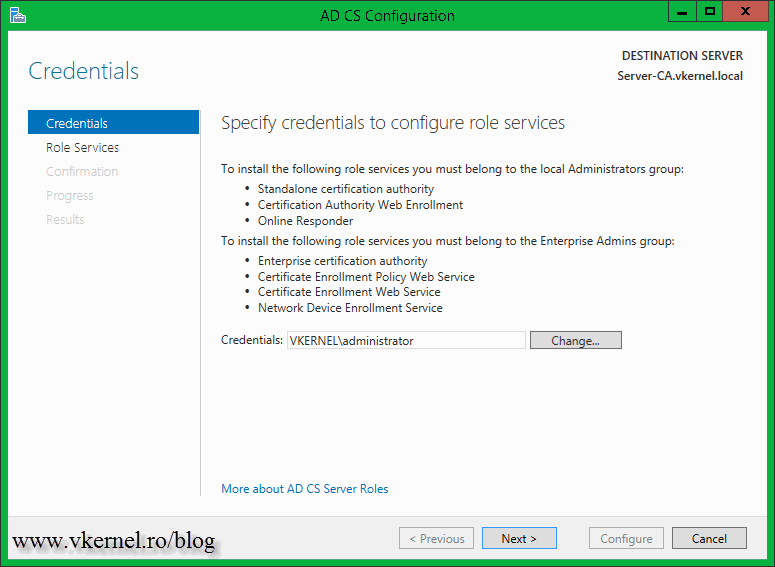
In order for the Certificate Services to be configured it needs an administrator account. The account must have enterprise permissions in order for the configuration to succeed. I am using the enterprise administrator account so I’m good-to-go.
Select which role services you want to configure then click Next.
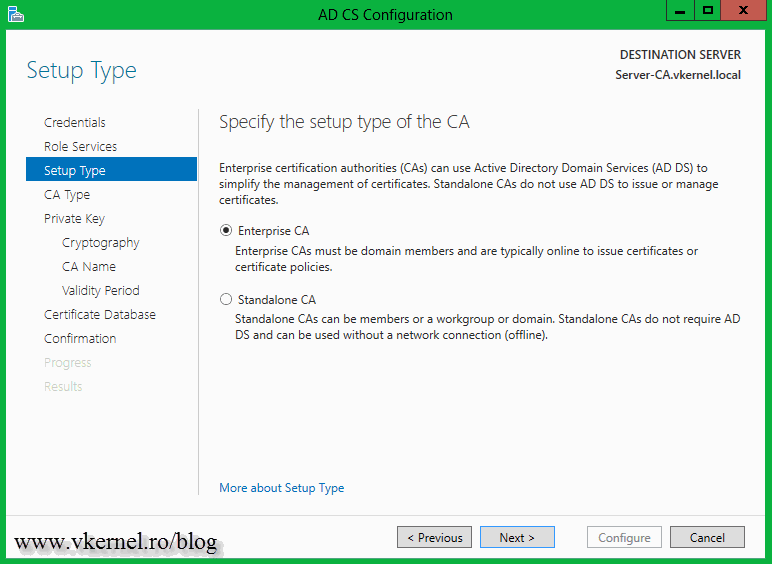
Go with the Enterprise CA option so the Certification Authority can be AD integrated.
Being the first CA in the infrastructure select Root CA and continue the wizard.
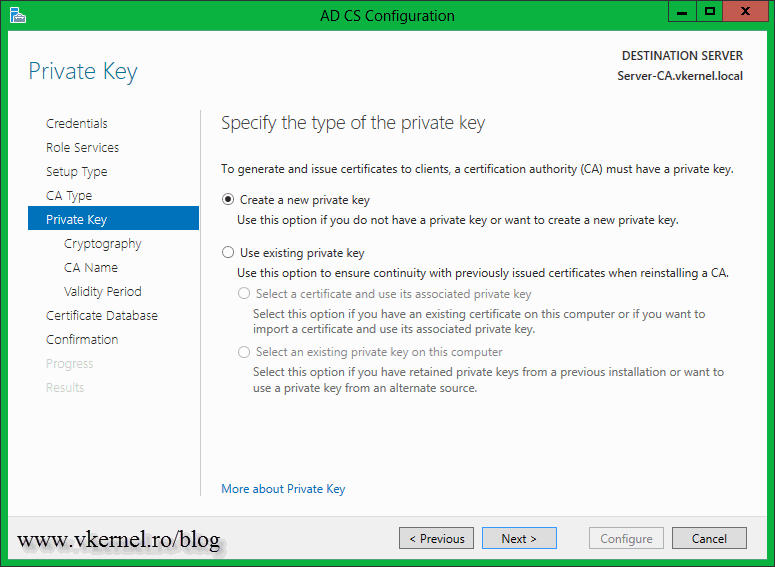
Go with the default selection here and create a new private key.
