Install Certification Authority in Windows Server 2008 R2
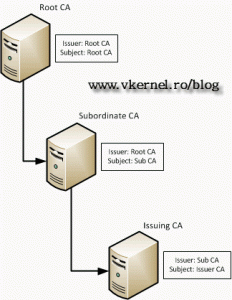
Yes, you can have your own Certification Authority (CA), and issue certificates for clients. The bad news is that certificates issued by your internal CA are trusted only by you internal clients, or by clients that have your root certificate imported. For internal applications, sites etc this is gold, because you don’t have to by a commercial certificate, but if you have a public HTTPS site you will need a commercial certificate. Certification authorities can have multiple ramifications or levels, like Root CA, then a Subordinate CA, and the last one is the Issuing CA.Bellow I created a diagram for a better visualization.
Root CA will issue certificates only for Subordinate CA, and the Subordinate CA will issue certificates only for Issuing CA. The Issuing CA is the one that will issue certificates for internal clients. You can, off course create more than three ramifications, but even those commercials Certification Authorities are not going with more than three. Now there are multiple types of Certification Authorities for Windows Domains. The first and the bigger one is Enterprise Root CA, then is Enterprise Subordinate CA. These two types are used only if you have a Windows Domain implemented in your network. The last two are Enterprise Standalone CA, and Subordinate Standalone CA. These are used if you don’t have a Windows Domain implemented. Now the difference between Enterprise and Standalone is that with Enterprise you have certificate templates, and the root certificate will automatically be deployed to all clients. I will end this introduction now, and start working.
For this guide I have a Domain Controller (DC) running Windows Server 2008 R2, and another Windows Server 2008 R2 (named Server-Cert) joined to the domain, which will be our Enterprise Root CA. Yes I’m going with the Enterprise version, because is a Windows Domain, and for small business is more than sufficient a single Enterprise Root CA.
Go to Server-Cert and open Server Manager; right-click Roles and choose Add Roles.
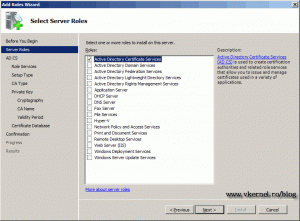
Click Next to skip the Welcome screen. On the Roles screen select the Active Directory Certificate Services and click Next.
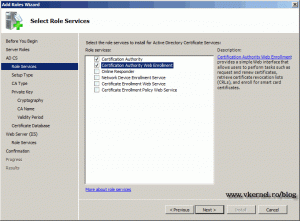
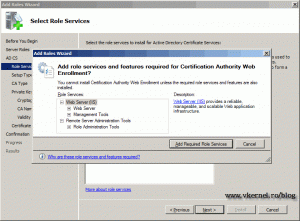
Skip the introduction of AD CS. On the Role Services screen we have the option to install more than just the certificate service. For this demonstration I’m going to install the Certification Authority Web Enrollment too. This will give us a web page to request certificates, and it’s great, believe me. As soon as you click the Certification Authority Web Enrollment you will be asked to install some required prerequisites. And off course a web site to function needs a web server. Just click Add Required Roles Services and continue the wizard.
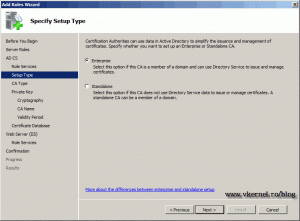
Because this is about installing Enterprise Root CA, just leave the defaults here and click Next.
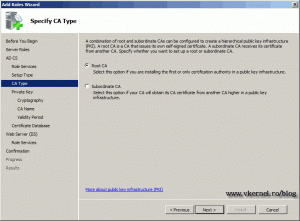
Again leave the defaults here to install a Root CA.
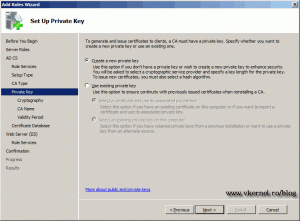
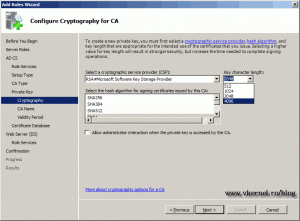
We need to create a new private key, so click Next to continue.
For Enterprise Root CA I usually choose a length key of 4096 and leave the rest to default.
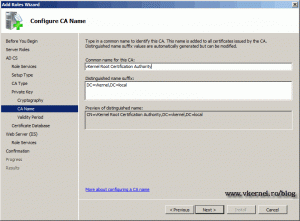
Give your Root CA a name. I always change the name, because I really hate the default one.
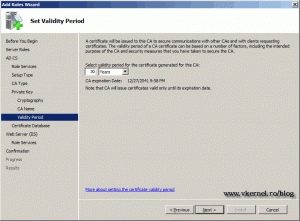
Select a validity period. For Enterprise Root CA I usually type 30 years.
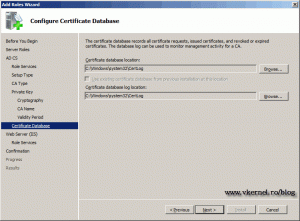
If you have a reason to change the default log and database location, do it using the Browse buttons. Now comes the IIS installation part, just go with the defaults and finish the wizard.
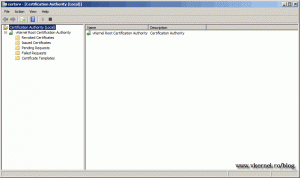
The installation is done. Go to Administrative Tools > Certification Authority to open the Management Console for the Certificate Services. From this console you can revoke certificates and create templates.
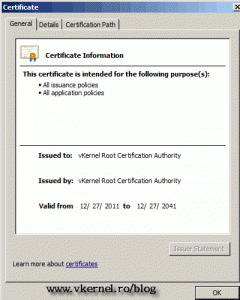
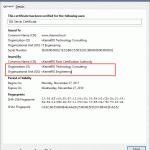
To see the root certificate just right-click the server name, choose Properties and hit the button View Certificate
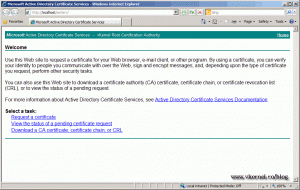
Open a browser and type http://localhost/certsrv, and the Certificates Services Web Enrolment page should open. Using this web page clients can request certificates, if they have the proper permissions.
Want content like this delivered right to your
email inbox?


I have follow the step and done all the setting but when i go to Certificates Services Web Enrolment and try to create a subordinate Certification Authority” template , i dont see any options thr ,its only show Basic EFS and Users, please advice.
Hi,
It’s because you are logged in with a simple domain user. You need to be logged in with a domain admin account, then your Subordinate Certification Authority will be appear in the list.
Actually the server must be running AD AS services so it needs to be a DC or Exchange box in order to select the Enterprise option.
@Richard
Wrong. To install an Enterprise CA all you need is an AD environment and the server that is going to server as a certification authority needs to be part of that domain. It’s not a must that you need to install certification services on a domain controller; you can, but it’s not a must. And one other thing, it does not need to be an Exchange server. You can run certificate services without an Exchange server in your environment.
@mahin
In your case there is some problem with your AD environment, or some restrictions apply.
hello
i follow the above senario
i have a problem with it !
when i wanna install active directory certificate servise in windows server 2008 r2 i’m not able to select enterprise because it is disable !!! what can i do?
this server is joined to a domain.
Maybe you have a broken AD environment or a Certification Authority already exist. I will check the second one first then do an AD investigation.