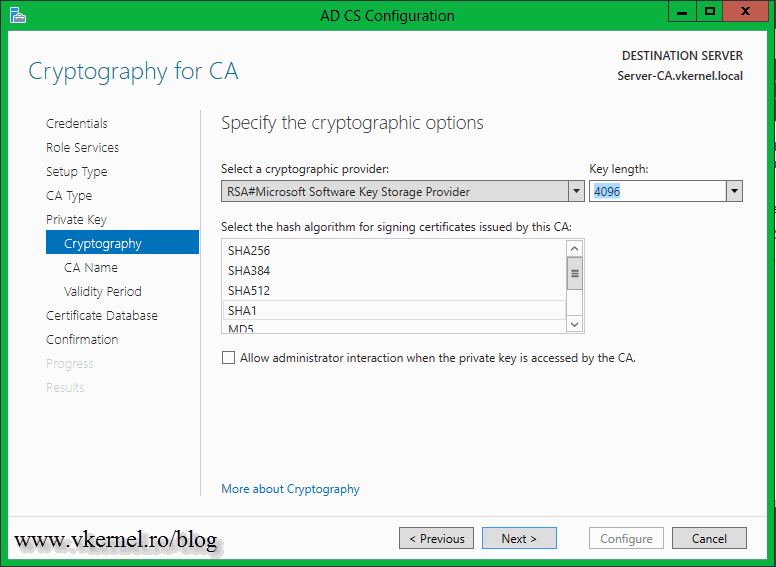
Leave the default hash algorithm, then select your key length. I usually go with 4096 for an Enterprise CA, but be careful with this because there are some third-party software that might have problems with such a big key. Since I know my internal software is OK with this key length, I’ll go with this one.
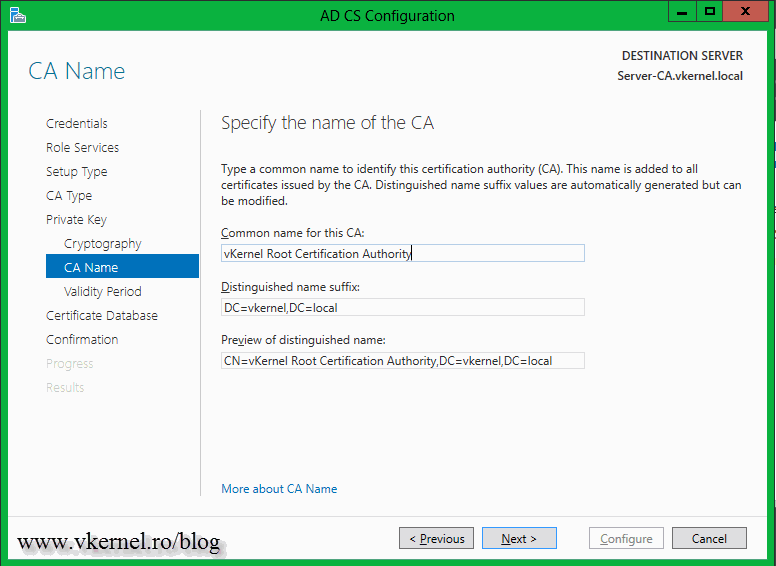
Type a name for your internal CA in the Common name for this CA box then provide a distinguished name suffix. Click Next when done.
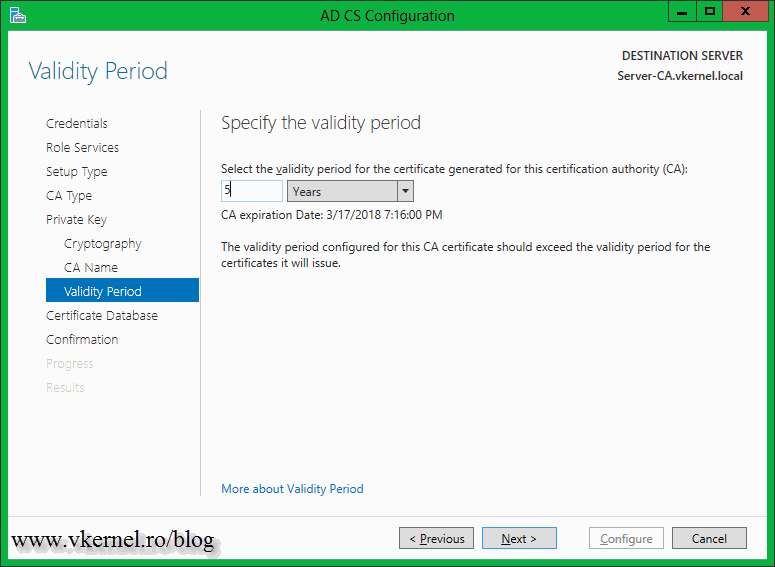
For a Root CA I usually go with 30 years as a validity period, but only when I have a three tire hierarchy (Root, Subordinate, Issuer). In this case I’ll leave the default validity period and continue the wizard.
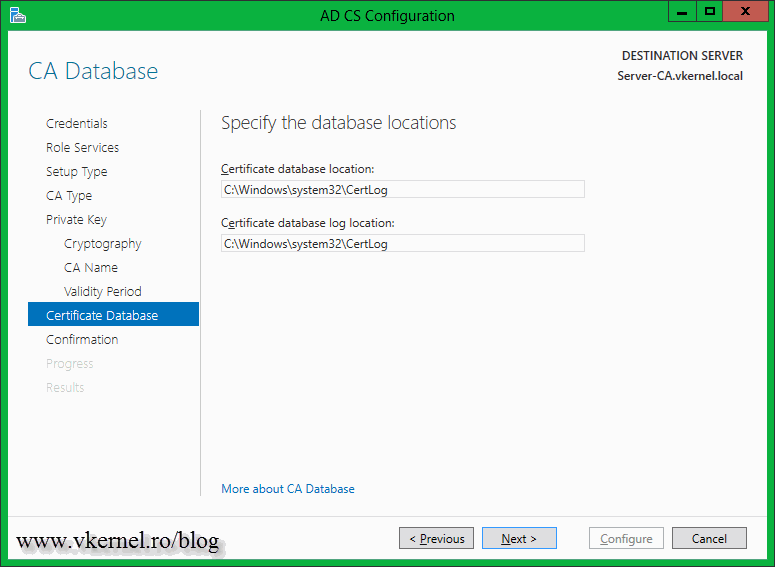
Type a location for the database and log files, if you want to change the default ones.
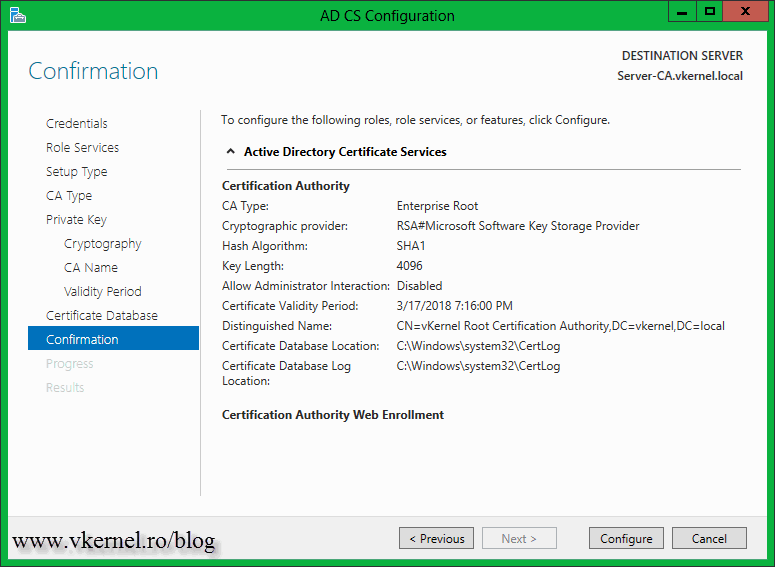
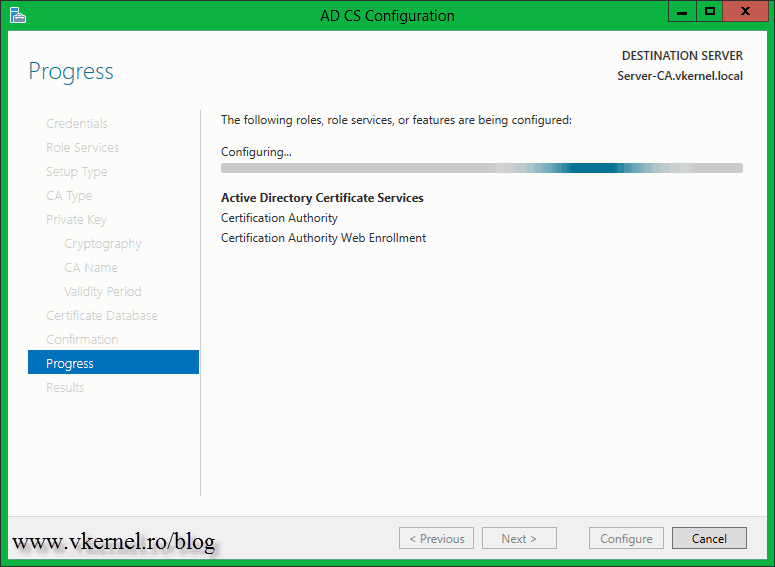
On the Confirmation page click Configure.
This will take just a few seconds to complete, and when is done you should have some green validation checks.
If you want to open the Certification Authority console, go to Server Manager > Tools > Certification Authority.
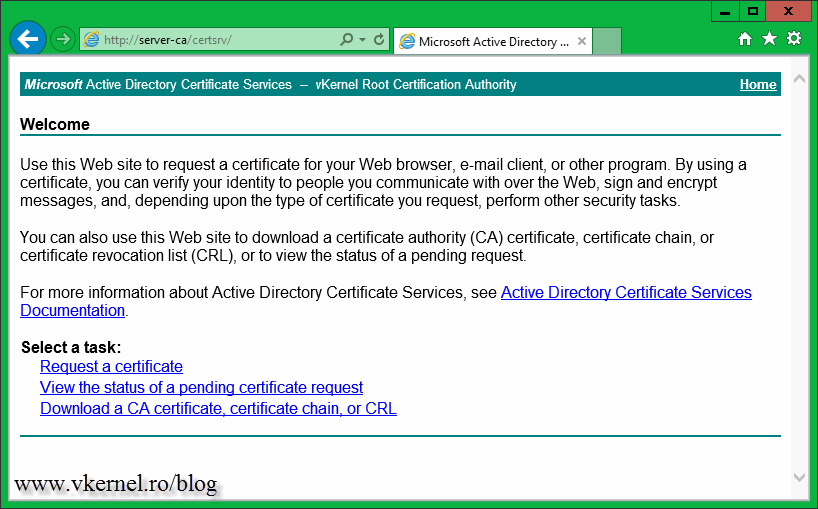
Open a browser and see if the certificate enrollment web page is working. From a client, type your CA server name followed by /certsrv (http://server-ca/certsrv). If you opened IE on the CA server itself you can use localhost followed by /certsrv.
Want content like this delivered right to your
email inbox?



Fine article. Can you explain the steps to adequately secure a VMware Issuing CA server on a VMware Host. The obvious concern I have is over the .vmdk file and its accessibility. Do you have a list of steps to cover in prepping an Issuing CA VM on VMware so it is secure?
Thanks in advance!
Bill
Well… first make sure the vCenter permissions are in place so only the required people can see or access the VM. Second, make sure who you allow to RDP into the guest. Third, I will put the VM in a separate VLAN where only the required people can access it; normal users can’t even PING the VM/VLAN.
Good luck 🙂
thnx alot
You’re welcome.